Overview
How Secure Enclave gives you Instant Access to your Digital Assets with Hot Storage Vault
Vault12 Guard's Instant Access Hot Storage enables secure local storage of digital assets such as crypto and NFTs with immediate on-device retrieval, and safeguards them from loss by backing them up in your digital Vault.
Have you ever wanted to access your digital assets instantly, but also be sure that they are fully protected?
Do you ever worry about what would happen to your digital assets if your phone were stolen or lost?
Do you want to reduce the time it takes to access assets in your digital Vault?
The dilemmas of phone security
When we started Vault12 in 2014, mobile phones were pretty insecure: all one needed was a USB cable to download the contents of any phone. Internal phone storage was not a secure location for high-value digital assets, so we designed Vault12 from the ground up to implement robust storage security for these early insecure phones.
Since then, phone security has dramatically improved - first thanks to pioneering work from Apple on iPhone and iOS, and more recently in Google Android phones.
The two biggest innovations that have enabled robust security on phones are:
- The Secure Enclave - cutting-edge technology with its own separate tamper-proof processing unit, memory, and operating system making it extremely hard to get unauthorized access to native cryptographic keys stored inside.
- Biometric Authentication - Apple also pioneered FaceID that is fully controlled by the Secure Enclave at the hardware level, which means even if iOS itself is compromised on your phone, it doesn't give attackers any ability to trick FaceID and unlock the security enclave.
The Secure Enclave approach has been extended across all of Apple's devices, and Cloud vendors have also started implementing the same security architecture to protect sensitive data in the cloud.
With these capabilities setting new standards for device security in both Apple and Google ecosystems, Vault12 can now leverage these hardware innovations to provide simple, instant access to locally-stored digital assets - all while providing a robust, distributed, decentralized social recovery backup that is the hallmark of the Vault12 Guard Cryptostorage platform.
What is the Secure Enclave?
The Secure Enclave is a dedicated secure subsystem integrated into Apple systems on chip (SoCs). The Secure Enclave is isolated from the main processor to provide an extra layer of security, and is designed to keep sensitive user data secure even if the Application Processor kernel becomes compromised.
The Secure Enclave makes it close to impossible for hackers to decrypt sensitive information remotely, and also extremely hard even if they illegitimately gain full physical access to your device (in case of loss or theft). Because the Secure Enclave is a separate system, and because the phone's operating system never actually sees the decryption keys, it's incredibly difficult to decrypt your data without knowing your PIN code.
The risk factor for the Secure Enclave is PIN codes - if your pin code is easy to guess, or simple enough to brute force, losing your phone might eventually lead to other parties getting access to your phone's data days or months later. Keep that in mind generally while deciding what assets should be included in "hot storage" access on your phone - but Vault12 does not rely on the PIN capability of Secure Enclave, in order to prevent such risks from affecting you.
Third-party apps such as Vault12 Guard can also create and store strong cryptographic keys in the enclave to lock down data, but the apps never have access to the keys themselves. Instead, apps make requests for the Secure Enclave to encrypt and decrypt data. This means any information encrypted using the Secure Enclave is incredibly difficult to decrypt on any other device.
When you store a private key in the Secure Enclave, you never actually handle the key, making it difficult for the key to become compromised. Instead, you instruct the Secure Enclave to create the key, securely store it, and perform operations with it. You receive only the output of these operations, such as encrypted data or a cryptographic signature verification outcome.
Many attempts have been made to hack the Secure Enclave, however, none have succeeded in remotely retrieving anyone's keys.
In 2017 a hacker was able to decrypt the Secure Enclave firmware. However he was unable to gain access to any private keys, so there was no actual exploit.
In 2020 a well-known group of Chinese hackers discovered an "unpatchable" exploit on the Secure Enclave chip used by older Apple devices. While it is unclear what was possible with this specific vulnerability, direct access to the physical phone was required to conduct a hack. Apple has already fixed the security breach in A12, A13 and M1 chips.
More details on Apple's Security architecture is available in its annual Platform Security Guide.
What is Biometric Authentication: FaceID?

Biometric authentication relies on technical sensors that allow you to prove that you are who you say you are using attributes that are unique to each human being. Examples include retina scanning, fingerprint scanning, and facial recognition. Apple has been at the forefront of research and implementation of the facial authentication known as FaceID.
