Which is a better wallet: Ledger Nano X or Exodus?
Consider both your short-term needs and the long-term protection of your assets
When choosing crypto wallets, many users base their decisions on day-to-day asset management needs and perceived wallet or device security. However, savvy crypto users first consider a wallet's ability to handle long-term security scenarios.
Long-term security includes expected essentials like backup and recovery tools, and often-overlooked features related to secure and fault-proof third-party recovery. Wait, what's third-party recovery? You can think of third-party recovery as your ability to allow crypto assets to be inherited by successors. All crypto investors should have a comprehensive security strategy for the full life cycle of their crypto assets.
Let's begin by helping you understand the pros and cons of the Ledger Nano X hardware wallet and the Exodus software wallet for day-to-day activities, as well as considering their ability to safeguard the long-term security of your assets.
Overview
The Ledger Nano X and Exodus wallets both provide a wide variety of features and support a broad spectrum of cryptocurrencies, making them suitable for diverse crypto portfolios.
At a high level, several differences are clear:
Ledger Nano X
- Form: A hardware wallet, with mobile-centric usability via Bluetooth.
- General Usability: User-friendly (with necessary trade-offs due to its more-robust security features).
- Design: Compact and durable. The de facto standard for securing transactions on desktops.
- Price Point: It's not free, like software wallets are.
Exodus
- Form: A software wallet, available in both mobile and desktop versions.
- General Usability: Easy to use, and has particularly well-reviewed customer support.
- Design: Built-in exchange features and a moderate number of integrations.
- Price Point: The wallet software is free; the company makes money on exchange services provided through the wallet.
The decision between the two will likely hinge on individual preferences for target security requirements, preferred platforms (mobile or desktop), and should take into account the planned frequency of use.
Approach to comparison
Now, let's have a closer look.
When choosing the best hardware wallet for cryptocurrency security, you may wonder not only which is better, the Ledger Nano X or the Exodus, but also:
- What happens if your wallet is lost or stolen? (How well can these wallets recover from user errors?)
- How do these wallets handle more advanced scenarios like inheritance of crypto assets?
- How easy to use are these wallets?
- How do their security features compare?
This article compares important characteristics for these two popular wallets. We’ll break down the strengths and weaknesses of each, focusing on security, ease of use, and backup and recovery methods. By the end of this comparison, you’ll clearly understand which wallet is right for you, as well as how to recover your crypto assets in case of accidents.
What happens if your wallet is lost or stolen?
Wise wallet owners recognize the critical importance of crypto recovery before they find themselves in an unexpected bind! That's why it's important to understand the fundamental topic of crypto asset longevity, including features such as backup, recovery, and inheritance for crypto assets. These considerations are central to long-term planning.
Technical security is essential, but in the world of crypto, the degree to which backup and recovery solutions are foolproof for users is at least equally important. Here are the backup and recovery options for these two wallets:
Ledger Nano X | Exodus | |
Backup & Recovery methods | Recommends Recovery Seed Phrase be written on paper, or engraved onto metallic plates. | Recommends Recovery Seed Phrase be written on paper, or using iCloud or Google Account saving it along with your everyday passwords. |
Optional paid subscription | Ledger Recover, a centralized 3rd-party cloud service, highly criticized by the crypto community. Clouds are not safe — especially when operated by multiple 3rd parties. | No. |
How do these wallets handle Crypto Inheritance?
Crypto Inheritance Features
Currently, most crypto wallets, including the Ledger Nano X and Exodus, lack any features for establishing and managing crypto inheritance. This gap presents a challenge for users who want to be sure that their crypto assets can be transferred to their heirs.
Ledger Nano X | Exodus | |
Backup |
- Written only | - Written only |
Inheritance | No | No |
Decentralized backup with Vault12 | Yes | Yes |
Inheritance Management with Vault12 | Yes | Yes |
Backup and recovery differentiators
Ledger Nano X Recover service Disadvantages:
- The optional Ledger Recover backup service is a paid service provided by three corporations that each hold parts of the user’s seed phrase in a cloud. This introduces risks, as the seed phrase could potentially be accessed via subpoena; or business partners could terminate agreements or become involved in lawsuits that result in locked data or resources (like, for example, Gemini and Genesis). These scenarios contain multiple potential points of failure.
- Very important detail: The terms of the optional Ledger Recover service do not mention support for inheritance, meaning any unfortunate accident related to the user could make crypto assets unrecoverable for his or her successors. Ledger itself suggests using 3rd-party crypto inheritance services for those purposes.
Ledger Nano X Recover service Advantages:
- People have different preferences. If a user is comfortable trusting a bank with their assets, they might also feel confident using Ledger Recover for securing their seed phrase backup (even though Ledger is not providing the entire cloud backup solution).
Exodus backup Disadvantages:
- Exodus has a cloud backup feature that comes with similar security assumptions and risks as all other passwords stored in your cloud provider. It is not recommended to rely on cloud backups for significant crypto balances.
Exodus backup Advantages:
- Exodus does offer a one-click solution for backup for insignificant balances of crypto.
How easy are these crypto wallets to use?
Let's compare the key aspects of both wallets side by side, and then summarize what really stands out for user convenience:
Ledger Nano X | Exodus | |
Display |
1” Monochrome OLED, | Full smartphone screen |
Input interface | 2 click buttons | Full smartphone screen |
Cable | USB-C | n/a |
Wireless | Bluetooth | As smartphone |
Platforms | macOS, Windows, Linux, Android, iOS, Browser Extension (3rd party) |
iOS, Android, Browser Extension |
3rd party wallets and dapps support | MetaMask, Exodus + 28 more | Ledger, Trezor |
Password manager & 2FA | FIDO2 2FA & Passkeys, Password Manager | n/a |
Product size & weight | 72 x 19 x 12 mm / 34g | - |
Convenience features | Battery (Up to 5 hours in use) | Exchange support |
Number of supported coins | 5,500+ | 200+ |
Price | $149 | $0 |
Crypto wallet user experience (UX) differences

Ledger Nano X with Smartphone UX
Ledger Nano X Disadvantages:
- The display is literally the size of a coin: very uncomfortable to use.
- Requires two-handed operation, making it difficult to use with a phone simultaneously — contrary to some misleading ads.
- The buttons are stiff, making operations cumbersome.
Ledger Nano X Advantages:
- Offers Bluetooth connectivity — works with or without a cable, at least with smartphones.
- Wide support for third-party wallets and dapps, allowing the Ledger Nano X to sign transactions directly in MetaMask, Uniswap, and other platforms without relying on Ledger Live software. This is a huge advantage for DeFi users.
Exodus UX Disadvantages:
- As a product that prioritizes ease of use, Exodus does not offer a full suite of advanced features such as fiat currency on/off ramps or advanced Web3 / DeFi integrations.
- The desktop version of Exodus offers more features than the mobile version (e.g., portfolio management tools, Trezor hardware integration, and a broader set of supported cryptocurrencies).
Exodus UX Advantages:
- Exodus is generally more user-friendly than the Ledger Nano X (and other hardware wallets).
How do these wallets' security features compare?
Now, we dive deeper into the core specification of every hardware wallet: security features.
| Ledger Nano X | Exodus | |
| PIN-code | 4 - 8 digits | up to 6 digits |
| BIP39 Passphrase | Yes | No |
| Open-source | Partial | Partial |
| Secure Element | Yes | No |
| Multisignature | Yes | No |
Crypto wallet security feature differentiators
Ledger Nano X security Disadvantages:
- Some critical components are closed-source. This raises concerns, especially after the controversial introduction of the Ledger Recover backup service, which challenged the previous assumption that the Secure Element could never transmit the recovery seed phrase outside the hardware wallet.
Ledger Nano X security Advantages:
- Includes a Secure Element, giving Ledger devices a strong reputation for withstanding physical attacks. This is important for users who prefer not to complicate their security with BIP39 passphrases, prioritizing ease of use.
Exodus security Disadvantages:
- Portions of the Exodus wallet are closed-source, preventing full transparency of its code security.
- Exodus, like all software wallets, operates in an inherently less-secure operating environment than a hardware wallet.
- As a software wallet, Exodus lacks a Secure Element.
- Exodus lacks support for some common security extensions such as 2-factor authentication, creation of multisignature transactions, and entry of a wallet "extra word" passphrase.
Exodus security Advantages:
- Some of Exodus's security disadvantages could be mitigated by using Exodus together (integrated) with Ledger Nano X (they are compatible with each other).
Summary of Ledger Nano X and Exodus Comparison
The Ledger Nano X and Exodus both provide a respectable set of features, and support a broad spectrum of cryptocurrencies, making them suitable for diverse crypto portfolios.
The Ledger Nano X is a mobile-friendly, security-oriented solution, and offers a balance of security and convenience features. It provides a small display and uncomfortable input, but with the advantages of a Secure Element and wireless connectivity options like Bluetooth.
On the other hand, Exodus is free and simple, but provides fewer security capabilities. It's great for beginning users and suitable for relatively small amounts of crypto.
The decision between the two will likely hinge on individual preferences for the target use case and balance, and should take into account the planned frequency of use.
Given their convenient integration, the best of all worlds could be to use both wallets, holding larger amounts of crypto in your Ledger Nano X wallet while keeping a small, ready-to-transact "petty cash" stash in your Exodus wallet.
Whichever you choose, remember to add crypto inheritance to your choice of wallet to ensure the long-term safety of your digital assets.
Vault12 Guard: a decentralized solution for Crypto Inheritance
Vault12 is the pioneer in Crypto Inheritance Management, and delivers an easy-to-use and secure method for assigning a legacy contact to your crypto wallets. This enables you to pass on your wallet seed phrases and private keys for all types of digital assets to future generations. Vault12 Guard is designed for everyday people, yet strong enough for Crypto OGs.
Vault12 Guard has a uniquely-secure design. Utilizing advanced encryption and decentralized storage, it ensures that crypto assets are not only safe but also transferable under predefined conditions, filling a critical need unmet by most traditional hardware wallets. Vault12 Guard applies a hybrid approach of software fused with the hardware-based Secure Element of phone devices (The Secure Enclave for iOS devices, and Strongbox for Google devices). Vault12 Guard's decentralized design reduces possible points of failure. Nothing is stored on cloud servers or Vault12 servers, and no assets are stored on local devices, making them less of a target.
From a user perspective, the Vault12 Guard app asks users to appoint one or more people (or mobile devices) as Guardians. The designated Guardians are entrusted to protect the user's comprehensive collection of wallet seed phrases and private keys, which are safely stored within a decentralized digital Vault. Its simple, user-friendly workflow removes the necessity for regularly revising wallet inventories or modifying instructions for your lawyers — a process that otherwise could lead to privacy breaches.
Both the Ledger Nano X and Exodus are compatible with Vault12 Guard Inheritance. This addresses the seed phrase backup dilemma for any hardware wallet. It also makes less-secure backup methods, such as paper or steel plates, unnecessary.
Stablecoins' momentum builds in bridging traditional and digital assets
Include stablecoins in your digital recovery and inheritance plans
There is a lot of buzz about stablecoins. So what are they, should you have some, and how should you protect them if you do have some?
First, let's review what they are: stablecoins are blockchain-based tokens that are designed to act as stable forms of value. Their prices are synchronized to predictable external assets, such as stable currencies. But unlike currency, which can be slow to deploy or move (whether physically or via a bank electronic transaction), stablecoins instantly can be transferred or exchanged for a huge array of digital assets.
Given their stable value, stablecoins have a unique place in the crypto world: unlike more-volatile cryptocurrencies, they act as low-risk intermediaries between digital assets and other traditional forms of value.
And even though their role is intermediary, they could be held for short periods of time, or long ones. Let’s consider why so many people and institutions buy stablecoins — and sometimes hold them for long periods of time.
What are the most common use cases for stablecoins?
There are many ways that people and institutions use stablecoins:
As a mechanism for exchange between other forms of value: Some people buy stablecoins for just a short period of time to support making another transactions: for example, it may be necessary to buy stablecoins when moving fiat currency to or from a centralized exchange, or converting between two different types of cryptocurrencies if there is no direct exchange possible between them. A huge market that uses stablecoins as a medium of exchange is International remittences.
As a store of wealth: Stablecoins offer a more stable form of wealth preservation than holding cash in a country with high inflation or an otherwise-volatile currency (e.g., Argentina and Turkey).
As liquidity: Stablecoins provide ready-to-deploy financial liquidity that can be used to quickly participate in DeFi opportunities or trade for other cryptocurrencies when time is of the essence (without needing to slog through slow fiat on-ramps).
As loan collateral to avoid a taxable crypto sale: By borrowing stablecoins against their crypto assets on DeFi, holders can utilize their capital or spend some proceeds without selling crypto assets — thereby avoiding the tax consequences of a sale.
As an investment that bears yields: Stablecoins can be used to earn yield (this typically requires allowing an exchange or DeFi platform to “lock” them).
As a low-risk hedge relative to other investments: Stablecoins can be used to reduce risk as part of a balanced digital portfolio.
Stablecoins and investment risk
If you are considering investing in stablecoins, remember that:
- If you let a centralized exchange hold the keys to your coins, you are subject to third-party risks related to trusting the company, their security, and their financial health. (Remember, "Not your keys, not your coins.") Understand how to manage your keys.
- If you hold your own keys and invest via DeFi, you are subject to the risks of associated smart contracts having bugs, vulnerabilities, or otherwise behaving in unexpected ways.
Nothing is risk-free in life, especially in investing. Choose the levels and forms of risks that you are comfortable with as appropriate for your situation.
How did stablecoins evolve?
When cryptocurrencies like Bitcoin, Ethereum, and altcoins first joined the financial scene, their extreme volatility made them high-risk, speculative investments. Most coins have rollercoaster price periods! Stablecoins were introduced as a way to buffer that volatility.
But a few kinks had to be worked out first: some early attempts to build stablecoins failed because their price was not as stable as the issuers had planned. Specifically, algorithmic stablecoins, which were meant to hold a stable value based on mathematical algorithms, smart contracts, and modeled market behaviors, did not always perform as expected.
For example, the algorithmic stablecoin TerraUSD spectacularly failed in May 2022 due to faulty assumptions in the design of the algorithm about market behavior in response to unexpected events. As a result of several failed algorithmic stablecoins, these days, algorithmic stablecoins have lost much of their initial popularity.
Modern stablecoins
Most stablecoins today are backed by real-world assets (collateral), such as currency, government treasury bonds, cryptocurrencies (sufficiently over-collateralized to buffer against volatility), or baskets of commodities. Confidence is improved when tangible assets back up digital coins, not just trust in the behavior of a "pegging" algorithm.
Transparency, maturity, and regulatory acceptance all lead to increased use of stablecoins. Today's largest stablecoins have made leaps and bounds towards achieving each of those ends. Reflecting this evolution, stablecoins have been making up an increasing share of on-chain transactions — more than half of all crypto transactions — as the following chart demonstrates.
