An attack on your crypto assets is inevitable: Slam the door shut on crypto theft.
Hackers and scams have been prevalent since the inception of crypto, but just how successful have they been and how have they evolved their tactics?
In 2008, the Federal Trade Commission recorded identity theft at the top complaint submitted by U.S. consumers. Now, these complaints have grown 20% higher and many involve mobile devices. Cybercrime is a booming criminal industry raking in nearly $1.5 trillion each year globally. You might also remember that in 2008 the Bitcoin Whitepaper was released, effectively creating a "purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution". Given the total market cap of cryptocurrencies was over $130.3 billion as of March 1st, 2019, it's no surprise that crypto assets are subject to the same kinds of attacks we've seen in the early days of mobile banking.
Hackers and scams have been prevalent since the inception of crypto, but just how successful have they been and how have they evolved their tactics? Research shows that in 2018 alone over $1.7 billion in cryptocurrency was stolen by hackers, which was more than triple that in the previous year. Of that number, "$950 million was stolen from exchanges and wallet providers while the other $725 million was taken through "inside jobs," including fraudulent ICOs, exit scams, staged exchange hacks, and Ponzi schemes" according to blockchain intelligence company Ciphertrace. Let's examine the evolution of crypto-jacking and derive lessons to protect ourselves moving forward.
History
From 2011 to today there have been numerous headlines about hacks and scam in the crypto industry. Each of the following is an example of crypto-jacking in recent history that highlights various tactics used by hackers and fraudsters.
Timeline
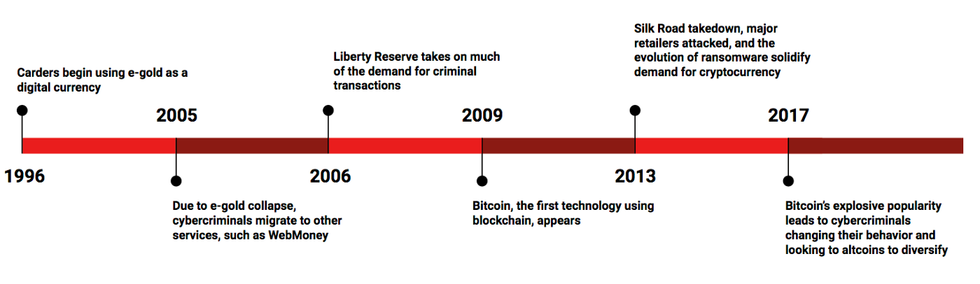
From 2011 to today there have been numerous headlines about hacks and scam in the crypto industry
2011
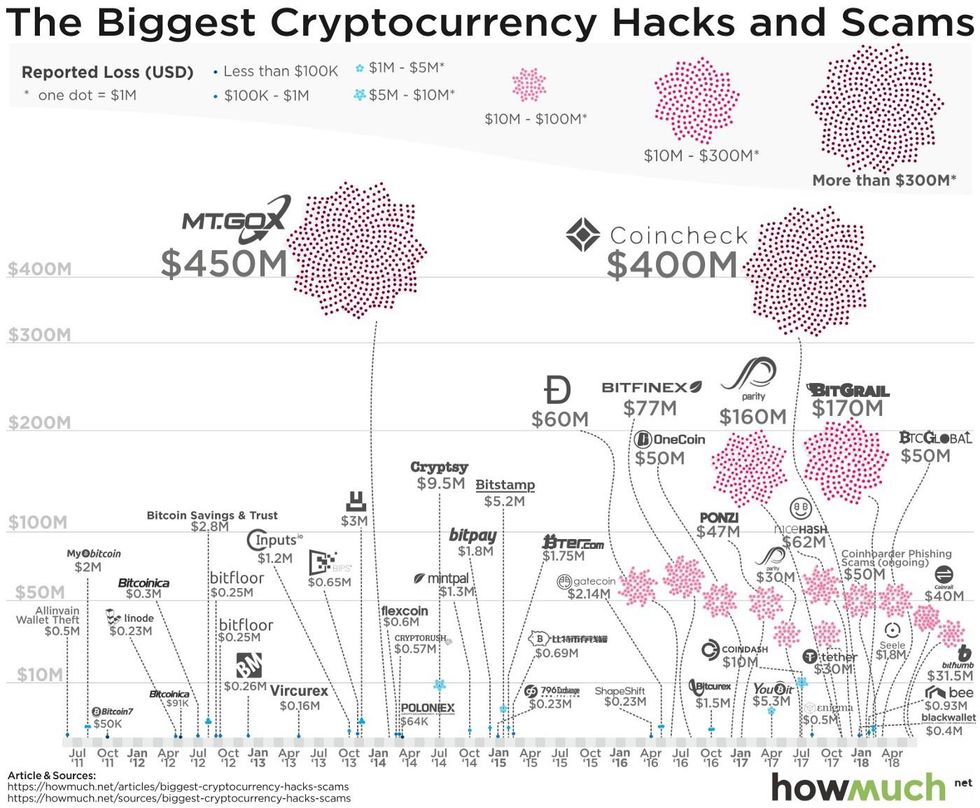
One of the first major cryptocurrency heists was the Mt. Gox hack, where $30,000 in Bitcoin was stolen. The computer of an auditor of the exchange was compromised by attackers who proceeded to manipulate the price of bitcoin on the exchange to one cent. The attackers then stole the private keys of Mt. Gox clients that were stored in hot wallets (wallets that are connected to the internet) and transfer out the Bitcoins at an artificially reduced price.
2012
In 2012, the Bitcoin Savings and Trust investment fund shuts down and is determined to be a fraudulent Ponzi Scheme a year later having robbed is investors of an equivalent to $2.8 million. In 2016, the culprit was sentenced 18 months in prison for a classic scam in an emerging medium of exchange.
2013