Security & Privacy Features:
- Face ID data is encrypted with a key that is only available to the Secure Enclave. This data is regularly updated to record changes in your appearance. This data is used to train a neural network in order to enhance the effectiveness of your authentication.
- Face ID data does not leave your device, and is not backed up to the iCloud. Supported applications that use Face ID for authentication are only notified about whether the login was successful. Apps can not access the Face ID data associated with your enrolled face.
Since your FaceID data never leaves your phone, and is natively stored inside your phone's hardware, it means that hackers cannot "spoof" your face by hacking into a cloud biometric data server and pretending to be you to unlock your keys.
How good is Security on Android Phones?
Security on Android smartphones has historically been below the standard set by iPhones. Even when top Android manufacturers started introducing secure hardware in their devices, the lack of Android platform standards led to a highly-variable array of software, secure architecture approaches, and eventually, to many bugs.
After years of evolution and in response to market needs, Google introduced a tamper-resistant hardware enclave called Titan M which enables tamper-resistant key storage for Android apps, using StrongBox.
StrongBox is an implementation of the Android Keymaster API, which resides in a hardware security module used in Android devices. With this security enhancement standard, Google paved the way for Android devices with secure elements to reach a unified security level across the industry, and to implement features that were previously impossible, like secure applets, across the Android ecosystem - not just by a single manufacturer.
The downside, however, is that these capabilities are fairly new, and not all models of Android smartphones yet support this high level of security. Google Pixel 4 and newer, and Samsung Galaxy Series 20 and newer support StrongBox, and hopefully, many more devices by a variety of major Android manufacturers will too, thanks to Google's initiatives.
Biometrics (Touch/FaceID) on Android phones also still varies by manufacturer, and it is challenging to judge the security of those varying implementations across the industry in a consistent way.
Future uses of StrongBox
StrongBox and tamper-resistant hardware are becoming important requirements for emerging user features, including:
- Digital keys (car, home, office)
- Mobile Driver's License (mDL), National ID, ePassports
- eMoney solutions (for example, Wallet)
All of these features must be run on tamper-resistant hardware in order to protect the integrity of sensitive resources like application executables, user data, and encryption keys.
In order to accelerate the adoption of these new Android use cases, Google has formed the Android Ready SE Alliance. SE vendors are collaborating with Google to create a set of open-source, validated, and ready-to-use SE Applets. StrongBox for SE is qualified and ready for use by Google's OEM partners and currently available from Giesecke+Devrient, Kigen, NXP, STMicroelectronics, and Thales.
You can visit the Android Security and Privacy developer site for more info.
Introducing Hot Storage Vault powered by Secure Enclave
As security on Apple's phone has improved and evolved, Vault12 has combined these innovations with its Cryptostorage platform and the Vault12 Guard app to ensure that any files that you want to have readily available locally are encrypted by the Secure Enclave chip, and can only be decrypted with FaceID.
The best part is that these files that you select for secure local storage are still backed up to your Vault, so it becomes much, much simpler for you to access the files that you need often, and you are not at risk even if you lose your phone.
Local copy is the latest capability of Hot Storage for digial Vault owners that makes the storage of digital assets more convenient whilst still protected by the highest available security. It enables you to designate specific assets to be encrypted with an extremely secure cryptographic key generated inside the Secure Enclave locally on your iPhone.
The asset is always available when needed without the need to contact your Guardians - however, it is also backed up in your Vault just like your other assets, so if your phone is lost or stolen, a full Vault recovery is still possible by contacting your Guardians
Existing assets that are already in your Vault can be made available via Local copy by temporarily unlocking them. Should you want your assets to only be available via your distributed Guardians, you can also remove the Local copy of asset at any time. You are always in control of your assets.
This new capability is super-convenient for frequently-used assets like a BitClout seed phrase (which is frequently required when logging in or logging out), or seed phrases for wallets that you log into from many devices.
Local copy is available in the latest release of iOS and Android versions of Vault12.
The Vault12 Guard "Local Copy" feature in Action
Let's see the "Local Copy" hot storage Vault in action in Vault12 Guard. If you do not yet have a digital Vault, see our guide on setting up digital assets in your personal Vault.