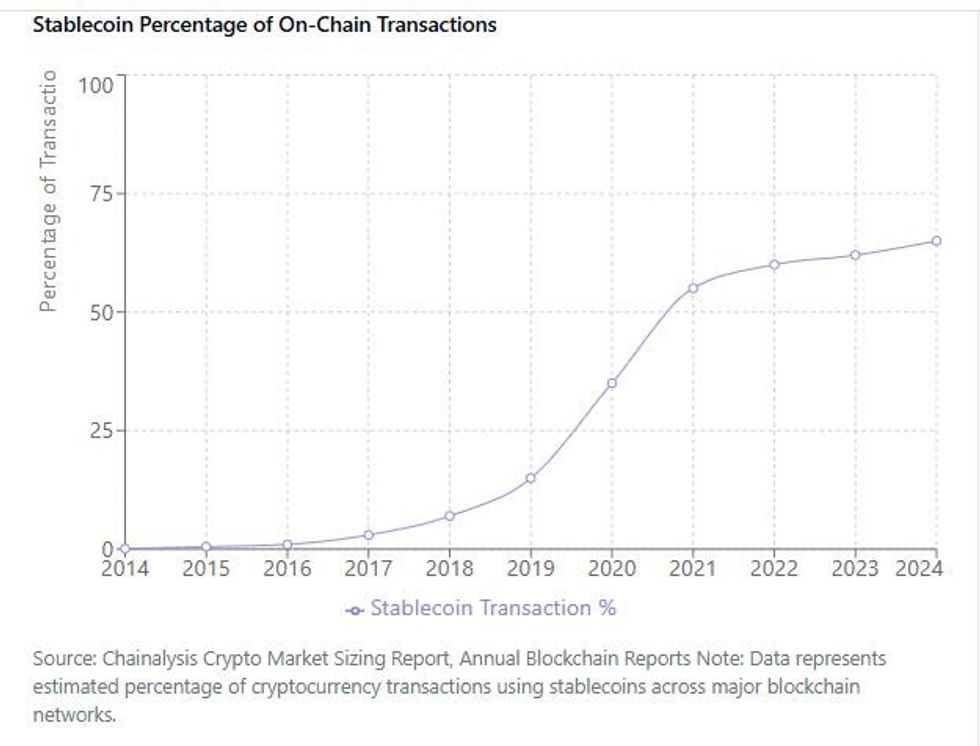
Chainalysis via Claude.ai
Stablecoin successes
Several collateralized U.S. Dollar stablecoins from private corporate issuers have matured and gained popular acceptance. Among them, descending by market capitalization:
- USDT ("Tether"), from Tether
- USDC ("USDC Coin"), from Circle (until 2023, issued by the Centre Consortium, founded by both Circle and Coinbase)
- PYUSD ("PayPalUSD"), from Paxos Trust Company
- RLUSD ("Ripple USD"), from Ripple
According to the "State of Stablecoins in 2025" report by Dune and Artemis, Tether shows stablecoin leadership in volume and market penetration with a $146 billion market cap, while USDC Coin, with a $56-60 billion market cap, excels in institutional adoption and DeFi usage, driven by its regulatory compliance and on-chain activity.
If you'd like a deep dive into the differences between USDT and USDC, we recommend Coin Bureau's insightful comparison.
What financial institutions issue or transact in stablecoins?
Crypto exchanges and stablecoin issuers necessarily hold large quantities of stablecoins, but did you know that many other major financial institutions are moving into the use of stablecoins as well? Institutions like Visa, Bank of America, and Revolut are using or piloting projects to issue and accept selected stablecoins as part of their service packages and partnerships. Even Fidelity Investments is testing their own stablecoin.
How is the United States handling stablecoins?
The United States is undergoing a sea change in its stablecoin appetite, having issued new guidance in March 2025 permitting banks to engage in both crypto custody and certain stablecoin activities. And the Guiding and Establishing National Innovation for U.S. Stablecoins Act of 2025 (“GENIUS Act”), which describes a broader range of stablecoin guidance, is quickly approaching finalization as law. Further, the U.S. Treasury Secretary Scott Bessent has even announced plans to leverage stablecoins backed by U.S. Treasury bills to bolster the dollar's position as the world's dominant reserve currency.
Regulatory clarity for stablecoins is happening fast, which reduces risks for all users.
How can you protect the stablecoins in your digital wallet?
If you hold stablecoins in a digital wallet, you should include them in a secure wallet backup and an inheritance plan just as you would for your other digital assets. Don’t put off thinking about the possibility of wallet access disruptions, or about your digital inheritance.
- Back up your wallet seed phrase so that you can restore your wallet if you ever lose access to it. A decentralized Digital Vault is the most effective place to safeguard your digital assets.
- Think about who your digital asset beneficiary or beneficiaries should be, and plan your digital inheritance.
- You could also choose to keep your Centralized Exchange passwords in your Vault12 Digital Vault, as well as any other related passwords. A Digital Vault is more secure than a standard password manager.
"Failing to plan is planning to fail."— Benjamin Franklin
Vault12 Guard can protect all of the digital assets that you hold
The Vault12 Guard Digital Vault can protect the stablecoins and all other digital assets in your wallets. See how easy it can be for you to protect your digital wealth in a decentralized way using your personal choice of Vault Guardians. Simply and conveniently protect all of your digital assets today in your own Digital Vault. When you’re ready, take it a step further to secure the future of your digital wealth with Vault12 Digital Inheritance.
Ledger Stax and Trezor Model T: two strong wallets compared
The right wallet for you depends on your usage patterns and design preferences
When choosing hardware wallets, many crypto users base their decisions on day-to-day asset management needs and perceived device security. However, savvy crypto users first consider a wallet's ability to handle long-term security scenarios. Long-term security includes expected essentials like backup and recovery tools, and also often-overlooked features related to secure and fault-proof third-party recovery. You can think of third-party recovery as your ability to allow crypto assets to be inherited by successors. Successful crypto users require a comprehensive security strategy for the full life cycle of crypto assets. This article will help you achieve that.
Let's jump into helping you understand the pros and cons of the Ledger Stax and Trezor Model T for day-to-day activities, as well as their potential to safeguard the long-term security and longevity of your assets.
Overview
The Ledger Stax and Trezor Model T both provide a wide variety of reliable security features and support a broad spectrum of cryptocurrencies, making them suitable for diverse crypto portfolios. However, several differences are clear:
Ledger Stax
- Mobile-Centric Usability: Designed with mobility in mind, the
- Ledger Stax features wireless connectivity options like Bluetooth and
- NFC, making it highly compatible with mobile platforms.
- Premium Design: Its unconventionally large display enhances readability, though it comes with slower responsiveness included.
- Price Point: Positioned as a premium product, its cost reflects its advanced features and sleek design
Trezor Model T
- Mobile-Centric Usability: No Bluetooth connectivity. iOS app is view-only.
- General Usability: Smaller set of wallets, coins, and apps.
- Design: The touchscreen and input are very well-thought-out experiences.
- Price Point: More affordable.
In terms of crypto asset longevity features, such as backup, recovery, and crypto inheritance, both devices provide industry-standard and proprietary options with certain trade-offs, as well as compatibility with third-party solutions like Vault12 Guard for succession planning scenarios.
The decision between the two will likely hinge on individual preferences for the target platform (mobile or desktop), and should take into account the planned frequency of use.
Approach to comparison
When choosing the best hardware wallet for cryptocurrency security, you may wonder:
- Which is better, the Ledger Stax or the Trezor Model T?
- How easy to use are these wallets?
- How do their security features compare?
- Do these wallets have vulnerabilities, and have they been hacked?
- What happens if your wallet is lost or stolen?
- How do these wallets accomodate user errors, and complex scenarios like inheritance of crypto assets?
This article compares important characteristics for these two popular wallets. We’ll break down the strengths and weaknesses of each, focusing on security, ease of use, and backup and recovery methods.
By the end of this comparison, you’ll clearly understand which wallet is right for you, as well as how to recover your crypto assets in case of accidents.
What happens if your wallet is lost or stolen?
Wise wallet owners recognize the critical importance of crypto recovery before they find themselves in an unexpected bind! That's why it's important to understand the fundamental topic of crypto asset longevity, including features such as backup, recovery, and inheritance for crypto assets. These considerations are central to long-term planning.
Technical security is paramount, but in the world of crypto, the degree to which backup and recovery solutions are foolproof for users is at least equally important. Here are the backup and recovery options for these two wallets:
Ledger Stax | Trezor Model T | |
Backup & Recovery methods | Recommends Recovery Seed Phrase be written on paper, or engraved onto metallic plates. | Recommends Recovery Seed Phrase be written on paper, or engraved onto metallic plates. |
Optional paid subscription | Ledger Recover, a centralized 3rd-party cloud service, highly criticized by the crypto community. Clouds are not safe — especially when operated by multiple 3rd parties. | No. |
How do these wallets handle Crypto Inheritance?
Crypto Inheritance Features
Currently, most hardware wallets, including the Ledger Stax and Trezor Model T, lack any features for establishing and managing crypto inheritance. This gap presents a challenge for users who want to be sure that their crypto assets can be transferred to their heirs.
Ledger Stax | Trezor Model T | |
Backup |
- Written only | - Written only - Manual sharing of shards |
Inheritance | No | No |
Decentralized backup with Vault12 | Yes | Yes |
Inheritance Management with Vault12 | Yes | Yes |
Backup and recovery differentiators
Ledger Stax Recovery service Disadvantages:
- The optional Ledger Recover backup service is a paid service provided by three corporations that each hold parts of the user’s seed phrase in a Cloud. This introduces risks, as the seed phrase could potentially be accessed via subpoena; business partners could terminate agreements or become involved in lawsuits that result in locked data or resources (like, for example, Gemini and Genesis); and there are multiple potential points of failure.
- Very important detail: The terms of the optional Ledger Recover service do not mention support for inheritance, meaning any unfortunate accident related to the user will make crypto assets unrecoverable for his or her successors. Ledger itself suggests using 3rd-party crypto inheritance services for those purposes.
Ledger Stax Recovery service Advantages:
- People have different preferences. If a user is comfortable trusting a bank with their assets, they may also feel confident using Ledger Recover for securing their seed phrase backup (even though Ledger is not providing the complete cloud backup solution).
Trezor Model T backup Disadvantages:
- Trezor has a Multishare backup service, but it is fully manual, and challenging to maintain. The user is responsible for generating, distributing, and keeping track of the encrypted shards.
Trezor Model T backup Advantages:
- Trezor does offer a Multishare backup option for those who are able and willing to set it up.
How easy are these crypto wallets to use?
Let's compare the key aspects of both wallets side by side, and then summarize what really stands out for user convenience:
Ledger Stax | Trezor Model T | |
Display | 3,7” black and white E Ink, |
1.54" Color LCD, |
Input interface | Touchscreen | Touchscreen |
Cable | USB-C | USB, MicroSD card slot |
Wireless |
Bluetooth 5.2, | No |
Companion Apps | macOS, Windows, Linux, Android, iOS |
macOS, Windows, Linux, Android |
3rd party wallets and dapps support | 50+ | 9+ |
Password manager & 2FA | FIDO2 2FA & Passkeys, | FIDO2 2FA |
Product size & weight | 85 x 54 x 6 mm / 45g | 64 x 39 x 10 mm / 22g |
Convenience features |
Battery (10 hours of use), | Magnetic dock |
Number of supported coins | 5,500+ | 1,600+ |
Price | $399 | $149 |
Crypto wallet user experience differences

User holding a mobile phone and using Ledger Stax as FIDO U2F security key
Ledger Stax Disadvantages:
- The display has a noticeable response delay due to the "E Ink" touchscreen technology, and could be irritating.
- Not all apps are ported to Stax yet. Even the native Passwords app still has no release date identified as of this article's publish date, so check in advance whether your favorite network/coin is supported.
- Extremely expensive. The value in Stax is more about design, rather than practical aspects.
Ledger Stax Advantages:
- Huge informative display and "Clear Signing" allows you to review and confirm all transaction details directly on Ledger Stax and in a human-readable language before they are signed and sent. This enhances security and ensures that you see exactly what you are approving in a secure and tamper-proof manner.
- Offers Bluetooth connectivity as well as NFC — works with or without a cable, at least with smartphones.
- Wide support for third-party wallets and dapps, allowing the Ledger Stax to sign transactions directly in MetaMask, Uniswap, and other platforms without relying on Ledger Live software. This is a huge advantage for DeFi users.
Trezor Model T Disadvantages:
- No wireless connectivity: you always have to use a cable.
- iOS is a balance view-only app, so you can't send transactions from iOS.
Trezor Model T Advantages:
- The display is much more convenient to work with on a regular basis, and easy to read.
- The touchscreen and input are very well-thought-out experiences on Trezor Model T — you can use it without any discomfort.
How do these wallets' security features compare?
Now, we dive deeper into the core specification of every hardware wallet: security features.
| Ledger Stax | Trezor Model T | |
| PIN-code | 4 - 8 digits | up to 50 digits |
| BIP39 Passphrase | Yes | Yes |
| Open-source | Partial | Full |
| Secure Element | Yes | No |
| Multisignature | Yes | Yes |
Crypto wallet security feature differentiators
Ledger Stax security Disadvantages:
- Critical components like the Secure Element and its operating system are closed-source. This has raised concerns, especially after the controversial introduction of the Ledger Recover backup service, which challenged the assumption that the Secure Element could never transmit the recovery seed phrase outside the hardware wallet.
Ledger Stax security Advantages:
- Includes a Secure Element, giving Ledger devices a strong reputation for withstanding physical attacks. This is important for users who prefer not to complicate their security with BIP39 passphrases, prioritizing ease of use.
- Clear Signing is also a security feature.
Trezor Model T security Disadvantages:
- Lacks a Secure Element, making it resistant to physical attacks only if a BIP39 passphrase is used. This is a significant drawback in both convenience and its ability to be fault-proof.
Trezor Model T security Advantages:
- Fully open-source software and hardware. This minimizes third-party risks, and avoids any need to rely on trust.
- Allows for longer PIN codes, which might appeal to particularly cautious users.
Have there been vulnerabilities or hacks of these wallets?
There have been vulnerabilities and hacks associated with both the Ledger and Trezor products, however given Stax is very new we will cover it's manufacturer's hacks history.
Far from delivering uncompromised security, these wallets are routinely subject to malware, supply chain, and firmware vulnerabilities. Here are some recent notable incidents:
Ledger Vulnerabilities:
- The Connect Kit Attack (2023): The Connect Kit breach was discovered by the security teams of Ledger.
- Ledger User Data Breach (2020): A major data breach exposed the personal information of thousands of customers, leading to phishing attacks.
- Another User Data Breach (2021): Ledger announced on Twitter that it has been targeted by rogue Shopify team members who exported over 200 merchants’ customer databases.
- Ledger Live (2020): Users were exposed to basic double spending attacks, amplified double spending attacks, and DoS attacks without user consent.
- Potential Supply Chain Attack Vulnerability (2020): Kraken Security Labs Identifies Supply Chain Attacks Against Ledger Wallets.
Trezor Model T Vulnerabilities:
- Ability to Physically Hack Trezor T Wallet (2023): Crypto Security Firm Unciphered Claims Ability to Physically Hack Trezor T Wallet
- Five Reported Vulnerabilities in Two Models of Trezor Hardware Wallets (2019): Ledger’s Attack Lab has found five vulnerabilities in hardware wallets of its direct competitor Trezor.
- Kraken Identifies Critical Flaw in Trezor Hardware Wallets (2020): Kraken Security Labs has devised a way to extract seeds from both cryptocurrency hardware wallets offered from industry leader Trezor, the Trezor One and Trezor Model T.
Summary of Ledger Stax and Trezor Model T Comparison
The Ledger Stax and Trezor Model T both provide a respectable set of security measures, and support a broad spectrum of cryptocurrencies, making them suitable for diverse crypto portfolios.
The Ledger Stax is very mobile-friendly, and offers a balance of security and convenience features at a very premium price. It offers a big, but unconventional display and with delayed input, but with the advantages of a Secure Element and wireless connectivity options like Bluetooth.
On the other hand, the Trezor Model T, at a much lower price, boasts a fully open-source framework, larger display with colors, and touchscreen interface for enhanced user interaction, but with reduced security and convenience from not having a Secure Element and working only with USB connections the offer sounds non-attractive.
The decision between the two will likely hinge on individual preferences for the target platform (mobile or desktop), and should take into account the planned frequency of use.
Whichever you choose, remember to add crypto inheritance to your choice of wallet to ensure the long-term safety of your digital assets.
Vault12 Guard: a decentralized solution for Crypto Inheritance
Vault12 is the pioneer in Crypto Inheritance Management, and delivers an easy-to-use and secure method for assigning a legacy contact to your crypto wallets. This enables you to pass on your wallet seed phrases and private keys for all types of digital assets to future generations. Vault12 Guard is designed for everyday people, yet strong enough for Crypto OGs.
Vault12 Guard has a uniquely-secure design. Utilizing advanced encryption and decentralized storage, it ensures that crypto assets are not only safe but also transferable under predefined conditions, filling a critical need unmet by most traditional hardware wallets. Vault12 Guard applies a hybrid approach of software fused with the hardware-based Secure Element of phone devices (The Secure Enclave for iOS devices, and Strongbox for Google devices). Vault12 Guard's decentralized design reduces possible points of failure. Nothing is stored on cloud servers or Vault12 servers, and no assets are stored on local devices, making them less of a target.