As cryptocurrencies became more mainstream, one Bloomberg anchor had a bitcoin gift card stolen directly from live TV after the anchor displayed a close up of the digital QR code used to claim the coins. All it took was a quick-witted viewer to whip out a phone and beat the newscasters to the punch.
2014
Yet again Mt. Gox is hacked, this time losing a total of 650,000 BTC. Unable to recover from the loss, all trading was stopped and the exchange filed for bankruptcy. The attacker was never identified, leaving other exchange vulnerable to attack.
2015
Thousands of Dark Web users see $12 million in Bitcoin disappear during the Evolution Marketplace exit scam. Deceitful folks eager to capitalize on the hype of the crypto movement are reaching all corners of the deep web.
2016
It's not just Bitcoin, any cryptocurrency and altcoins can be stolen without proper protection. In 2016, $60 million was lost in The DAO Attack. The DAO (Decentralized Autonomous Organization) is built on Ethereum that runs via a series of smart contracts and is governed by member voting. The purpose of The DAO was to collectively fund member projects, but instead, much of the funds were drained in code attack that exposed a loophole to allow the attacker to siphon out funds into a "child DAO". The thief was never caught.
2017
In an effort to bring price stability to cryptocurrencies, Tether released a coin that pegged one-to-one to the USD across exchanges, platforms, and wallets. In 2017 Tether announced the transfer of nearly $31 million to an unauthorized wallet. They also announced, however, that the stolen tokens would not be redeemable.
2018
Last year brought an onslaught of hacks targeted at exchanges. At the turn of the year, the price of Bitcoin skyrocketed and the popularity of crypto assets was at an all-time high. In the prior year, many exchanges and wallet providers all over the world raced to capture market share of crypto users, but many lacked necessary security measures and hackers became more savvy and determined. One such example is the Japanese crypto-exchange Coincheck which lost a whopping $400 million worth of crypto coins.
2019
Already early on in 2019, we see an interesting case in which QuadrigaCX, Canada's biggest cryptocurrency exchange, lost $150 million worth of crypto supposedly due to the death of the founder, who was the only person who knew the private keys. However, there are have been uncertainties raised about the case: did the founder fake his death? Is this a case of fraud? Or did poor contingency planning cause the funds to be simply inaccessible?
Threats
Despite more awareness about security, hackers outwitted operators, and some operators outwitted customers to commit fraud. From these examples over the last few years, we can examine some common ways crypto has been stolen and outright lost:
- THEFT: Traditional methods such as phishing, extortion, or fraud could subject you to identity theft.