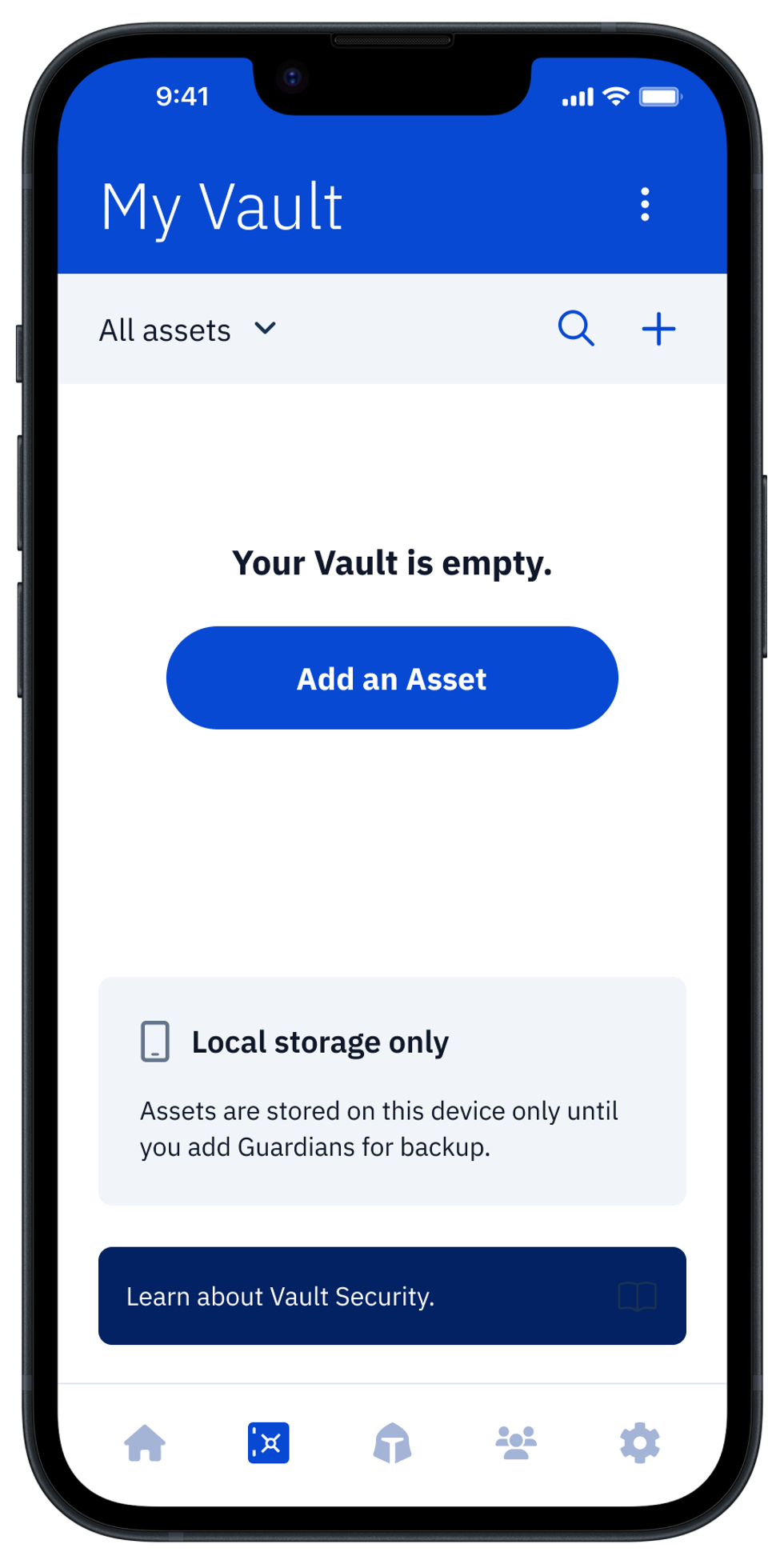
1. Open your Guard Digital Vault
Open Vault12 Guard to view your Vault and digital assets. Select "Add an Asset." For this example, we will choose the options "NFTs," and then "Add Media" to choose a piece of NFT art on your filesystem.