From a user perspective, the Vault12 Guard app asks users to appoint one or more people (or mobile devices) as Guardians. The designated Guardians are entrusted to protect the user's comprehensive collection of wallet seed phrases and private keys, which are safely stored within a decentralized digital Vault. Its simple, user-friendly workflow removes the necessity for regularly revising wallet inventories or modifying instructions for your lawyers — a process that otherwise could lead to privacy breaches.
Both the Ledger Stax and Trezor Model T are compatible with Vault12 Guard Inheritance. This addresses the seed phrase backup dilemma for any hardware wallet. It also makes less-secure backup methods, such as paper or steel plates, unnecessary.
Vault12 is NOT a financial institution, cryptocurrency exchange, or custodian. We do NOT hold, transfer, manage, or have access to any user funds, tokens, cryptocurrencies, or digital assets. Vault12 is exclusively a non-custodial information security and backup tool that helps users securely store their own wallet seed phrases and private keys for the purpose of inheritance. We provide no legal or financial services, asset management, transaction capabilities, or investment advice. Users maintain complete control of their assets at all times.
Basics
Learn about how the risks of holding cryptocurrency are different than those of traditional investments, and how to move ahead with confidence and safety.
View all articlesDeath and Taxes… Why Tax Time Is the Perfect Time to Fix Your Crypto Inheritance
In this world nothing can be certain except Death and Taxes
“In this world nothing can be said to be certain, except death and taxes.”
Benjamin Franklin wrote that in 1789. If he were alive today, he’d probably add a third certainty:
If you don’t plan your digital inheritance, a good chunk of your wealth will simply vanish.
Every year, tax season forces us into the same ritual: pull together documents, log into accounts, reconcile statements, and finally see—clearly—what we actually own.
That’s exactly why tax time is the single best moment to get your crypto and digital inheritance sorted out. You’re already doing the hard part: creating an inventory of your assets. All you need to do is extend that thinking one step further:
“If I got hit by the proverbial bus tomorrow… who could access this, and how?”
Let’s walk through how to turn your yearly tax chore into a quiet act of love for your future heirs.
The Hidden Superpower of Tax Season: Asset Inventory
Most people think of taxes as punishment, not a planning tool. But when you look at what you actually do each year, it’s powerful:
- You list employers and income sources
- You gather bank and brokerage statements
- You track gains, losses, and cost basis
- You note property, side gigs, investments, and loans
In other words: you build a living snapshot of your financial life.
That snapshot is exactly what your heirs and executor will need one day. The gap is that:
- It usually lives in your head, scattered in email, or dumped into a folder called “2025 Taxes.”
- It rarely includes your digital footprint or crypto assets in a structured way.
So tax time becomes this moment where you almost have everything needed for a great inheritance plan—but then you hit “submit,” breathe a sigh of relief, and bury the work for another year.
Most people think of taxes as punishment, not a planning tool. But when you look at what you actually do each year, it’s powerful:
- You list employers and income sources
- You gather bank and brokerage statements
- You track gains, losses, and cost basis
- You note property, side gigs, investments, and loans
In other words: you build a living snapshot of your financial life.
That snapshot is exactly what your heirs and executor will need one day. The gap is that:
- It usually lives in your head, scattered in email, or dumped into a folder called “2025 Taxes.”
- It rarely includes your digital footprint or crypto assets in a structured way.
So tax time becomes this moment where you almost have everything needed for a great inheritance plan—but then you hit “submit,” breathe a sigh of relief, and bury the work for another year.
The Missing Column: Your Digital and Crypto Assets
Traditional estate planning is still stuck in a world of:
- House
- Bank accounts
- Brokerage
- Retirement accounts
- Insurance
But your actual life now includes:
- Bitcoin, Ethereum, and other tokens
- NFTs and digital art
- Assets on DeFi platforms and L2s
- Staked assets and yield strategies
- Exchange accounts (even the “small” ones you forgot about)
- Password managers
- Encrypted notes and backups
- 2FA apps and hardware keys
- Cloud storage with important documents, photos, and IP
For your heirs, the hardest part is not taxes—it’s discovery and access:
- Discovery – “What did they have, and where is it?”
- Access – “How do we unlock it without their passwords and keys?”
Without answers to those two questions, a perfectly legal, well-structured estate still leaks value. With crypto, “leaks” usually means “gone forever.”
The Brutal Truth: Estate Law Can’t Recover a Lost Private Key
With traditional finance, losing a password is annoying but fixable:
- There’s a helpdesk.
- There’s KYC.
- There’s a paper trail.
With crypto, if your heirs don’t have:
- The seed phrase
- The private key
- The social recovery method
- Or the hardware wallet PIN + recovery
…then the assets are effectively burned.
Death certificates, probate orders, and court documents mean nothing to a blockchain. The network doesn’t know you died; it only knows valid signatures.
That’s why crypto inheritance must be designed in advance, at the same level of care you put into optimizing your tax bill.
Turning Tax Prep Into Inheritance Prep: A Simple 6-Step Ritual
You don’t need to become a lawyer or a security engineer. You just need to add a few extra steps to what you’re already doing each year.
1. Expand Your Asset Inventory to Include Digital
While you’re gathering statements and logging into platforms for tax reporting, create one master inventory that includes:
- All exchanges you use (even “test” accounts with small balances)
- All wallets (hardware, mobile, browser, paper)
- All major on-chain positions (staking, DeFi, L2s, NFTs)
- Any custodial platforms (CeFi yield platforms, centralized staking, etc.)
- Critical digital services:
- Password manager(s)
- Cloud storage that contains important docs
- Domain registrars, app store accounts, creator platforms (where there’s IP or revenue)
Treat this like a crypto & digital asset schedule to sit alongside your traditional tax and estate documents.
2. Label the “Where” and the “How”
For each item in your inventory, add two simple pieces of information:
- Where is it?
- Exchange name, wallet type, protocol, or chain
- How is it secured?
- Hardware wallet, seed phrase in a safe, multi-sig, social recovery, etc.
You’re not putting the actual secrets in this list—just the map, not the keys.
Think of it like this: if you weren’t around, could your executor at least know which hills to dig under?
3. Decide Who Should Ultimately Inherit What
Estate planning sounds technical, but at core it’s emotional:
- Who do you want to benefit from your Bitcoin, ETH, or NFTs?
- Are there assets that are more meaningful to specific people—e.g., digital art, ENS names, in-game assets, or creator royalties?
- Do you want a portion of your crypto to go to a foundation, DAO, or non-profit?
You can formalize distribution wishes in:
- Your will
- A letter of wishes
- A separate digital asset memo that your executor knows about
The key is that tax time already has you thinking in percentages and allocations—just extend that mindset one step into “what if I wasn’t here next year?”
4. Establish a Secure Way to Pass On Secrets (Without Sharing Them Now)
This is the biggest practical challenge:
How do you make sure your heirs can access your keys only when they’re truly supposed to?
Some approaches people use:
- Multi-sig wallets where one key is held by a trusted person or entity
- Shamir’s Secret Sharing or other threshold schemes, where parts of a secret are split among multiple “guardians”
- Dedicated crypto inheritance tools that combine encryption, sharding, and social recovery
- Estate-aware password manager plans, where a trusted contact can gain access after a verified event
What you don’t want to do is:
- Put seed phrases directly in a will (it becomes public in probate in many jurisdictions)
- Email your seed phrase to yourself or someone else
- Put everything in a single safe that no one even knows exists
The ideal pattern is:
Your inventory and intentions are discoverable,
your keys and instructions are recoverable but strongly protected,
and the whole system doesn’t depend on any one person’s memory.
5. Document “How to Use This” in Human Language
Your heirs might not be crypto-native. They might be terrified of doing something wrong.
So along with your technical plan, add a plain-English guide:
- “If I’m gone, here’s who to contact first.”
- “Here’s where to find the inventory of my accounts and wallets.”
- “These people/platforms have pieces that can help unlock access.”
- “Before moving anything, get a reputable crypto-savvy lawyer or advisor to help.”
- “Do not share seed phrases in email, text, or random websites promising recovery.”
You can think of this as the “Meet Joe Black” note to your future self and your family—the part the lawyers and accountants usually skip, but the humans desperately need.
6. Make It an Annual Habit: “Death and Taxes Day”
Finally, turn this into a ritual.
Once a year—when you do your taxes:
- Update your asset inventory (including new wallets, protocols, or accounts).
- Check that your inheritance mechanism (social recovery / Shamir / multi-sig / tool of choice) still works and still involves the right people.
- Revise your instructions and wishes if relationships or holdings have changed.
You don’t need to obsess over it all year. Just pair it with something you’re legally forced to do anyway.
If death and taxes are unavoidable, you might as well hijack tax day to make death a little less chaotic for the people you love.
Why This Matters More Each Year
Every year:
- More of your net worth migrates from the physical world to the digital one.
- More platforms, protocols, and wallets come into your life.
- More of your story—photos, messages, creations, IP—lives behind encrypted logins.
Failing to plan doesn’t just mean your family may pay more tax.
In the digital world, it means they may never even know what’s missing.
A thoughtful crypto and digital inheritance plan is:
- A financial decision (don’t burn assets by neglect)
- A security decision (don’t leak secrets prematurely)
- And above all, a love decision (don’t leave a puzzle no one can solve)
Tax season hands you the raw material for this plan every year. The next step is simply deciding:
“This is the year I stop pretending I’ll live forever—and I make sure my digital life is as well-organized for my heirs as it is for the tax office.”
If you’d like, I can now:
- Add a short intro blurb about Vault12 / your product as the “how” piece
- Turn this into a shorter LinkedIn version or an email newsletter
- Or create a 5-point checklist graphic you can use as a lead magnet: “Turn Tax Time Into Crypto Inheritance Time”
Where there's a Will, there's a way
How to protect your Digital Legacy
Many topics in life are difficult to discuss. Uncomfortable truths are often more easily brushed aside and ignored than discussed. The reality is that this doesn’t fix the issue. Although it can be difficult, it is essential to have open and honest conversations, especially with those closest to you. Being on the same page when it comes to these tough conversations often results in much better overall outcomes than ignoring them and hoping they go away.
One topic of particular difficulty for families to discuss is inheritance. The reasons for this are obvious. Nobody wants to think about losing their loved ones. It is one of the most painful experiences in this life. Not wanting to endure it more than one already has to in one lifetime is a completely understandable mindset.
The problem becomes that without a plan, families often find themselves in all sorts of predicaments that arise due to a lack of planning. Without having the conversation, children often don’t know what they even stand to inherit from their parents. When an inheritance comes as a surprise, it is even more difficult to know what to do with it.
Where there's a Will, there's a way
If you have never had a discussion with your core family about an inheritance plan, you probably aren’t super keen to start discussing their or your untimely demise over a casual dinner.
One major reason that people don’t set a plan is that inheritance doesn’t come up easily in conversation. It is simpler not to make others uncomfortable, as well as not to address the uncomfortable truth of one’s own mortality. Furthermore, unless someone has had the experience of having someone close to them pass away before, they likely don’t have the context for how the process of distributing assets to next of kin works and why it is so important to create a plan.
The law surrounding what happens to assets without a legally binding will from the deceased varies from one country to another, but the process of claiming assets without a will is messy at best, no matter where you go. The assets can end up getting tied up for months, sometimes years, and there are instances of people not inheriting their loved one’s wealth at all due to the lack of a will naming them the heir.
Willing assets to next-of-kin is already a painful enough process without having to combat outside parties, including the possibility of your own government, to obtain what you should have been rightfully entitled to from your loved one. As painful as it can be to think about losing a loved one, creating a legally binding will is a great first step to ensuring that there is some type of plan that can be carried out should the unthinkable happen.
Stick to the Plan
In addition to the grief that comes from losing a loved one, there are a great deal of practical expenses that come up when someone passes away. Ideally, these things are already covered through some plan in the will, allowing those closest to the departed to grieve instead of frantically coming up with thousands to cover end-of-life expenses while they’re in distress from losing their loved one to begin with.
Even with a will, there is no guarantee that the recipient of this windfall of assets is going to know what to do with them. The first step is to ensure that while expenses are covered, the family doesn’t transition their grief into a massive spending spree from receiving a windfall of assets. In many instances, inheritance is the largest individual wealth increase that a person will experience in their life, and it can be overwhelming to suddenly have significantly more money and borrowing power at your fingertips.
Fortunately, the ability to immediately access assets can vary greatly, depending on the liquidity of the asset class being inherited. It is not simple to turn around and sell a home, for example, but it can be fairly easy to unload stocks, bonds, and crypto, given the liquidity of the market. Avoiding the pitfall of liquidating everything is a step that many struggle with, and it isn’t easy to accomplish on your own, especially given the severity of emotions in this moment of life.
If this isn’t enough, there are also major tax concerns when it comes to inheritance, which vary based on geographical location. Again, unless they’ve had the great misfortune of going through the process previously, it is not very likely that the average person is an expert in tax law regarding willed assets and inheriting wealth. Without proper planning, wealth that should be going to the next of kin of the deceased can end up being paid in unnecessary taxes instead.
Inheritance management advisors can help with this issue. Not only do these experts have a lot of experience being a supportive presence for grieving families, but they also have the benefit of being well-versed in how to maximize the impact of an inheritance to help the family going forward.
Additional Considerations
An initial meeting with an expert in inheritance can make a world of difference in how solidified your plan is for when the worst happens to you or your loved ones. The professional advisor likely has years of experience in having discussions about wealth and estate planning, and can help to overcome the initial hesitancy regarding the difficult topic of death.
Your planning professional will also know local inheritance tax law and can help to create a structure that allows you or your loved one to give as much of the wealth that has been accumulated to whomever you desire, instead of having to pay an unnecessary amount to the government. Of course, it is best to follow the law and to pay the necessary taxes to avoid even further headaches when mourning a loved one, but few people would sign up for more of their wealth going to their government than to their own family, friends, or charitable causes.
In addition to tax planning, a proper plan will also help to create a route forward for the assets in question once they’ve been passed along. There is not necessarily a “right” answer to what should be done with the inheritance, but meeting short-term goals while ensuring longevity of the wealth to benefit the family without burning through it all is a balance that is easier struck by an unbiased third party than from within the familial unit.
Experts should be well-versed in the asset class or classes that are being passed on. There are so many different types of assets, especially today, that everyone can’t be an expert on every type of asset class or market. Ideally, the initial meeting with an estate planning professional can help identify what types of assets you or your loved one owns, what the plan is for those assets, and how comfortable the advisor is with planning around these types of assets. A good professional will assist in their own areas of expertise and have a network of experts in areas that they’re less familiar with to consult with or outsource management services to on behalf of clients.
With the emergence of blockchain technology, wealth has started being accumulated in digital assets over the course of the last decade and a half. While most asset custodians execute the beneficiary wishes of their customers on their behalf, digital assets can be self-custodied.
A plan for digital asset inheritance management should be conducted with a company like Vault12, who have experts in blockchain and crypto technology. This can be done in addition to planning for non-digital assets, which a traditional estate planner would likely have more experience with up to this point in their career.
If you or a loved one is involved in blockchain and digital assets, it can be too easy to misplace or lose access to wealth that exists on the blockchain without a proper plan. Instead of panicking during an already traumatizing event, consider reaching out to Vault12 for a consultation to discuss creating a wealth management plan.
Digital Inheritance with Vault12
How it Works
Vault12 Releases Open-Source Capacitor Plugin for Quantum-Safe Data Storage
Production-proven Shamir’s Secret Sharing now available for iOS, Android, and Web apps
Miami, FL – December 2, 2025 – Vault12, Inc., the pioneer of crypto inheritance, today announced the open-source release of the Shamir Secret Sharing plugin for Capacitor, a new plugin for the Capacitor framework that enables app developers to add quantum-safe data storage for iOS, Android, and web applications using Shamir’s Secret Sharing.
The Shamir Secret Sharing plugin for Capacitor plugin brings information-theoretic security—protection based on mathematical impossibility rather than computational difficulty—directly into modern, cross-platform app stacks. By splitting sensitive data into multiple cryptographic shards, developers can eliminate single points of failure and build applications that remain secure even in a post-quantum world.