- HACKS: A critical detail about a coordinated heist from is that most of the incidents regarding stolen crypto have a common theme: the digital assets were kept in exchanges.
- DEFECTS: Having your digital assets stolen is not the only way to lose money in the crypto world. Technical errors could cause funds to be locked up forever.
It is estimated that 20% of Bitcoin's supply is unrecoverable. The hard truth is there have always been and always will be thieves after your wealth, the only difference is theft now happens mostly in the digital space. Cybersecurity threats are on the rise and crypto owners are prime targets.
Although there are new solutions emerging, there will be tradeoffs between security standards and ease of use. Additionally, there are a few security fundamentals that will always hold true, ever when using offline wallets.
Prevention
Crypto is going to continue to be targeted, so if you want to HODL your crypto assets for the long run, it is imperative to adopt pro-active preventative measures. Firstly, don't leave your crypto anywhere that is connected to the internet. Second, don't trust centralized authorities (even if you don't believe them to be a hostile actor) with custody of your coins.
Instead, use common sense and apply basic security principles like a backup to a digital vault.
Hardware wallets are also a great option, but remember to keep track of it and choose memorable yet hard to guess PIN. Backup your private keys and recovery phrases — always.
Conclusion
We routinely store our cryptocurrency assets, for day-to-day use, in hardware/software wallets or in a centralized, online account. However, both of these approaches have significant weaknesses. In the case of wallets, if the owner loses the device, she risks permanent loss of all the assets. Wallet vendors provide 12/24-word passphrases as means of "last resort" backup. Owners store these passphrases as pieces of paper — sometimes in a bank safe deposit box, sometimes in a sock drawer. That is a pretty odd medium to use for the highest level of security for digital money. This approach not only shifts the risk of attack on keys into the recovery phrase, but it is also subject to a whole new set of risks — earthquakes, burglaries, mudslides and fires to mention a few factors in California alone. The paper passphrase, unfortunately, becomes an unacceptably risky single point of failure.
In the case of centralized online accounts, all of the account holders are at catastrophic risk when dedicated criminal hacker organizations target the online storage providers, which was the case with MtGox (2014), Bitstamp (2015), Bitfinex (2016) and Coincheck (2018). The delegation leaves users without direct ownership of their funds, negates one of the key principles of crypto assets and effectively forces users to fully trust a centralized storage vendor. That relegates crypto assets to same outdated setup as the legacy banking system.
As cryptocurrency investors start to invest in more and more coins, the number of accounts and wallets needed will also increase. Given the threat landscape, protecting cryptocurrency, whether for the short term or the long haul, is critical. A better solution is needed to prevent more high-profile hacks and the subsequent loss of assets — some of it irretrievably. Learn more about how Vault12 is changing the risk landscape with its digital custody app — now available (beta) vault12.com/getapp.
Written by Kyle Graden and Wasim Ahmad.
First published at vault12.com/blog.
An attack on your crypto assets is inevitable: Slam the door shut on crypto theft.
Hackers and scams have been prevalent since the inception of crypto, but just how successful have they been and how have they evolved their tactics?

Wasim Ahmad
Wasim Ahmad is a serial entrepreneur and an advisor in the fields of AI, blockchain, cryptocurrency, and encryption solutions. At Vault12, the pioneer of crypto inheritance, he led private and public fundraising efforts and focuses today on expanding the Vault12 ecosystem. In addition, he is a producer of the upcoming movie 'The Bitcoin Executor'.
His crypto experience began with AlphaPoint, where he worked with the founding team to launch the world's first crypto trading exchanges. Previously he was a founding member of Voltage Security, a spinout from Stanford University, that launched Identity-Based Encryption (IBE), a breakthrough in Public Key Cryptography, and pioneered the use of sophisticated data encryption to protect sensitive data across the world's payment systems.
He has also been very involved with regulatory initiatives in both the US and the UK, providing feedback to the SEC and FCA respectively pushing for expanded momentum for innovation and startups within the regulatory frameworks of both countries.
Wasim served on the board of non-profit, StartOut, and is a Seedcamp and WeWork Labs global mentor.