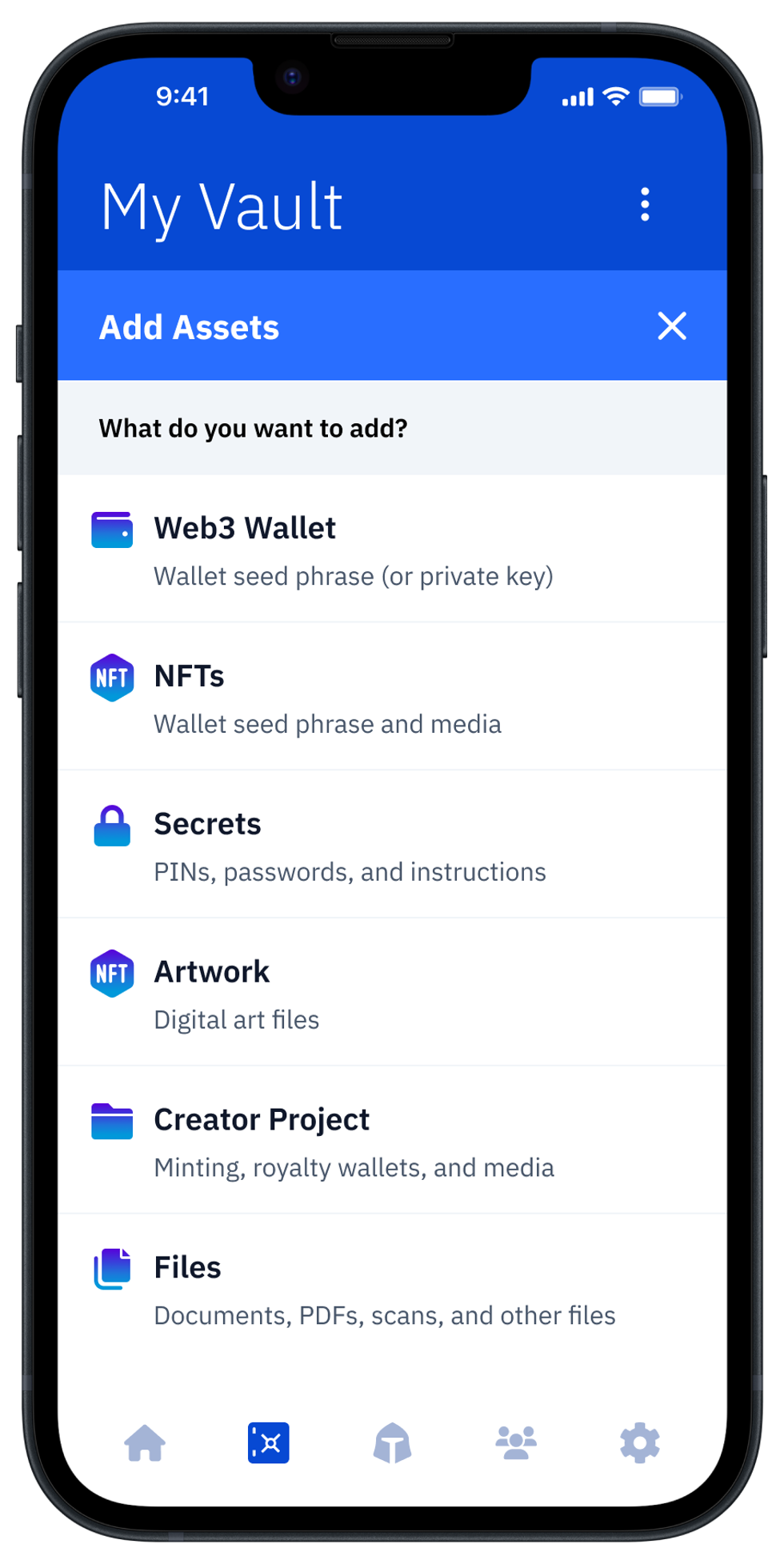
2. Add your Asset to Guard