This plugin has already been battle-tested in production for a decade on almost a million iOS and Android devices, as a core component of Vault12 Guard, a mobile app that provides decentralized backup, and inheritance for crypto wallets and other sensitive data.
“Developers building self-custody and high-assurance apps need tools that won’t break the moment quantum computing becomes practical. With the Shamir Secret Sharing plugin for Capacitor, we’re making the same Shamir’s Secret Sharing engine that powers Vault12 Guard available to anyone building the next generation of secure, user-controlled applications.”
— Blake Commagere, Co-founder and COO, Vault12
Shamir’s Secret Sharing (SSS), originally devised by Adi Shamir (the “S” in RSA), allows a secret to be mathematically split into multiple shares, with a configurable threshold required to reconstruct it. Individual shares reveal nothing about the underlying secret, ensuring that no single compromise exposes user data.
Capacitor is an open-source, cross-platform native runtime that lets developers build iOS, Android, and web apps from a single modern JavaScript/TypeScript codebase. It provides a consistent API and plugin system to bridge web frameworks (React, Vue, Angular, etc.) with native device capabilities such as secure storage, biometrics, and the filesystem.
Key features of the Shamir Secret Sharing plugin for Capacitor plugin include:
- Quantum-resistant security using Shamir’s Secret Sharing with information-theoretic guarantees
- Cross-platform support for iOS, Android, and Web via Capacitor
- Flexible storage options, including memory-based and filesystem-based operations
- Progress tracking for long-running operations and large files
- Robust recovery, supporting reconstruction of complete secrets or individual shards
- Production-proven reliability, already protecting high-value digital assets for Vault12 Guard users
Developers can access the source code, documentation, and implementation examples on GitHub: https://github.com/vault12/capacitor-shamir
About Vault12 Guard Crypto Inheritance
Video: Introducing Digital Inheritance
About Vault12
Founded in the United States over a decade ago, Vault12 is dedicated to solving crypto inheritance challenges through quantum-safe encryption and decentralized social custody. The company is venture funded, including investments from Winklevoss Capital, Naval Ravikant, Data Collective, and True Ventures. Vault12 Guard is available in the Apple App Store and Google Play store.
For media inquiries, please contact: Wasim Ahmad media@vault12.com
Quantum-safe Data Storage for App Developers with Open-Source Shamir Secret Sharing for Capacitor
Production-proven Shamir’s Secret Sharing Capacitor Plugin now available for iOS, Android, and Web apps
How to build quantum-resistant apps with the Shamir Secret Sharing plugin for Capacitor?
The future of computing is knocking at our door. Quantum computers promise to revolutionize industries, solve impossible problems, and, unfortunately, break most of the encryption that protects our digital lives today.
This is where the Shamir Secret Sharing plugin for Capacitor plugin becomes your secret weapon for building truly resilient and secure apps.
What is Capacitor by Ionic?
Capacitor is an open-source, cross-platform native runtime that lets developers build iOS, Android, and web apps from a single modern JavaScript/TypeScript codebase. Created by the team behind Ionic, it provides a consistent API layer that bridges web technologies (like React, Vue, Angular, or vanilla JS) with native device capabilities such as secure storage, biometrics, filesystems, and more. Through its plugin system, Capacitor allows both first-party and community plugins—like Shamir Secret Sharing plugin for Capacitor—to expose powerful native functionality in a way that feels natural to web developers, enabling high-performance, production-grade apps without sacrificing the speed and flexibility of a web-based stack.
What are the challenges of Self-Custody?
We're witnessing a fundamental shift in how people think about their digital assets and personal data. From crypto wallets to personal health records, users increasingly want control over their own information. They don't want to trust centralized services with their most sensitive data.
But self-custody creates a terrifying problem: what happens when someone loses their phone, forgets their password, or worse—their device gets stolen? Traditional backup solutions force users to trust third parties or create single points of failure.
The Shamir Secret Sharing plugin for Capacitor plugin solves this elegantly by eliminating the need for any single point of trust or failure.
What is the mathematics behind Shamir's Secret Sharing?
Shamir's Secret Sharing reads like something from a cryptography fairy tale. Invented by Adi Shamir (the "S" in RSA encryption), this algorithm takes any secret and mathematically divides it into pieces called shards.
Here's where it gets beautiful: you can lose some shards and still recover your secret perfectly. Need 3 shards to reconstruct your data? Generate 5 shards and distribute them to trusted friends or devices. Even if 2 shards disappear forever, you can still recover everything.
But the real magic happens in what cryptographers call "information-theoretic security." Each individual share reveals absolutely nothing about your secret. Not a single bit of information leaks, no matter how powerful the computer trying to crack it.
This isn't just computationally difficult to break—its mathematically impossible. Even with unlimited processing power, an attacker with insufficient shards learns nothing. The mathematics guarantee this, not the limitations of current technology.
How do you Future-proof against quantum threats?
Most encryption today relies on mathematical problems that are hard for classical computers to solve. Factoring large prime numbers takes classical computers thousands of years. Quantum computers could solve these same problems in hours.
Shamir's Secret Sharing takes a completely different approach. Its security doesn't depend on computational difficulty—it depends on mathematical impossibility. Think of it like trying to solve an equation with fewer values than unknowns. There are infinite equally valid solutions, making it impossible to determine which one is correct.
This information-theoretic approach means quantum computers offer no advantage to attackers. The underlying mathematics remain just as secure whether facing classical computers, quantum computers, or hypothetical super-quantum computers that might emerge decades from now.
Your applications built with the Shamir Secret Sharing plugin for Capacitor today will remain secure through whatever computing revolution comes next.
How can you Fault-proof your apps through distribution
Traditional security models create single points of failure. Lose your password manager database? Everything's gone. Company servers get compromised? Your data's exposed. Phone gets stolen? Access to your accounts vanishes.
Shamir's Secret Sharing flips this model entirely. Instead of protecting one critical thing perfectly, you distribute security across multiple independent channels. Each share can live in a different place:
- One share encrypted by your phone's secure enclave
- Another with a trusted friend or family member
- A third is stored in a safety deposit box
- Additional shards distributed to other devices or locations
The threshold system means you're protected against multiple simultaneous failures. Device breaks? Friend moves abroad? Safety deposit box becomes inaccessible? Your system keeps working because no single failure can compromise your security.
This distributed approach creates applications that become more resilient as they scale, not more vulnerable.

What are Common Use Cases for the Shamir's Secret Sharing Capacitor Plug-in?
The Shamir Secret Sharing plugin for Capacitor plugin provides the foundation, but imagination determines the possibilities. Consider these emerging use cases:
Family digital inheritance becomes possible when crypto seeds or important documents are shared across trusted family members. Parents can ensure their digital assets transfer smoothly without exposing sensitive information during their lifetime. That's what the Vault12 Guard app does by using Shamir Secret Sharing plugin for Capacitor.
Collaborative authentication allows teams to protect shared resources without any single administrator having complete control. Critical business systems require multiple people to authorize changes, preventing both external attacks and insider threats.
Progressive disclosure enables applications that reveal information only when specific conditions are met. Legal documents that unlock automatically when multiple parties agree, or time-locked messages that require distributed consent to access early.
Redundant backup systems can store encrypted application state across multiple cloud providers, user devices, and physical locations. Users never lose access to their data, but no single provider ever has complete information.
The plugin's cross-platform nature—supporting iOS, Android, and web—means these experiences work seamlessly across all user devices and contexts.
How has the Shamir's Secret Sharing Capacitor Plug-in been tried and tested in commercial apps?
The convergence of quantum computing, increased privacy awareness, and demand for user-controlled applications creates unprecedented opportunities for developers who think ahead.
Applications built with traditional security models will face obsolescence as quantum computers emerge. Centralized platforms will struggle as users demand true ownership of their data. Single points of failure will become unacceptable as digital stakes continue rising.
But developers using Shamir Secret Sharing plugin for Capacitor can build applications that thrive in this new landscape. Your users get genuine self-custody without sacrificing usability. Your architecture becomes more resilient as it scales. Your security improves as computing power increases rather than becoming more vulnerable.
The plugin abstracts away the complex mathematics and cross-platform implementation details. You get enterprise-grade Shamir's Secret Sharing through simple TypeScript interfaces, letting you focus on creating innovative user experiences rather than cryptographic implementation.
How can you start using the Shamir's Secret Sharing Capacitor Plug-in?
Quantum computers won't wait for our applications to catch up. User expectations for data ownership and privacy continue accelerating. The developers who start building quantum-resistant, fault-proof applications today will define the next generation of digital experiences.
The Shamir Secret Sharing plugin for Capacitor plugin gives you the tools. The mathematical foundations are unshakeable. The production validation is complete. The cross-platform compatibility ensures a broad reach.
What remains is the most exciting part: imagining and building the resilient, user-empowering applications that will define computing's next chapter. The future belongs to developers who understand that true security comes not from building higher walls, but from removing single points of failure entirely.
Your users are ready for applications they can truly trust. The technology is ready to support your vision. The question is: what will you build?
Using the Shamir Secret Sharing plugin for Capacitor - Github: https://github.com/vault12/capacitor-shamir
What is Shamir's Secret Sharing?
Shamir's Secret Sharing is a cryptographic algorithm that divides a secret into multiple parts (shards), where a minimum threshold of shards is required to reconstruct the original secret. This ensures that:
- No single shard reveals any information about the secret
- Any threshold number of shards can reconstruct the secret
- Security through distribution - store shards separately for maximum security
What are the Security Concepts behind Shamir's Secret Sharing?
Shamir's Secret Sharing provides information-theoretic security, which means the algorithm is mathematically proven to be unbreakable regardless of computational power. Key security advantages:
- Quantum Resistance: Security relies on mathematical impossibility rather than computational complexity, remaining secure against quantum computers
- No Key Management: There is no single master key to rotate or protect; instead, security hinges on distributing and safeguarding the individual shards
- Mathematical Foundation: Based on polynomial interpolation over finite fields, where reconstructing the secret without sufficient shards is mathematically impossible, not just computationally difficult
What are the features of Shamir's Secret Sharing Capacitor Plug-in?
- Secure Secret Splitting: Split sensitive data into encrypted shards using Shamir's Secret Sharing
- Cross-Platform: Native support for iOS, Android, and Web
- Flexible Storage: Memory-based and filesystem-based operations
- Progress Tracking: Real-time progress callbacks for all operations
- Performance Optimized: Efficient handling of large files and data
- Recovery Options: Restore complete secrets or individual shards
What are examples of Real-World Usage?
This plugin has already been battle-tested in production for a decade on almost a million iOS and Android devices, as a core component of Vault12 Guard, a mobile app that provides decentralized backup, and inheritance for crypto wallets and other sensitive data.
More information is at Github: https://github.com/vault12/capacitor-shamir
Vault12 Guard Adds Support for Apple’s New Credential Exchange Protocol (CXP), Enabling Inheritance of your Passwords, Simply and Securely
Miami, FL – November 19, 2025 – Vault12, Inc., the pioneers of crypto inheritance and decentralized backup, today announced that Vault12 Guard™ now supports Credential Exchange Protocol (CXP), giving iPhone, iPad, and Mac users a secure, standardized way to move their passwords and passkeys into their inheritance Vault to protect their digital legacy.
With this update, anyone running iOS 26, iPadOS 26, or macOS 26 can securely import logins, passkeys, verification codes, and even Wi-Fi credentials directly from Apple Passwords, Bitwarden, and other compatible managers into Vault12 Guard—without exporting files or manually copying data. The transfer happens through an OS-controlled flow that maintains encryption between the source app and Vault12 Guard.
“Credential portability has finally arrived. By plugging into the CXP standard, Vault12 Guard becomes a neutral, long-term backup and inheritance hub for all your critical credentials—not just crypto seed phrases.”
— Wasim Ahmad, Chief Crypto Officer, Vault12
Once inside Vault12 Guard, credentials are:
- Protected by Guardians – Encrypted, split, and stored across trusted people and devices rather than a single cloud provider - even if you lose your phone.
- Inheritance-ready – Integrated with Vault12’s digital inheritance flows so beneficiaries can recover essential logins and other digital assets.
- Future-proof and portable – Users or beneficiaries can later export their credential bundle from Vault12 Guard back into any compatible password manager that supports the same standard.
A detailed walkthrough of how to import and export credentials using CXP and Vault12 Guard is available in the latest blog post on the Vault12 website (vault12.com)
About Crypto Inheritance
Video: Introducing Digital Inheritance
About Vault12
Founded in the United States over a decade ago, Vault12 is dedicated to solving crypto inheritance challenges through quantum-safe encryption and decentralized social custody. The company is venture funded, including investments from Winklevoss Capital, Naval Ravikant, Data Collective, and True Ventures. Vault12 Guard is available in the Apple App Store and Google Play store.
Media Contact: Wasim Ahmad media@vault12.com
Vault12 Guard now imports your iOS Credentials from Apple Password and other Password Managers
Vault12 Guard now supports Apple’s new Credential Exchange Protocol (CXP), making it much easier to bring your existing credentials into your inheritance Vault.
How to Move Your Passwords, Passkeys, and Codes Between Your Password Manager and Vault12 Guard?
With the latest Vault12 Guard release, effortless password backups are no longer just for crypto and seed phrases — you can now bring in your logins, verification codes, passkeys, and even Wi-Fi credentials from Apple Passwords and major third-party managers (like Bitwarden), store them in your decentralized Vault, and export them back into any compatible app later if you ever need to move or recover. This works on iPhone, iPad, and Mac running iOS 26, iPadOS 26, and macOS 26.
Vault12 Guard now supports Apple’s new Credential Exchange Protocol (CXP), making it much easier to bring your existing credentials into your inheritance Vault. CXP is a new industry standard designed for the secure transfer of passkeys and passwords between compatible apps and platforms—so instead of manually copying details or re-creating accounts, you can move them directly and safely into Vault12 Guard.
With iOS 26, Apple is the first major platform to roll out CXP, opening the door to real credential portability and user choice. Thanks to our integration, iPhone users now have a secure, standardized way to import passkeys from other password managers and platforms into Vault12 Guard, while keeping everything encrypted and under their control.
Why back up your credentials in Vault12 Guard?
When you bring credentials into Vault12 Guard, they’re protected like any other high-value asset:
- Decentralized protection with Guardians
Your credentials are encrypted, split, and stored across your chosen Guardians (trusted people or your own devices), not in a single cloud account or server. - Inheritance-ready by design
Through Vault12 Digital Inheritance, your beneficiary can recover critical logins and keys when Guardians approve an inheritance request—using the same audited restore flow already documented for other assets. - No vendor lock-in
Because Vault12 Guard uses the same system-level transfer mechanism as Apple Passwords and leading managers like Bitwarden, you can always export your credentials back into another app later.
We strongly recommend having active Guardians configured before importing, so your credential backup is both secure and recoverable.
What is needed to import your passwords into Vault12 Guard?
- Vault12 Guard updated to the latest version on iOS 26 / iPadOS 26 / macOS 26.
- A password manager that supports the new secure export flow, such as:
- Apple Passwords
- Bitwarden
- Other compatible apps as they roll out support over time.
How are Passwords transferred into and out of Vault12 Guard?
Apple’s Credential Exchange capabilities in iOS 26, iPadOS 26, and macOS 26 introduce a standardized, OS-controlled way for credential apps to talk to each other securely.
At a high level:
- The export always starts in the app that currently holds your data (Apple Passwords, Bitwarden, etc.).
You choose an option like “Export data to another app” / “Move to another password app”. - The system shows a list of compatible destination apps (including Vault12 Guard).
- Once you select Vault12 Guard, the OS:
- Packages the selected credentials (logins, passkeys, verification codes, and, where supported, Wi-Fi details),
- Sends them directly and securely to Vault12 Guard,
- Ensures only the chosen destination app can read them.
No manual juggling, no generic file exports in this flow—just a controlled, encrypted handoff mediated by the operating system and the participating apps.
Vault12 Guard simply plugs into this mechanism as a secure backup & inheritance destination (and as an export source), instead of inventing its own incompatible format.
How do I import passwords into Vault12 Guard?