Wasim graduated with a Bachelor of Science in Physics and French from the University of Sussex.

Vault12
Vault12 is the pioneer in crypto inheritance and backup. The company was founded in 2015 to provide a way to enable everyday crypto customers to add a legacy contact to their cry[to wallets. The Vault12 Guard solution is blockchain-independent, runs on any mobile device with biometric security, and is available in Apple and Google app stores.
Vault12 is NOT a financial institution, cryptocurrency exchange, or custodian. We do NOT hold, transfer, manage, or have access to any user funds, tokens, cryptocurrencies, or digital assets. Vault12 is exclusively a non-custodial information security and backup tool that helps users securely store their own wallet seed phrases and private keys for the purpose of inheritance. We provide no legal or financial services, asset management, transaction capabilities, or investment advice. Users maintain complete control of their assets at all times.
You will lose your Bitcoin and other crypto when you die...
...unless you set up Crypto Inheritance today.
It's simple — if you don't worry about crypto inheritance, nobody else will — not your software or hardware wallet vendors, not your exchanges, and not your wealth managers. So it's up to you to think about how to protect the generational wealth you have created, and reduce the risks around passing that crypto wealth on to your family and heirs. What are the challenges with crypto inheritance?
- Crypto Wallets are difficult to use and do not offer crypto inheritance management. In fact, most of them tell you to write down your seed phrase on a piece of paper, which is practically useless.
- Some people back up their wallet seed phrases or private keys on paper, local devices like hardware wallets or USBs, or in the cloud. All of these options have severe drawbacks that range from hacking to accidental loss to disrupted cloud services.
- Software wallets operate on specific blockchains, yet your crypto assets span multiple blockchains. For inheritance to work, you must be able to manage inheritance across every blockchain — now and forever.
Pioneering Crypto Inheritance: Secure Quantum-safe Storage and Backup
Vault12 is the pioneer in Crypto Inheritance, offering a simple yet powerful way to designate a legacy contact and pass on your crypto assets—like Bitcoin (BTC), Ethereum (ETH) and Solana (SOL) —to future generations. Built for everyday users yet robust enough for the most seasoned crypto enthusiasts, Vault12 Guard ensures your wallet seed phrases and private keys are preserved in a fully self-sovereign manner, across all Blockchains.
At the heart of Vault12 Guard is quantum-resistant cryptography and a decentralized, peer-to-peer network of trusted Guardians. Your critical information is never stored in the cloud, on Vault12 servers, or even on local devices—dramatically reducing the risk of a single point of failure. By fusing a powerful software layer with the Secure Element of iOS devices (Secure Enclave) and Google devices (Strongbox), Vault12 Guard locks down your private keys against present and future threats.
Our innovative approach harnesses social recovery, enabling you to appoint one or more trusted individuals or mobile devices as Guardians. These Guardians collectively safeguard your protected seed phrases in a decentralized digital Vault—so there’s no need for constant lawyer updates or bulky paperwork. Should the unexpected happen, your chosen legacy contact can seamlessly inherit your crypto assets without compromising your privacy or security.
Preserve your digital wealth for generations to come with Vault12 Guard—the simplest, most secure way to manage crypto inheritance and backup.
Take the first step and back up your crypto wallets.
Designed to be used alongside traditional hardware and software crypto wallets, Vault12 Guard helps cryptocurrency owners back up their wallet seed phrases and private keys (assets) without storing anything in the cloud, or in any single location. This increases protection and decreases the risk of loss.
The first step in crypto Inheritance Management is making sure you have an up-to-date backup.
The Vault12 Guard app enables secure decentralized backups, and provides inheritance for all your seed phrases and private keys across any blockchain, including Bitcoin, Ethereum, and others, and for any crypto wallet.
Note: For anyone unfamiliar with cryptocurrencies, Vault12 refers to wallet seed phrases and private keys as assets, crypto assets, and digital assets. The Vault12 Guard app includes a software wallet that works alongside your Digital Vault. The primary purpose of this is to guard your Bitcoin (BTC) and Ethereum (ETH) wallet seed phrases, private keys, and other essential data, now and for future generations.