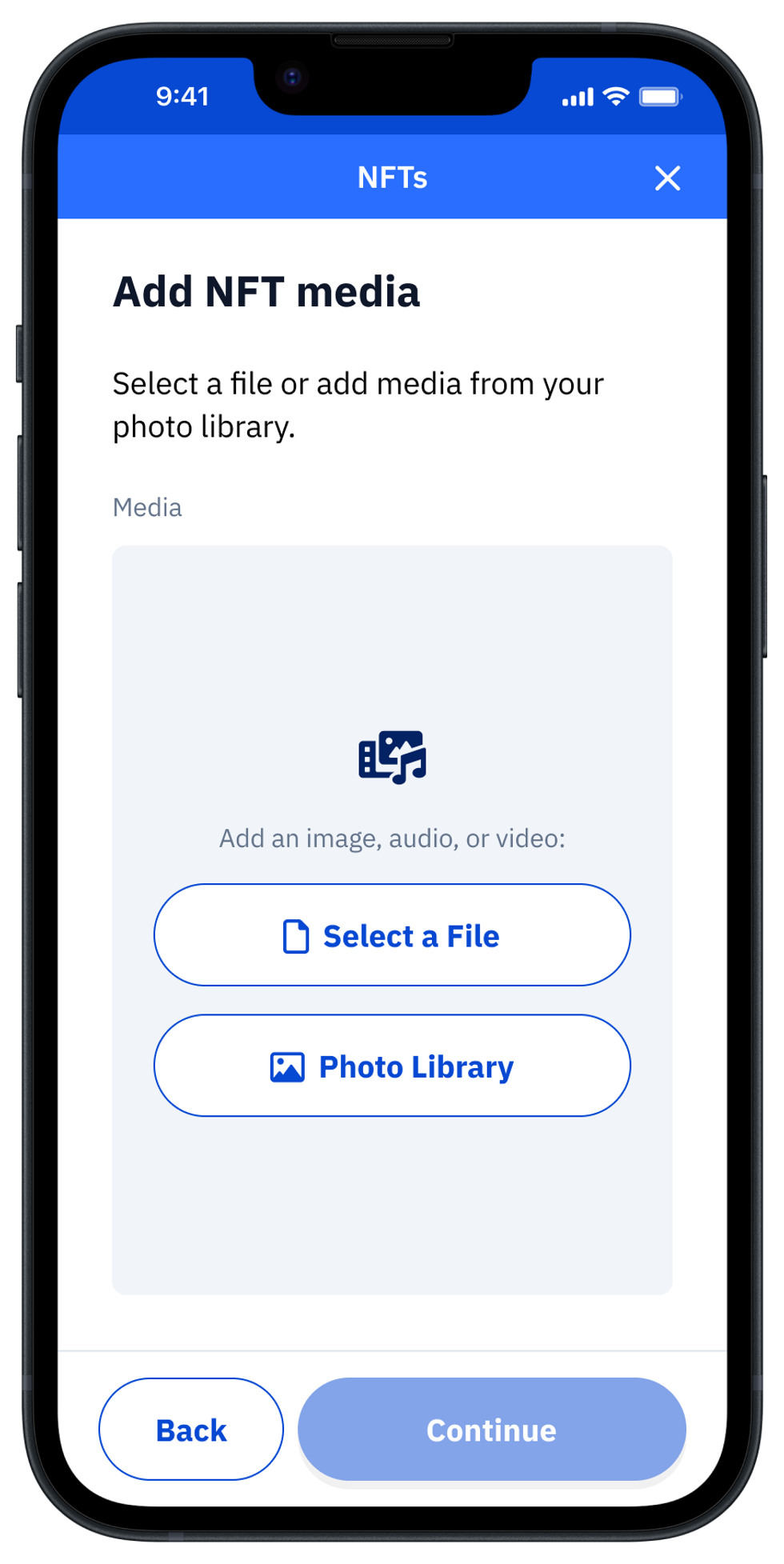
Select the asset to store.