Use this when you want Vault12 Guard to serve as your resilient backup for credentials stored elsewhere.
On iPhone, iPad, or Mac (same pattern):
- Open your password manager (e.g., Apple Passwords, Bitwarden).
- Select the items you want to protect in Vault12 Guard:
- Logins, passkeys, verification codes, Wi-Fi credentials.
- Choose “Export to another app” / “Move to another password app”.
- In the destination list, select “Vault12 Guard”.
- Vault12 Guard opens:
- Shows what’s being imported,
- Lets you choose Asset Name,
- Confirms and saves everything into your Vault.
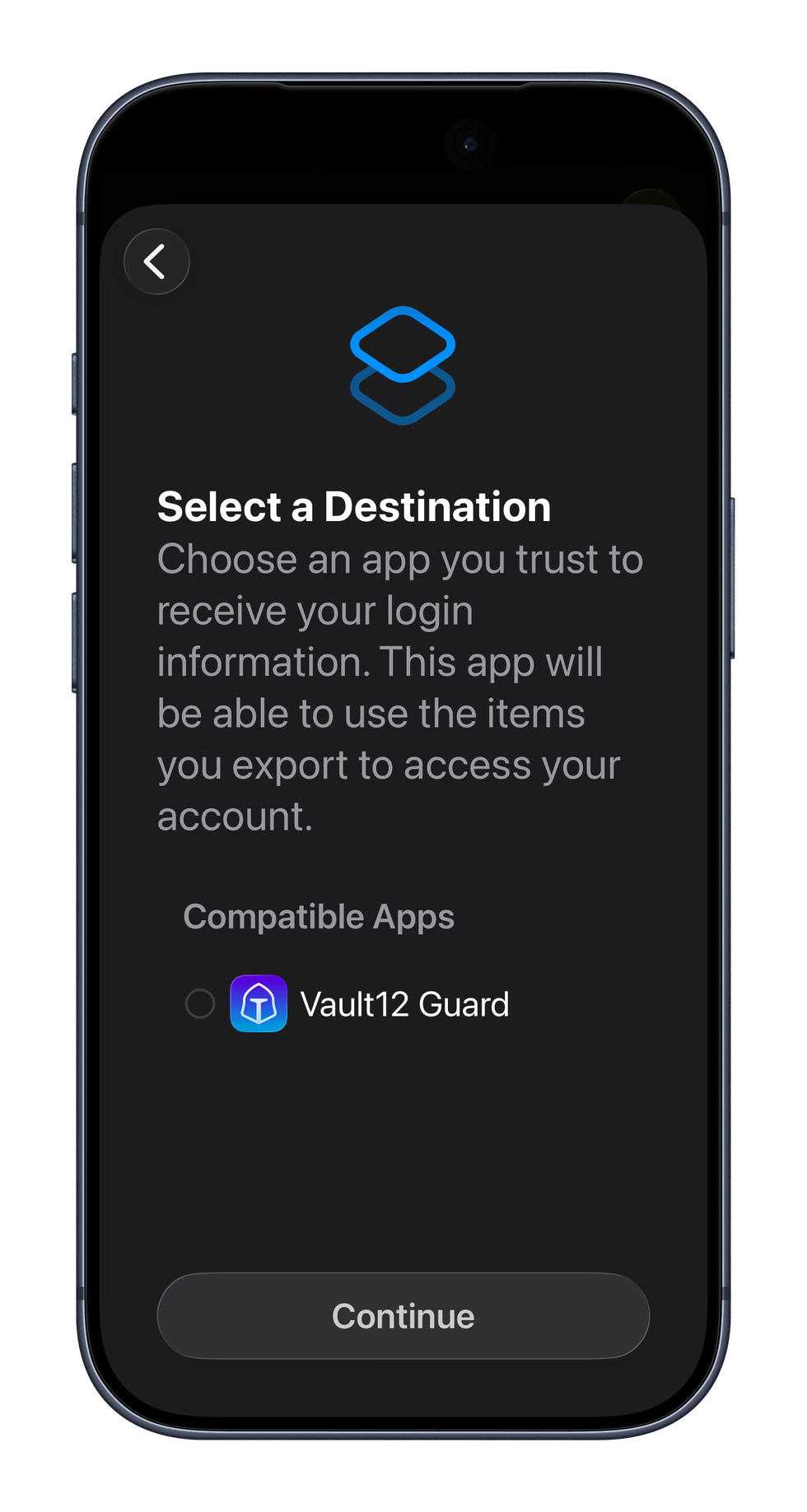
In Apple Password choose the Export option and select the credentials to export, then select the destination.
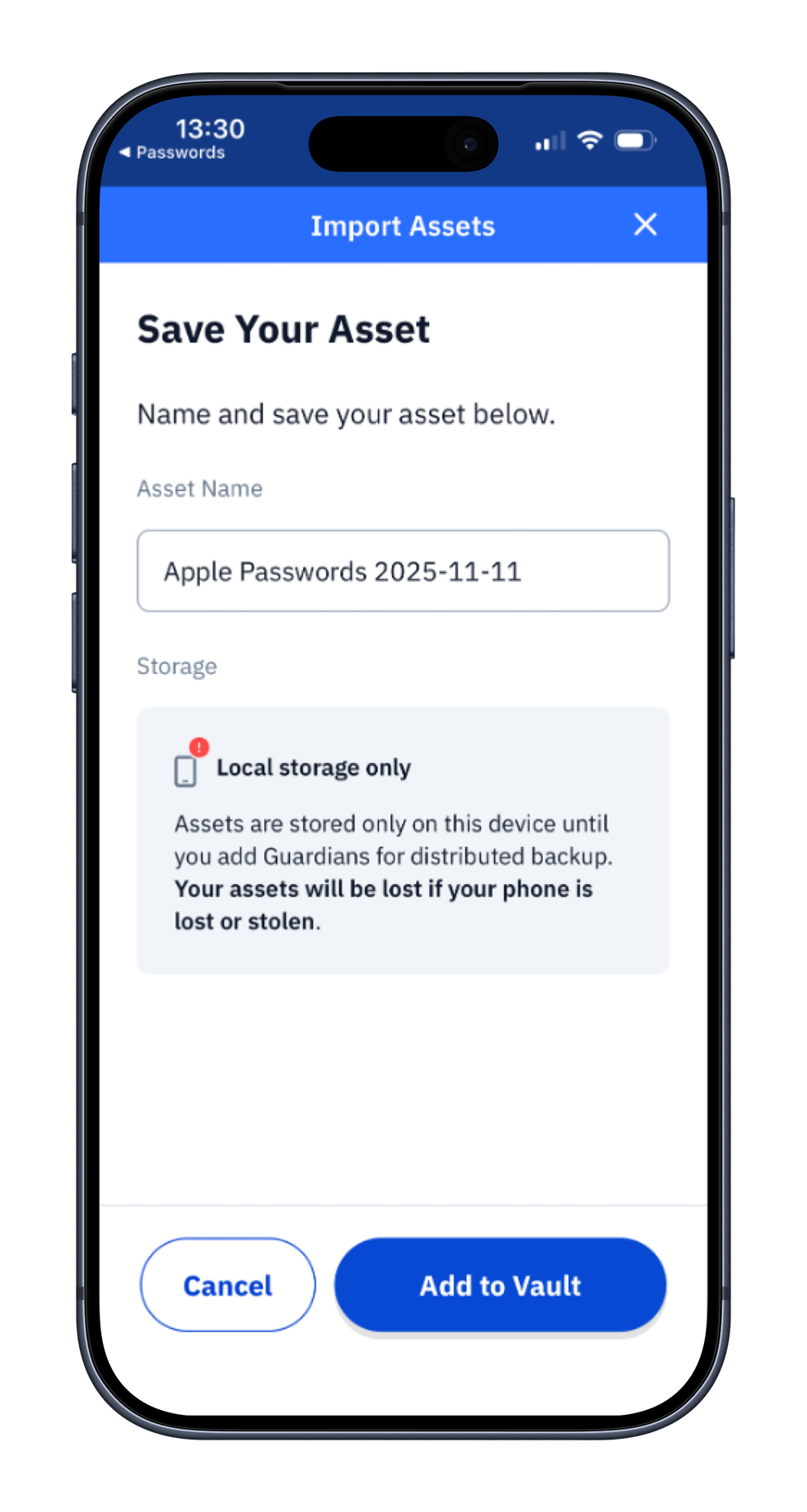
Once exported open Vault12 and name your credential file and add to your inheritance Vault.
How do I export from Vault12 Guard into another app?
When a Vault is inherited and contains an imported password file, you can export the file to compatible password managers.
Also, you can use this if you’re switching tools, rebuilding another manager, or validating portability.
On iPhone, iPad, or Mac:
- Open Vault12 Guard.
- Navigate to the relevant Asset Details screen.
- Open the context menu (⋯).
- Tap “Export Credentials to Another App”.
- Choose your target (e.g., Apple Passwords, Bitwarden, other supported managers).
- Confirm the system prompt.
The OS delivers those credentials straight into the chosen app using the same secure channel—so Vault12 Guard is both an endpoint for imports and a clean, standards-aligned source for exports.
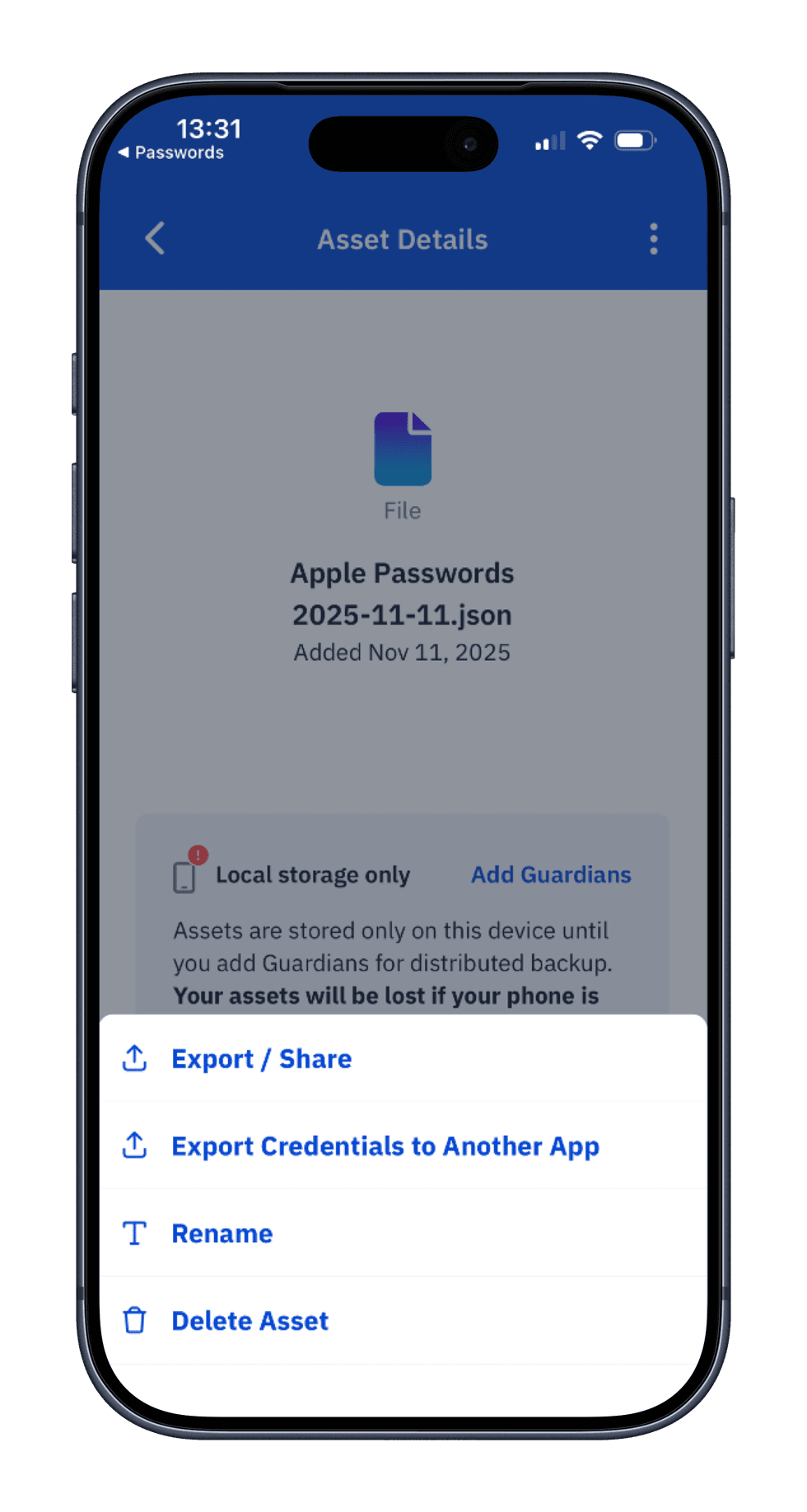
Export Passwords file
What are the best practices for transferring credentials with Vault12 Guard?
- Import only on trusted devices protected with biometrics and device passcodes.
- Keep Guardians active & up to date to avoid recovery friction later.
- Use Vault12 Guard as your neutral backup hub, not as a replacement for day-to-day autofill. Let your password manager handle sign-ins; let Vault12 Guard guarantee long-term recoverability.
- Only export to apps you trust. The system dialog makes this explicit—if you don’t recognize the app, don’t send credentials there.
1) AppleID/iCloud Password and Passkey are NOT backed up during export from Apple Password
2) Master passwords to password managers should be backed up manually
Inheritance Management
Managing digital assets like cryptocurrencies can be complex, especially when it comes to inheritance.
View all articlesThe Great Inheritance and Crypto: What you need to know.
The Great Inheritance or The Great Wealth Transfer and Crypto and what it means for you.
The Great Inheritance is here - huge growth in wealth acquisition via Inheritance.
Crypto and Digital Assets make up approx 5-10% $6T in the next 20 years.
Ensure your customers can inherit crypto assets with Vault12.
For $1 a day your customers and their friends a manage their crypto inheritance, easily.
Summary
We are in a unique period of history. Referred to as the Great Inheritance, it is a time when inheritance is the greatest vehicle of wealth accumulation. Over $6T will be passed down to people in 2025 alone, with $80 trillion of assets passing to younger generations over the next twenty years. This means that effective strategies for wealth transfer and wealth acquisition must be in place, including for crypto and other digital assets.
Unlike traditional assets, crypto assets must be documented ahead of time; otherwise, they will be lost and irrecoverable. This requires careful management, as recording information about your crypto wallets (seed phrases and private keys) must be done in a secure and private way; otherwise, should that information get into the wrong hands, these wallets can be emptied ahead of time.
Many solutions exist to document this sensitive information. The problem, however, is that they all suffer from risks and drawbacks. This is why a native solution based on maximizing privacy and security was created by Vault12, the pioneers of crypto inheritance. This process involves securely backing up your crypto wallets, then designating a technical beneficiary. This is done in a simple and easy-to-use fashion, suitable for both the average retail consumer as well as law firms and wealth managers alike.
A little crypto inheritance planning and management will safeguard accessibility to assets from one generation to the next.
Inheritance Growth Over The Years
Image courtesy of The Economist
According to The Economist, inheritance rates are rising to levels not seen since the early 1900s. While this chart measures inheritance as a percentage of national output and not the net value of the inheritance alone, national output has undoubtedly grown globally in most cases over the past century. The Economist states that this year, the total value that will be inherited globally is equivalent to around 10% of global GDP.
What Can We Learn From The Past?
In many cases, inheritance is the largest windfall of value that people will receive at one time in their lifetime. Couple this with it occurring during a period of grief that overwhelms, and it is clear how easy it is to make decisions that lead to value destruction instead of value accumulation.
In the previous chart from The Economist, there is a clear lull in inheritance growth as a percentage of national output in the middle of the 20th century. Back in the 1960s, at the approximate bottom of the chart, it was difficult to access investment products as an average citizen globally. The internet did not exist. There had been no democratization of financial markets. Investment was available to a small portion of the population, and based on the chart, even those who could access it didn’t use it well when it came to maintaining the value of their family’s wealth.
It can be incredibly tempting to spend such a windfall, especially in a time of grief. We see the temptation to “rub your hands in glee and ponder what you ought to do” with your inheritance, as The Economist article describes. It can be surmised that this is why so few of today’s globally wealthy can trace their wealth back to the early 1900s, when the inheritance flow as a percentage of national output was at its highest levels.
Today’s Challenges
In today’s world, even more pitfalls exist than those navigated by the families of the industrial pioneers of the early 1900s. Not only are there more shiny toys to buy than ever before, but access to financial markets has become even more widespread than at any prior point in human history. This means that even if you make the responsible decision to invest some or all of an inheritance, there are more options as to what to do with that money than ever before.
In the age of the internet, someone is promising to change your entire life around every corner with the next incredible investment opportunity. These types of promises can sway people into making poor decisions with their money in any scenario, but especially when they’re in a vulnerable state after a family tragedy.
Image courtesy of The Economist
In their book “The Missing Billionaires,” wealth managers Victor Haghani and James White show that if the millionaires of the past had simply worked with someone who could’ve helped them properly plan what to do with their family fortune, they could have increased the value of each dollar invested by a multiple of six figures over the course of the past century. The Economist uses this historical data to show the value of properly planning and allocating an inheritance.
Applying this lesson to today, more and more people stand to benefit from the work that their parents and grandparents have put in over the course of their lifetimes than ever before. The decision of what to do with this money when the time comes can feel overwhelming, but creating a plan and sticking to it, especially in a time of grief, can lead to preservation and growth of the family fortune for not only you, but your children and grandchildren as well.
Who Stands to Gain?
A recent report, the 2024 Bank of America Private Bank Study on Wealthy Americans, shows key trends related to inheritance, and particularly how younger generations view the future of wealth, including crypto and estate planning. An astounding $84 trillion of wealth transfer is projected over the next 20 years from current generations to Gen X, Millennials, and Gen Z.
According to the report, younger generations (ages 21-42) are more inclined to see digital assets like cryptocurrency as a key growth opportunity. Around 28% of younger respondents ranked crypto as a promising investment vehicle, significantly higher than older generations, where only 4% expressed the same confidence. This highlights the generational shift towards embracing newer financial instruments like blockchain and decentralized finance.
Interpersonal family dynamics can create tension during wealth transfers. For both younger and older wealthy individuals, unequal distribution of assets and a lack of clear instructions or communication were common sources of strain. Younger heirs are more likely to pursue alternative investment strategies, such as private equity and digital tools, reflecting their broader interest in controlling their wealth. These individuals also prioritize sustainability and impact investing as part of their inheritance planning, distinguishing their approach from older generations.
These insights demonstrate the ongoing generational divide in attitudes toward wealth management and the evolving role of digital assets in estate planning.
How Do Digital Assets Tie Into Inheritance?
Given that approximately $84 trillion is projected to transfer from seniors and baby boomers to Gen X, millennials, and their heirs by 2045, Matthew Sigel of VanEck Investments estimates that up to $6 trillion could enter the crypto market through inheritance in the next 20 years.
Why does Sigel believe this to be the case? Well, we can surmise from the earlier information regarding digital asset investment that as this money makes its way down to younger generations, there will be a larger appetite for alternative investments outside of stocks and bonds than there was in previous generations. As a growing and developing new asset class, digital assets will certainly gain their fair share of attention from younger investors, who will be looking to diversify and conserve what will likely be their largest windfall they receive in their lifetimes.
You may think that this would require an immense risk appetite, given the volatility of digital assets in their young existence, but for Sigel’s estimate to be correct, only approximately 14% of this Great Inheritance would need to be allocated to digital assets. Couple this with the fact that younger investors do generally have a higher risk appetite than their older counterparts, and it doesn’t seem that far-fetched that Sigel’s estimate could be accurate, or even fall short of what ends up flowing into digital assets.
Breaking Down Digital Asset Inheritance
Unlike traditional assets, crypto assets need to be managed differently from an inheritance standpoint. In fact, the only similarity between traditional and digital assets is that you must maintain an updated inventory of them. The main challenges associated with crypto inheritance are:
- Ongoing Digital Asset Inventory: You must carefully maintain an inventory of crypto assets. This means backing up seed phrases and/or private keys of all crypto wallets, across all blockchains, and all types of devices or places where those wallets exist, e.g., mobile phones, hardware wallets, cloud, and paper backups. Any assets that are not documented in your backup are liable to be lost.
- Absolute Informational Privacy: You must ensure absolute privacy of the backup information. Anyone with access to private keys or seed phrases will be able to compromise the funds. This includes ensuring that any documentation left with your lawyers is strongly protected.
- Critical Points of Failure: You must eliminate personal devices and cloud services as critical points of failure. The most significant risk in inheritance is reliance on individual devices, which can be stolen, lost, or damaged. The second risk is the dependency on one or more cloud servers. We have seen what happens when business relationships between cloud partners face legal challenges, or cloud services are disrupted by malware or bad software updates.
- Technical Beneficiary Awareness: As the varieties of crypto assets expand over time, staying aware of them becomes important. You will need to designate someone technically fluent in this area. They may not be the ultimate beneficiary; however, you will need to trust them to distribute the assets per your wishes.
- Trust & Estate Attorney: You must consult with experienced lawyers who are well-versed in the inheritance of crypto assets. A great resource is "A Practical Guide to Estate Administration and Crypto Assets" by Richard Marshall from Hill Dickinson LLP.
How Vault12 Can Help
Alright, so you’ve read this far and are convinced that doing nothing and having no plan is not a good idea. However, you also read the part where it is acknowledged that this can be a difficult subject, and you’re curious how to overcome that to ensure that you don’t end up like the families of yesteryear.
The great news today is that there are inheritance management advisors out there who can help you and your family navigate this difficult topic. While this discussion may be difficult to have with your loved ones around the dinner table at a family holiday, setting an appointment with an advisor and making time to be intentional about creating a plan is a great first step in figuring out how best to navigate the future of your family’s finances.
A quality advisor will not only help you avoid all of the pitfalls of trying to invest your inheritance all on your own, but their presence and expertise in navigating these types of conversations with families over the course of their career will help make the topic more palatable for you and your family when you meet with them.
Creating a plan for your family’s existing assets, especially in today’s age, will help protect your family’s legacy from any short-term decisions brought on by grief, confusion, or anger. It is essential to acknowledge these emotions as an integral part of the human experience. Allowing yourself the ability to experience and sort through them without it having a lasting impact on your family’s future is a critical lesson that we all can take from the shortcomings of generations gone by.
Why Choose Vault12?
Vault12 is the pioneer of crypto inheritance management. Vault12 Guard is the first solution to offer a simple, direct, and secure way for all types of investors to ensure that all of their crypto assets can be accessed by future generations.
Just because digital assets are new does not mean that classic lessons of asset management have no applicational purpose in this asset class. Stop to consider traditional approaches to the inheritance of assets, when applied to digital assets, create complexity and risk. Your portfolio of digital assets is continually changing — you cannot rely on doing an inventory once, or for that matter continuously, without assistance.
Taking a simple and direct approach like Vault12 Guard reduces the uncertainty around assets not being available to the designated recipient. It also avoids having to approach and petition each service individually during probate to gain access.
What Benefits Does Vault12 Offer?
Especially in a time of crisis, like in the event of losing a loved one, the less that the family has to put on their plate and struggle through while simultaneously mourning, the better. Vault12 offers a variety of benefits for peace of mind. Let’s walk back through the checklist from before about variables that you’d want to consider when mulling over digital asset inheritance:
- Inventory of crypto assets: The first step in inheritance is backing up all your crypto wallets. Vault12 makes this as easy as possible - despite the appalling lack of usability in current hardware and software wallets. There will always be new crypto assets on new blockchains, and Vault12 can manage any crypto asset on any device, on any blockchain, now and in the future.
- Privacy of all information: Your crypto assets are protected via a Secure Element (Secure Enclave in iOS, and Strongbox on Google Android phones), and the encryption used is Quantum-safe. With this security, no one knows what assets are part of your Vault.
- No Critical Points of Failure: No assets are stored locally, no assets are stored in any cloud, and no assets are stored at Vault12. There are no devices to lose, no paper backups, and no need to manually give encrypted assets to a subset of people. The Vault12 system is decentralized, making it a difficult target for hackers — and in fact for any type of failure.
- Confidence in a Technical Beneficiary: With Vault12, you get to designate a trusted technical beneficiary. Should you change your mind, you can swap them out at any time.
- Flexibility in Trust & Estate Attorney: While regulations and guidelines for inheritance planning can vary from state to state and country to country, Vault12 Guard is designed to be independent of whatever legal framework you choose to govern the inheritance of your assets. Vault12 Guard is simply a transfer mechanism that ensures all your crypto assets are passed from your control to a designated technical beneficiary.
Key Product Features of Vault12 Guard
The Vault12 platform provides your crypto assets with the highest security and strong backup resilience. Vault12 Guard Inheritance enables you to designate a beneficiary (an executor, trustee, or other chosen beneficiary) who can inherit the entire portfolio of digital assets that you choose to store in your Vault. There is no need to update an inventory continually or to issue updated instructions. Vault12 Guard Inheritance allows for peace of mind through the following features:
- Unified Digital Vault: Use Vault12 Guard Digital Vault to store digital assets, including cryptocurrency, financial login information, legal documents, medical records, and more.
- Guardian Network: The Vault is protected by your network of Guardians: friends, family, and/or business associates — people that you know and trust.
- Beneficiary Designation: Designate a beneficiary from your chosen Guardians. A declaration is then digitally signed and can be emailed to other parties, such as lawyers.
- Trigger-Based Access: As a Vault Owner, you can configure a legally-defined trigger, such as incapacitation or death. When the trigger occurs, the beneficiary indicates they are ready to access the digital assets. Assets are unlocked and transferred to the beneficiary only when a designated number of Guardians approve the request.
- Preemptive Veto Option: Should the beneficiary attempt to access the assets before they are intended to, the owner can veto the request before any of the Guardians receive an approval request.
How Can Estate Planners Utilize Vault12?
Would you, an estate planner, be willing to spend only $1 a day to protect your customers’ legacy and expand your customer base? What about offering peace of mind to your customers, especially in their time of need?
Anyone can download and use Vault12 Guard to protect their digital assets; it’s available in the Apple and Google app stores in most countries around the world. However, there is an even larger opportunity for financial institutions to provide crypto inheritance to their customers for as little as $1 a day.
Since Vault12 encourages the use of guardians, people that the customers know and trust, to guard their digital vault, the number of people engaged through the Vault12 product is much higher than any other solution for backup and inheritance. The guardians also get to experience safe and secure management of digital assets through the Vault12 Guard Inheritance program. This makes them more likely to use your services, as well as Vault12, for their own digital asset inheritance needs, given that they have already familiarized themselves with the product.
If you are interested in learning more about Vault12, please visit https://vault12.com/.
Sources
The Economist, 2025
- 2024 Bank of America Private Bank Study on Wealthy Americans, Bank of America
- The wealth whisperers who save super-rich families from themselves
- Inheriting is becoming nearly as important as working
Van Eck/CoinMarketCap, 2024
FT (Capital Group)
- Boomers to Zoomers: Engaging the next generation of wealth
- From widows to CFOs: how women navigate inheriting wealth
- Billionaires amass more through inheritance than wealth
- The great wealth transfer is coming…
- Attracting the next generation of inheritors and self-made wealthy
- Lack of holistic advice drives inheritors to regret
Bank of America Private Bank
- 2024 Study of Wealthy Americans (covers the Great Wealth Transfer, inheritance attitudes, and family dynamics).
UBS
- Own Your Worth 2025 (focus on women & next-gen readiness for the Great Wealth Transfer; includes full PDF).
- Heir dynamics: Money in motion (wealth transfer trends; PDF).
- Billionaire Ambitions Report 2024 (succession, legacies, and inter-gen transfers among billionaire families).
RBC Wealth Management
- Wealth transfer: Are you ready? (survey-based insights; with downloadable guide).
- Wealth Transfer (UK/Europe) (survey of 3,100+ people on giving & inheriting; report download).
J.P. Morgan Private Bank
- How to successfully gift to heirs (2025 thought leadership on distribution, governance & investment strategy for transfers).
- 2024 Global Family Office Report (includes succession planning & next-gen transition).
HSBC Global Private Banking
- Harmony through succession planning (2025) (family-owned businesses in Asia; wealth & business succession; PDF).
- European Family Office Report 2024 (succession preparedness & anticipated transfer timelines; PDF).
Barclays Private Bank
- Family Business Report (commissioned research with a section on the approaching inter-generational wealth transfer; PDF).
Northern Trust
- Wealth & Wisdom Across Generations (how to talk to loved ones about family wealth & transfers; PDF).
Fidelity (Wealth Management / Custody)
- State of Wealth Mobility (2024 study; communication & readiness for transfers highlighted).
- Additional planning content tied to inter-gen transfers (not formal “reports” but authoritative insights).
Staked crypto assets need inheritance too
DeFi assets in your wallet or staked - remember to back them up.
The world of digital assets is complicated. Understanding how to access, trade, and secure these assets is enough information to fill a book or two. This leads to an already steep learning curve for new users who may inherit these assets upon the passing of a loved one.
Not only can accessing the assets be complex, but you may not be the only one with access to your loved one's assets. Welcome to the world of Decentralized Finance (DeFi for short) and one of its first introductory functions: staking.
How to Inherit Staked Crypto: Traditional vs Liquid Staking
Staking is one of the most popular ways to earn yield on crypto assets, but few people think about what happens to those assets if the owner passes away. While staking can be a powerful tool for compounding returns, it introduces real danger of assets loss when it comes to inheritance.
In this article, we’ll walk through the two primary forms of staking — traditional (locked) staking and liquid staking — and explore what it takes to ensure they can be passed on securely and reliably. Whether you’re planning your estate or helping someone else manage theirs, knowing the difference matters.
🔐 Traditional Staking: Locked but Rewarding
In traditional staking, crypto assets are locked with a validator to help secure a proof-of-stake blockchain. While this earns staking rewards, the assets typically cannot be moved or used during the staking period, and there is often a mandatory “unbonding” delay when unstaking (ranging from a few days to several weeks).
Common Examples:
- ETH staked directly on Ethereum via a validator.
- SOL staked with a validator through SolFlare or Phantom.
- ATOM staked using the Cosmos Hub.
Inheritance Considerations:
How Vault12 Guard Helps:
Vault12 Guard enables the secure backup of private keys, seed phrases, and unstaking instructions, even if the original staking setup is complex. By storing all access materials offline in a decentralized, tamper-proof format, Vault12 Guard ensures that heirs can retrieve and unlock these assets when the time comes — without compromising security beforehand.
💧 Liquid Staking: Inheriting Without Lockups
Liquid staking offers an alternative: instead of locking tokens with a validator, users stake through a protocol (like Lido or Marinade) and receive liquid tokens in return — such as stETH for staked ETH via Lido Protocol, or mSOL for staked SOL. These tokens earn staking rewards and remain transferable, allowing holders to use them in DeFi while still compounding yield.
Inheritance Considerations:
How Vault12 Guard Helps:
Because liquid staking tokens are stored in wallets like any other crypto asset, they can be protected using the same Guard setup. Vault12 Guard secures access to the wallet containing these tokens, and can also store explanatory notes about what the tokens represent and how to use or convert them.
This ensures that even non-technical heirs can understand what they’ve inherited — and how to recover the full value.
⚖️ Traditional vs Liquid Staking: Inheritance Comparison
| Feature | Traditional Staking | Liquid Staking |
|---|---|---|
| Token Accessibility | Locked until unstaked | Transferable anytime |
| Technical Knowledge Needed | High (unstaking, validator selection) | Moderate (DeFi familiarity helps) |
| Inheritance Complexity | Higher | Lower |
| Smart Contract Risk | Minimal | Moderate (depends on provider) |
| Compatible with Vault12 Guard | ✅ Yes | ✅ Yes |
📘 Best Practices for Inheriting Staked Assets
Regardless of how your assets are staked, inheritance comes down to access and understanding:- Avoid reliance on exchanges: Custodial services may have inheritance policies (and may not), but if they do, they often require an enormous amount of legal hoops — or worse, a cross-border regulatory nightmare. Not to mention that it depends on the platform staying operational. Self-custody with Vault12 Guard frees your assets’ longevity from all those factors and gives you full control.