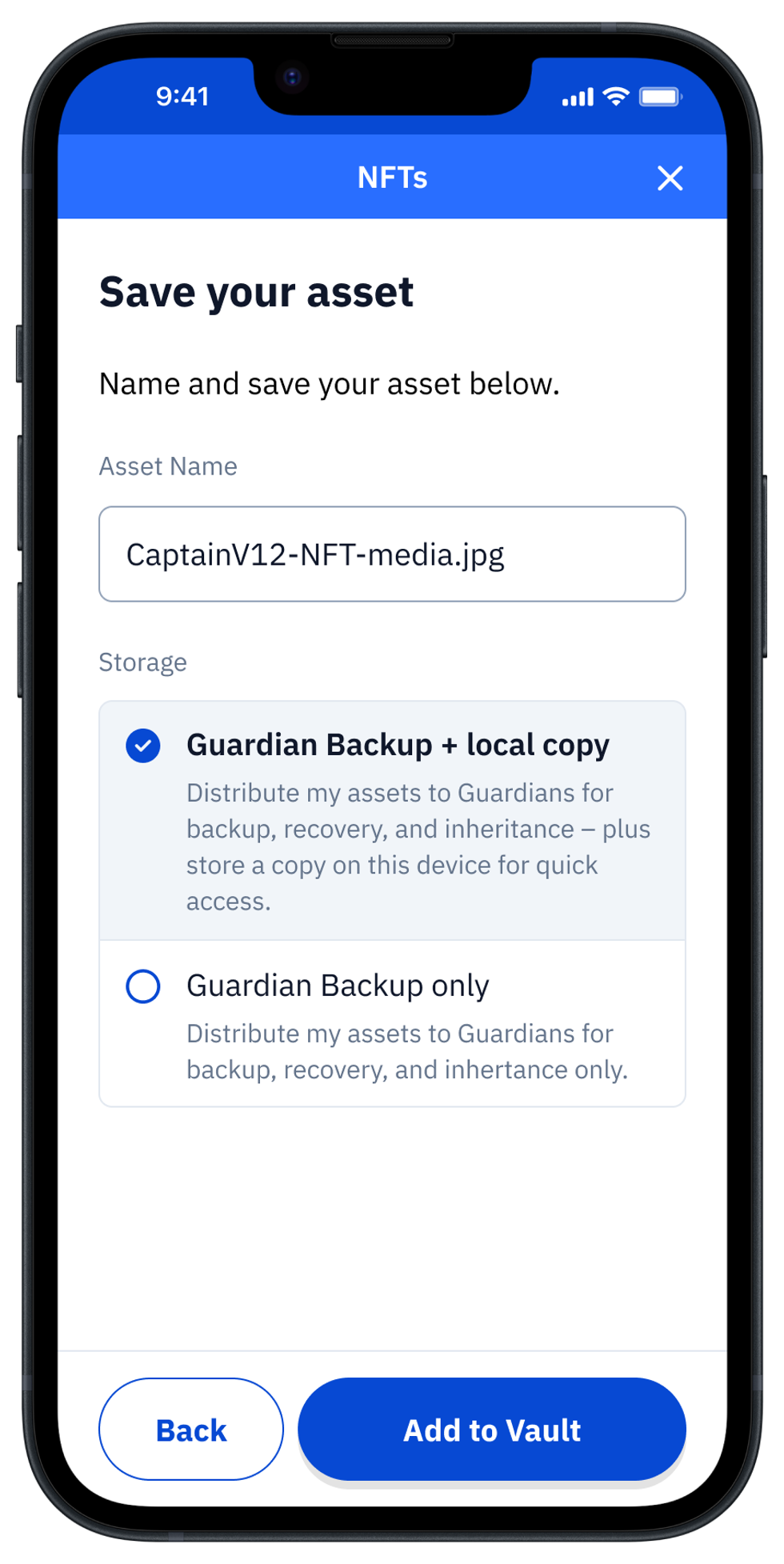
To utilize hot storage for instant access to the asset in the future, tick the " + local copy" option. Give it a name and press Add to Vault.
The digital asset will now be encrypted and then distributed to your Guardians.
3. Lock your Asset in Guard
During this process, encrypted shards of your asset are sent to your Guardians. Feel free to contact your Guardians to ensure that they receive the backup shards. This will ensure that your assets and Vault are protected in the case of loss or theft.