- Check compatibility: Due to architectural choices, Vault12 Guard is the only known solution to date for backup and inheritance that is officially compatible with inheriting staking and DeFi positions.
- Secure the keys: Vault12 Guard can store your wallet’s seed phrase, hardware device backup, or passcodes — all offline and under your control.
- Provide context: A secure note in Vault12 Guard can explain staking positions, validator choices, and steps for unstaking or liquidating.
- Test your plan: Ensure your heirs understand the recovery process — or rehearse it with a trusted person while you’re alive.
🧭 Final Thoughts
Whether your assets are traditionally staked or in liquid form, they represent long-term value — and that value deserves a secure, intentional inheritance path. By combining staking strategies with decentralized inheritance planning using Vault12 Guard, you can ensure that your assets outlive you, and remain protected for the people you choose.
Inheritance doesn’t have to be a vulnerability. With the right tools and mindset, it can be a legacy.
The death of safe deposit boxes
Where will you store your digital wallet seed phrases now?
Vaults are a historic solution
For thousands of years, wealthy tribes and individuals have stored their treasures in temples, palaces, and fortresses. From ancient Mesopotamia to Egypt to the Knights Templar to today’s public banks, vaults have long been used to safeguard valuable possessions.
In the last couple of centuries, increased availability has led more "regular people" to turn to safe deposit boxes held at banks or private vaults to store heirlooms, cash, and important documents. In this way, vaults — once limited to society's elites — became a popular and practical mechanism for protecting one's most important assets.
We all need vaults in today's digital world
Just in the last couple of decades, people have had to consider what the safest place is to store not just small physical assets, but also digital assets and passwords such as electronic documents and crypto wallet seed phrase backups.
Digital asset owners know how important it is to keep a backup copy of one’s wallet seed phrase. Losing your wallet seed phrase results in losing access to your digital wallet — and thus, losing access to all of the digital assets you hold! The stakes are very high, and there are not many simple and robust solutions to choose from.
Safe deposit boxes for digital wallet private keys?
It has seemed natural for many people to turn to safe deposit boxes to store paper, electronic, or engraved-metal copies of their digital asset wallet seed phrases. In fact, the iconic and well-educated Winklevoss twins Cameron and Tyler used safe deposit boxes as part of their early strategy to distribute and protect pieces of their Bitcoin wallet keys.
"The Winklevosses came up with an elaborate system to store and secure their private keys. They cut up printouts of their private keys into pieces and then distributed them in envelopes to safe deposit boxes around the country, so if one envelope were stolen the thief would not have the entire key.""How the Winklevoss Twins Found Vindication in a Bitcoin Fortune" by Nathaniel Popper, New York Times, December 19, 2017
Safe deposit boxes are no longer the best solution
But given the state of the world today, is it a good idea to rely on a safe deposit box to store your digital wallet seed phrase backup? Unfortunately, the answer is a resounding “No.” Let’s consider why not.
Safe deposit boxes are disappearing
Many banks have phased out the availability of safe deposit boxes. In the United Kingdom, HSBC and Barclays have completely stopped offering safe deposit boxes. In the United States, JPMorgan Chase, Santander, and Capital One have stopped offering new safe deposit boxes, while Bank of America and Citibank have also reduced their availability. Among the reasons for this trend: declining demand, high maintenance costs, and regulatory challenges. The chart below reflects these startling changes.
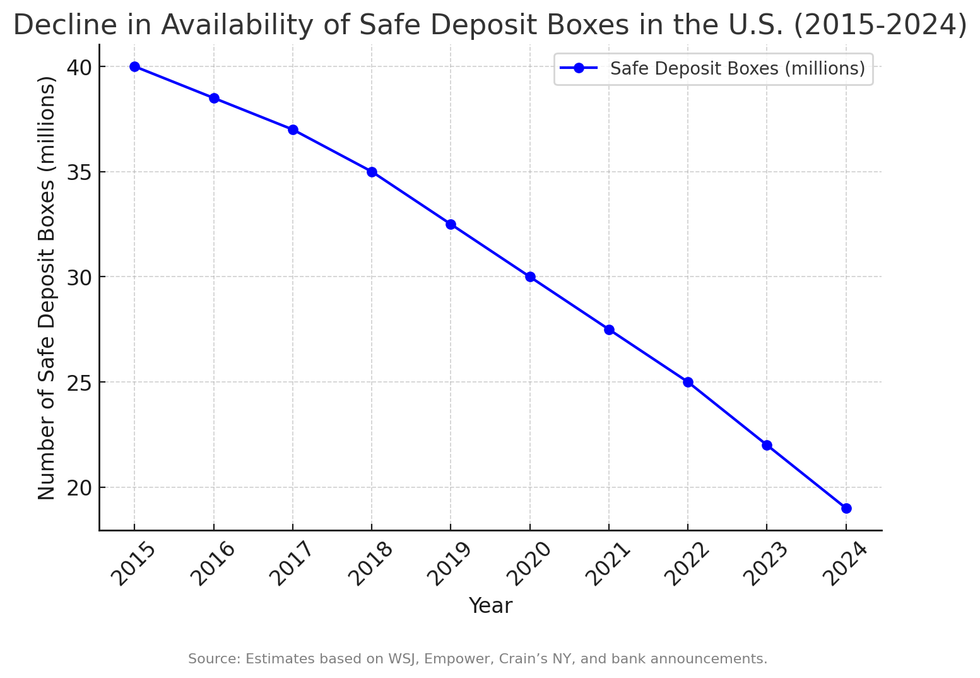
Fewer and fewer safe deposit boxes are available
ChatGPT
Safe deposit boxes are subject to theft
In 2015, a Citibank safe deposit box in Sherman Oaks, California was mysteriously emptied of over half a million dollars worth of valuables — and surveillance cameras only covered the vault entrance, not individual boxes. In 2017, a Brooklyn Santander bank branch was broken into from an adjacent basement, and crooks made off with the contents of about 50 boxes. And from 2020 to 2023, safe deposit box customers at MUFG Bank in Tokyo had valuables stolen by a bank employee! (In this case, the customers were repaid by the bank.)
Safe deposit boxes are subject to natural disasters
Natural disasters do not spare safe deposit boxes. Hurricanes in the United States (Katrina in 2005 and Harvey in 2017) led to many lost and damaged safe deposit box valuables. Earthquakes have resulted in safe deposit box losses in Japan and New Zealand. Fires destroyed the contents of safe deposit boxes in Australia (2019/2020) and California (during several years including 2025), after the boxes essentially became high-temperature ovens. In cases of extreme physical disaster, sometimes the only possible safety is being in a different location.
Safe deposit boxes can be legally seized
If a safe deposit box custodian is presented with a legal claim to freeze or seize the contents of a safe deposit box (for example, if there is a suspicion of illegal activity), law enforcement will assume custody of the contents as permitted by the relevant jurisdiction. Sometimes, depending on a warrant’s scope, many boxes can be opened even without specific individual warrants.
Safe deposit boxes aren’t insured
Many people assume that safe deposit boxes are insured by default — but they’re not! In the United States, neither the FDIC nor the National Credit Union Administration insures them.Some private insurers will cover them with special policies, but you have to specifically seek them out and pay extra for them — and carefully analyze the fine print about valuation, exclusions, and policy limits.
Safe deposit boxes aren’t always accessible
Banks aren’t always open for business. Beyond expected “business hour” limitations, banks can be unexpectedly closed for various reasons, including pandemic responses. If a bank that holds safe deposit boxes finds itself in a legal dispute or financial failure, although the contents of the safe deposit boxes are not considered bank assets, access to the boxes may be temporarily blocked while administrative proceedings unfold.
Additionally, if a safe deposit box owner passes away, special access rules (varying by region) come into play, and a spouse or the executor of a will may not be permitted to access a safe deposit box — even if they have the key and PIN.
A Digital Vault is safer and more convenient
A better solution is to use a secure Digital Vault like Vault12 Guard. The Vault12 Digital Vault fulfills and exceeds all of the secure digital storage requirements that a physical vault offers … without the limitations or third-party risks. Vault12 Guard takes the form of a simple-to-use mobile app that can protect all of your digital assets in a highly-secure, decentralized manner, monitored by Guardians of your choice.
A Vault12 Digital Vault is secure and always-accessible
The Vault12 Digital Vault is more secure than a safe deposit box, safe from natural disasters due to its decentralized design, always accessible, and its Digital Inheritance feature is simple for your next of kin to use when the time comes.
View the Vault12 Guard demo and download a trial today
Check out an overview with demo to see how the Vault12 Digital Vault works. Learn more on the Vault12 website. When you’re ready, you can get started with your Digital Vault in just a few minutes.
$6 Trillion of Crypto Assets to Be Inherited by 2045
How will you manage your crypto inheritance?
Over the next two decades, up to $6 trillion in crypto could be inherited, as younger investors favor digital assets over traditional stocks and bonds. Learn how this shift is reshaping wealth transfer and the future of investing
Unprecedented Asset Transfer via Inheritance by 2045
A recent report, the 2024 Bank of America Private Bank Study on Wealthy Americans, reveals key trends related to inheritance, and particularly how younger generations view the future of wealth, including crypto and estate planning.
An astounding $84 trillion of wealth transfer is projected over the next 20 years from current generations to Gen X, Millenials and Gen Z. Renowned expert Matthew Sigil, head of digital assets research at Van Eck (a prominent issuer of Bitcoin ETFs) has estimated that of this amount, $6T in crypto assets will be passed on via inheritance.
This transfer will be successful only if care and attention are paid to crypto inheritance planning and management, and if the right approaches are in place to support the technical transfer of these funds. Crypto assets are technically different in a number of ways to traditional assets, so inheritance needs to be carefully choreographed between asset owners, Trust and Estate Lawyers, and intended crypto beneficiaries.
Despite the fact that important steps must be taken for the safe, secure, and private transfer of crypto assets, none of the participants in the crypto ecosystem have offered inheritance plans or services. The pioneer of crypto inheritance management since 2015 has been Vault12.
Vault12 has built and continues to innovate a comprehensive solution that is easy to use for non-technical participants, yet incorporates a highly secure architecture and technology that is designed to preserve your crypto wealth and ensure successful transfer to your heirs. Learn more at vault12.com.
The Bank of America Private Bank Study
This report by Bank of America Private Bank analyzes financial outlooks, investing habits, and estate planning practices of wealthy Americans. The study reveals a generational divide, with younger wealthy individuals exhibiting different investment preferences than older generations. Younger individuals tend to be more skeptical of traditional investment strategies, and favor alternatives like cryptocurrencies and private equity. The study highlights the challenges facing wealthy families as they navigate wealth transfer, including the emotional strain of inheritance and the increasing burden of serving as trustee or executor.
Takeaways
- Great Wealth Transfer: Approximately $84 trillion is projected to transfer from seniors and baby boomers to Gen X, millennials, and their heirs by 2045.
- Crypto Inheritance Surge: Matthew Sigel of VanEck Investments estimates that up to $6 trillion could enter the crypto market through inheritance in the next 20 years.
- Investment Shifts: Millennials and Gen Xers will inherit $84 trillion, with a growing proportion of cryptocurrencies.
- Young Investor Participation: To reach the $6 trillion estimate, young investors (ages 21-43) need to allocate 14% of their inherited wealth to crypto: about $300 billion annually.
- Broader Investment Preferences: Many young investors view traditional stocks and bonds as insufficient for superior returns, preferring high-growth assets like cryptocurrencies.
- Risk Appetite by Generation: Younger investors show a higher risk tolerance, with significant crypto allocations (14%-17%) compared to older investors, who remain conservative.
- Crypto Exposure: Younger investors hold the highest average exposure to crypto, highlighting a shift in how the next generation approaches digital assets.
Sources:
2024 Bank of America Private Bank Study of Wealthy Americans
VanEck: $6 Trillion Could Pour Into Bitcoin, XRP and Crypto via Inheritances Over 20 Years
Crypto and Digital Asset Allocations
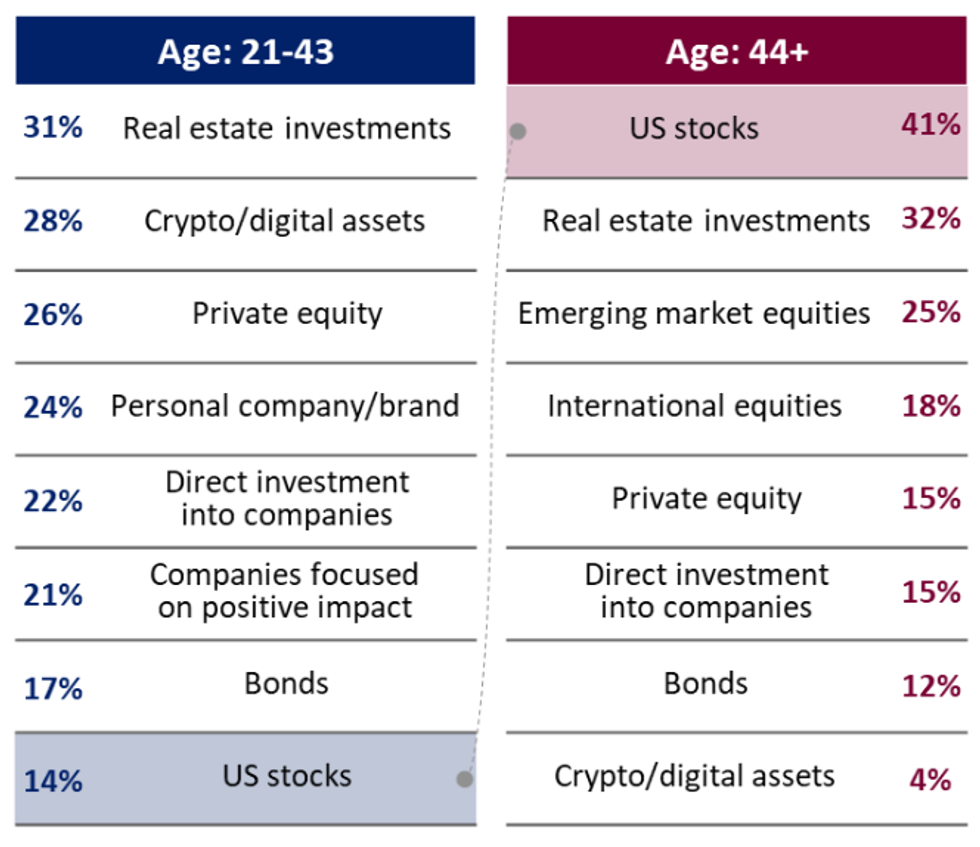
Bank of America 2024 Private Bank Study on Wealthy Americans
Crypto, Inheritance, and Wealth Management in Younger Generations
The 2024 Bank of America Private Bank Study on Wealthy Americans focuses on several key trends related to inheritance, particularly how younger generations view the future of wealth, including crypto and estate planning.
1. Crypto and Digital Assets
Younger generations (ages 21-42) are more inclined to see digital assets like cryptocurrency as a key growth opportunity. Around 28% of younger respondents ranked crypto as a promising investment vehicle, significantly higher than older generations, where only 4% expressed the same confidence. This highlights the generational shift towards embracing newer financial instruments like blockchain and decentralized finance.
2. Inheritance and Estate Planning
Interpersonal family dynamics can create tension during wealth transfers. For both younger and older wealthy individuals, unequal distribution of assets and a lack of clear instructions or communication were common sources of strain. Younger generations are more focused on including hard assets like jewelry and heirlooms — which are frequently overlooked in formal planning — in their estate plans.
3. Generational Differences in Wealth Management
Younger heirs are more likely to pursue alternative investment strategies, such as private equity and digital tools, reflecting their broader interest in controlling their wealth. These individuals also prioritize sustainability and impact investing as part of their inheritance planning, distinguishing their approach from older generations.
These insights demonstrate the ongoing generational divide in attitudes toward wealth management and the evolving role of digital assets in estate planning.