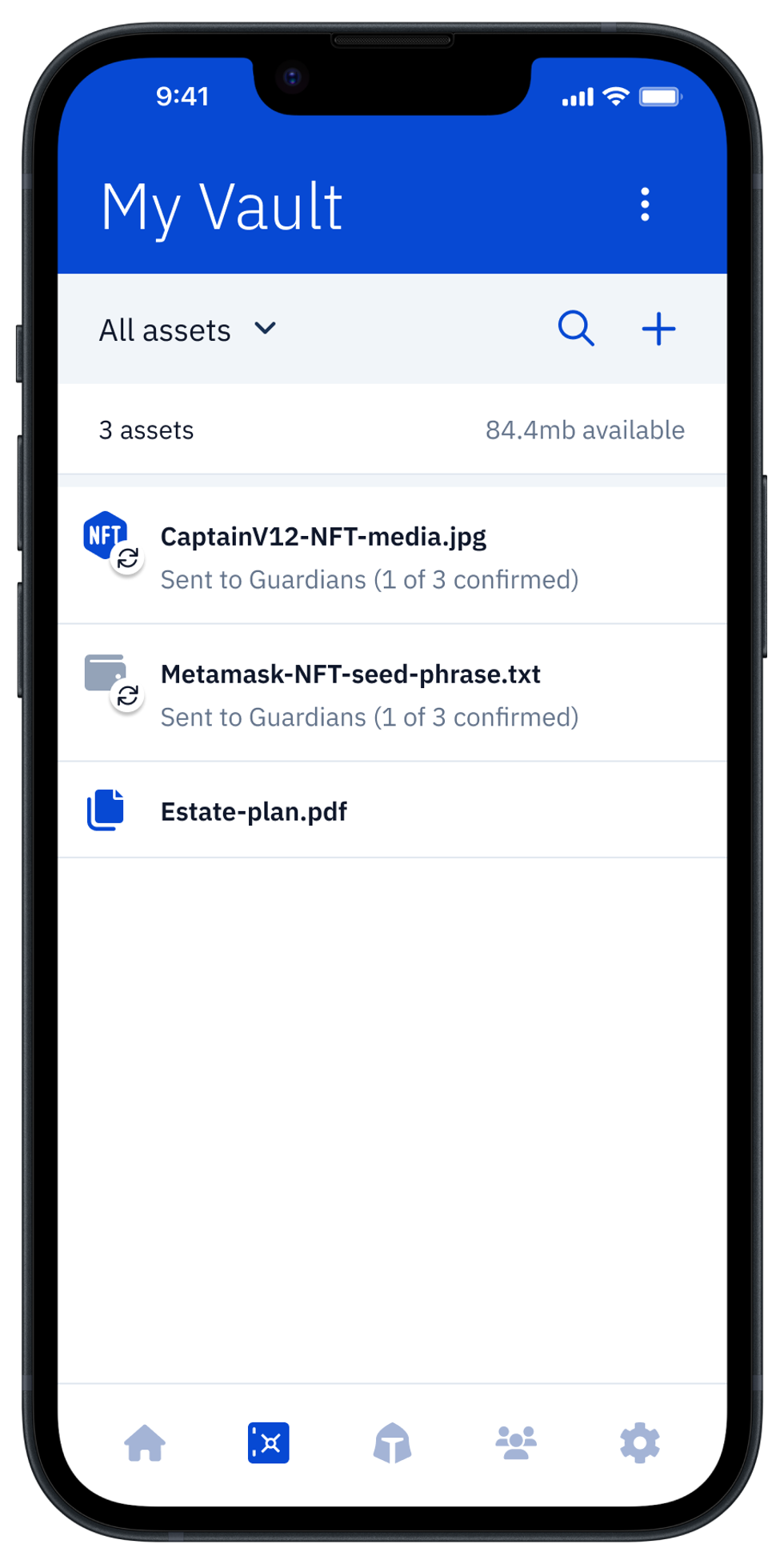
4. Instantly retrieve your digital asset in Guard
Once your assets have been synchronized with your Guardians, you can click to view them. For regular assets, your Guardians will need to confirm. For assets tagged for local storage, you can instantly view the asset after biometric authentication with FaceID.


You can download Vault at https://vault12.com/download.
Table of Contents
- The dilemmas of phone security
- What is the Secure Enclave?
- What is Biometric Authentication: FaceID?
- How good is Security on Android Phones?
- Future uses of StrongBox
- Introducing Hot Storage Vault powered by Secure Enclave
- The Vault12 Guard "Local Copy" feature in Action
- 1. Open your Guard Digital Vault
- 2. Add your Asset to Guard
- 3. Lock your Asset in Guard
- 4. Instantly retrieve your digital asset in Guard