Inheritance and Estate Planning "Strain Points"
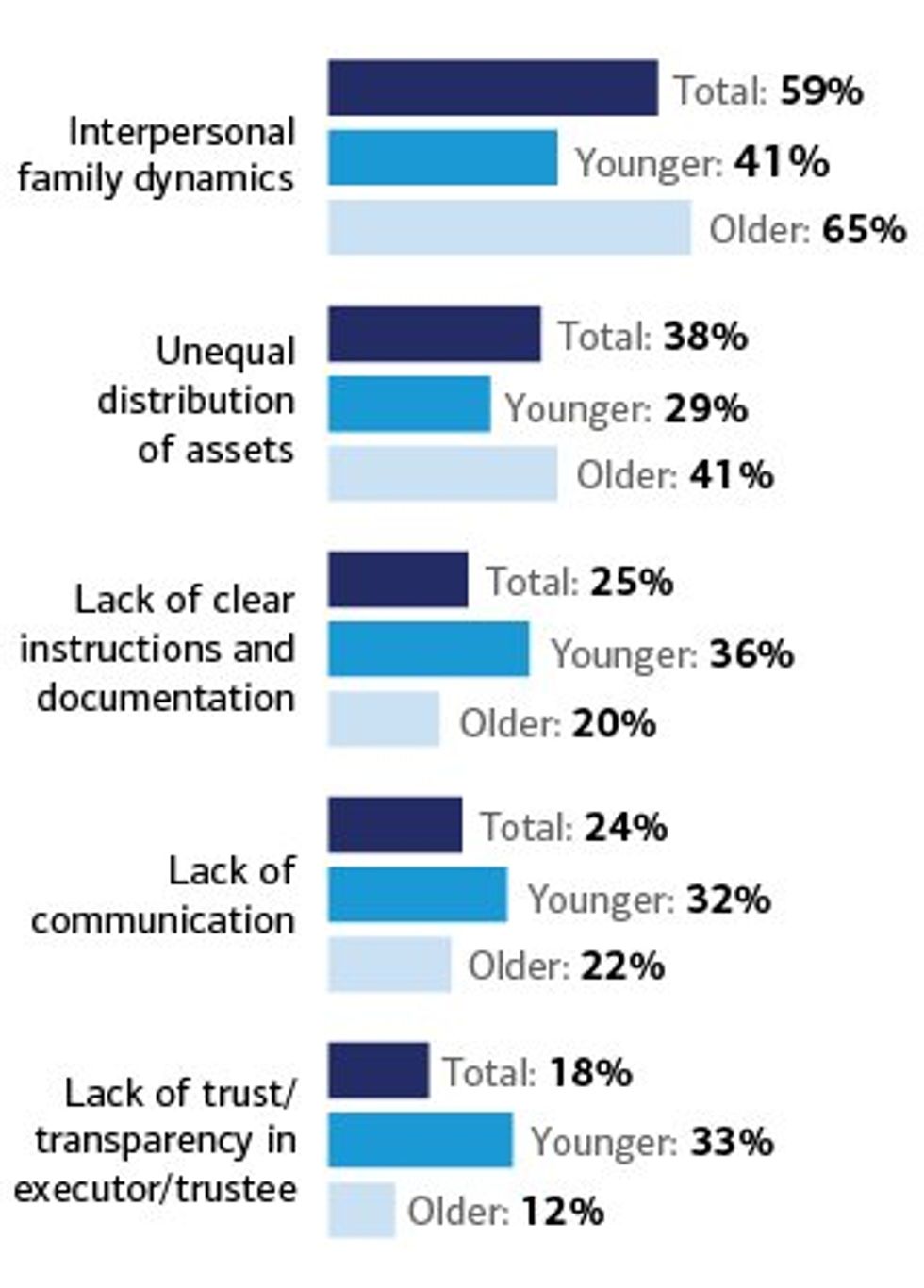
Factors driving strain on inheritance-related issues
Bank of America 2024 Private Bank Study
What you need to know about Crypto Inheritance Planning
Unlike traditional assets, crypto assets need to be managed differently from an inheritance standpoint. In fact, the only similarity between traditional and digital assets is that you must maintain an update inventory of them. The main challenges associated with crypto inheritance are:
- Inventory of crypto assets: You must carefully maintain an inventory of crypto assets. This means backing up seed phrases and/or private keys of all crypto wallets, across all blockchains, and all types of devices or places where those wallets exist, e.g., mobile phones, hardware wallets, cloud, and paper backups. Any assets that are not documented in your backup are liable to be lost.
- Privacy of all information: You must ensure absolute privacy of the backup information. Anyone with access to private keys or seed phrases will be able to compromise the funds. This includes ensuring that any documentation left with your lawyers is strongly protected.
- Critical Points of Failure: You must eliminate personal devices and cloud services as critical points of failure. The most significant risk in inheritance is reliance on individual devices, which can be stolen, lost, or damaged. The second risk is the dependency on one or more cloud servers. We have seen what happens when business relationships between cloud partners face legal challenges, or cloud services are disrupted by malware or bad software updates.
- Technical Beneficiary awareness: As the varieties of crypto assets expand over time, staying aware of them becomes important. You will need to designate someone technically fluent in this area. They may not be the ultimate beneficiary; however, you will need to trust them to distribute the assets per your wishes.
- Trust & Estate Attorney: You must consult with experienced lawyers who are well versed in inheritance of crypto assets. A great resource is "A Practical Guide to Estate Administration and Crypto Assets" by Richard Marshall from Hill Dickinson LLP.
Why Choose Vault12 Guard for Crypto Inheritance Management?
Vault12 is the pioneer of crypto inheritance management, and Vault12 Guard is the first solution to offer a simple, direct, and secure way for all types of investors to ensure that all of their crypto assets can be accessed by future generations.
Consider that:
- Traditional approaches to the inheritance of assets, when applied to digital assets, create complexity and risk.
- Your portfolio of digital assets is continually changing — you cannot rely on doing an inventory once, or for that matter continuously, without assistance.
- A simple and direct approach like Vault12 Guard reduces the uncertainty around assets not being available to the designated recipient. It also avoids having to approach and petition each service individually during probate to gain access.
- Inventory of crypto assets: The first step in inheritance is backing up all your crypto wallets. Vault12 makes this as easy as possible - despite the appalling lack of usability in current hardware and software wallets. There will always be new crypto assets on new blockchains, and Vault12 can manage any crypto asset on any device, on any blockchain, now and in the future.
- Privacy of all information: Your crypto assets are protected via a Secure Element (Secure Enclave in iOS, and Strongbox on Google Android phones), and the encryption used is Quantum-safe. With this security, no one knows what assets are part of your Vault.
- No Critical Points of Failure: No assets are stored locally, no assets are stored in any cloud, and no assets are stored at Vault12. There are no devices to lose, no paper backups, and no need to manually give encrypted assets to a subset of people. The Vault12 system is decentralized, making it a difficult target for hackers — and in fact for any type of failure.
- Confidence in a Technical Beneficiary: With Vault12 you get to designate a trusted technical beneficiary. Should you change your mind, you can swap them out at any time.
- Flexibility in Trust & Estate Attorney: While regulations and guidelines for inheritance planning can vary from state to state and country to country, Vault12 Guard is designed to be independent of whatever legal framework you choose to govern the inheritance of your assets. Vault12 Guard is simply a transfer mechanism that ensures all your crypto assets are passed from your control to a designated technical beneficiary.
Key Product Features of Vault12 Guard
The Vault12 platform provides your crypto assets with the highest security and strong backup resilience. Vault12 Guard Inheritance enables you to designate a beneficiary (an executor, trustee, or other chosen beneficiary) who can inherit the entire portfolio of digital assets that you choose to store in your Vault. There is no need to update an inventory continually or to issue updated instructions.
- Unified Digital Vault: Use Vault12 Guard Digital Vault to store digital assets, including cryptocurrency, financial login information, legal documents, medical records, and more.
- Guardian Network: The Vault is protected by your network of Guardians: friends, family, and/or business associates — people that you know and trust.
- Beneficiary Designation: Designate a beneficiary from your chosen Guardians. A declaration is then digitally signed, and can be emailed to other parties, such as lawyers.
- Trigger-Based Access: As a Vault Owner, you can configure a legally-defined trigger such as incapacitation or death. When the trigger occurs, the beneficiary indicates they are ready to access the digital assets. Assets are unlocked and transferred to the beneficiary only when a designated number of Guardians approve the request.
- Preemptive Veto Option: Should the beneficiary attempt to access the assets before they are intended to, the owner can veto the request before any of the Guardians receive an approval request.
.
Crypto Inheritance Planning vs. Traditional Estate Planning
Both types of planning work hand in hand to protect your digital and traditional assets
Crypto Inheritance Planning is a specialized subset of general estate planning that deals with the unique challenges of digital assets such as crypto wallets, cryptocurrencies, NFTs, and other blockchain-related assets. As you invest more in these assets, planning for what happens to them when the time comes is just as important as planning for traditional assets.
Why Crypto Inheritance Needs Special Attention
Crypto assets don’t work the same way as traditional financial assets when it comes to inheritance, nor are they like physical assets.
- Traditional financial investments usually include a beneficiary as part of the financial institution account: institutional processes will manage inheritance distribution.
- Physical assets might be located on your property (or even at a marina, stable, or airport), and are often registered or insured in your name, leaving a clear “paper trail” of ownership. Generally, your beneficiaries are aware that you have them, and they will be easily discoverable when you eventually pass. These assets will be sold or distributed among your beneficiaries according to your wishes as expressed in your will.
- Crypto assets are generally not discoverable by others unless you make a specific effort to make them so. This is why making an inventory of your crypto assets and setting up a plan to redistribute them as part of your inheritance plan is so critical.
For each asset type, you should consult with experts to consider legal and tax issues relative to transferring ownership of the assets when needed.
For crypto assets, you also need to consider the security of your digital holdings while you are still alive, and a safe mechanism for transferring access to your crypto wallet after you pass. This is where Vault12 Guard can help you.
Legal and Tax Considerations
Crypto inheritance is affected by many of the same jurisdictional issues that affect traditional inheritance, such as laws surrounding wills, probate, and executors. Depending on your area, rules on taxes and transfers can affect how your crypto assets are inherited. This is why it’s crucial to consult legal, financial, and tax professionals who understand both traditional and crypto-specific inheritance planning. They can help you navigate those rules and make sure that your plan is both effective and legally compliant.
Security Before and During Inheritance
You already know that you need to keep your guard up to protect your crypto investments while you are alive. There are risks seemingly around every corner! One of the unique risks to cryptocurrency holdings is that you should not trust anyone or any institution with seed phrases to your crypto wallets while you are alive. Also, due to several types of threats, your privacy is of utmost importance - you don’t want many people to know that you have crypto holdings.
How can you keep your seed phrases secret from everyone, yet still make them securely available to your beneficiary after you pass? Vault12 Guard solves that problem.What to Consider in Your Crypto Inheritance Plan
Be sure to cover these steps when adding digital assets to your estate planning:
1. Consult inheritance experts: Choose an estate planner or inheritance professional who knows crypto. They can guide you through the following:
a) Tax implications of digital asset transfers.
b) Legal frameworks that govern the inheritance process for digital assets, including how trusts and sales of these assets might affect beneficiaries.
2. Consider your need to secure and protect your private keys and/or seed phrases: These are the gateway to your assets, so keep them secure.
3. Consider your need to document your digital assets: When you implement your inheritance plan, you will need to create a detailed inventory of all your assets including every wallet and other blockchain-related holdings. For NFTs, you will need to make sure both wallets and original media files are backed up.
4. Include a technically-minded beneficiary. Choose someone you trust who can manage the technical aspects of accessing and potentially transferring the assets in your wallets. You might have a simple scenario where you store a small number of wallet seed phrases (which might not require a particularly advanced technical beneficiary). But your crypto holdings might be complicated, or sprawl across multiple platforms. Each individual situation is unique.
Crypto inheritance planning is an essential part of securing your digital legacy which is better done sooner rather than later. By planning now, you’ll avoid costly mistakes, and gain peace of mind from knowing that your assets will be conveniently passed on as you intend without risk or confusion.
Backup
Vault12 Guard provides inheritance, and secure decentralized backup of seed phrases and/or private keys, giving Bitcoin (BTC), Ethereum (ETH).
View all articlesHow To Back Up Your Crypto Wallet
Backing Up Your Crypto Wallet With Vault12 Guard Preserves Your Personal Crypto Security
Crypto can be difficult to store securely, but backing up your crypto wallet is essential so you can recover funds if your crypto wallet is ever lost, stolen, or damaged. A proper crypto wallet backup is also important for inheritance purposes so your assets live on, even after you die.
Why should you back up your crypto wallet?
Proper crypto wallet backups protect you from threats ranging from criminal actors and accidents to natural disasters and damage. Once securely backed up, you can recover your assets in times of need.
A proper backup of your crypto wallet involves recording:
- Each crypto wallet asset
- Seed phrases and passphrases
- Any supporting files for your assets
All crypto backup solutions should be physically secure, digitally secure, and resilient to degradation – but unfortunately, not all of them are.
What are some limitations of common crypto backup methods?
These are some common backup methods, but each has drawbacks:
- Back up to metal plates - This method sounds simple, but to do it right takes some planning, cost, and time.
- Back up to a local drive - This method is quick, but fraught with risks!
- Back up to the Cloud - This method is also quick, but it has significant risks related to the involvement of third parties.
- Back up to “brain wallet” - This method is slow, unreliable, and only justifiable in cases of extreme limitation or duress.
- Back up to paper - This method is extremely vulnerable and surprisingly subject to error.
How does Vault12 back up your crypto wallet?
The video demo below shows you how Vault12 Guard is used to back up a crypto wallet, making sure your assets live on, even after you pass:
YouTube
Vault12 Guard crypto backup is decentralized, resilient, and secure.
Vault12 Guard allows you to breathe easy, as it avoids the pitfalls of other backup methods:
- Guard's backups are decentralized. There is no single point of failure, allowing you to recover even if your phone is lost or stolen.
- Guard does not rely on Cloud servers. Your assets remain private from third parties and resilient to Cloud outages.
- Guard implements post-quantum encryption - giving your assets the highest possible level of security.
Vault12 Guard is the most advanced yet simple crypto backup solution
Not only is Vault12 Guard secure and resilient, but it is also simple to use. It allows you to back up all types of wallets, as well as NFT-related files, to construct a full inventory of your crypto assets. This includes multi-wallet management, which Vault12 simplifies with an integrated backup and inheritance solution. When you need to restore your Vault, Vault12 makes the process easy by requesting access from your most-trusted Guardians.
Of all your choices for backing up a crypto wallet, Vault12 Guard uniquely backs up your crypto wallets in a manner that is physically secure, digitally secure, and passes the test of time.
Risks of backing up your seed phrase on paper.
Paper is inherently vulnerable as a medium for long-term storage of any information - but the risks can be somewhat reduced if you counteract its weaknesses.
Cryptocurrencies are fueling a fundamental financial shift by allowing individuals to use cryptography to secure their own digital assets. Surprisingly, given the criticality of keeping safe backup copies of the encryption keys that control access to these digital assets, most cryptocurrency holders rely on paper as their chosen medium to back up their cryptocurrency access keys.
TL;DR (concentrated takeaways)
Paper backups of seed phrases are subject to a large array of threats, including loss, theft, and destruction.
Relying on paper backups is the leading cause of lost crypto assets.
Even safe deposit boxes may not fully protect paper backups.
Certain precautions, such as added physical protection, and having an equally-secure copy in a different location, can make paper backups less vulnerable.
Paper is a popular default backup medium because it is convenient for both consumers and wallet manufacturers. The use of paper to back up the all-important "seed phrase," or "private key," was for some years the assumed de facto backup mechanism described by cryptocurrency wallet manufacturers. In a survey of the 20 top wallets, 18 of them offered only one mechanism to back up the seed phrase: to write it down on a piece of paper and store it securely. The other 2 wallets surveyed also provided a paper backup option, and added the ability to generate an encrypted digital copy to be kept in a location such as a USB device, off-network laptop, or in the Cloud.
If you must write down your seed phrase or private key on paper, please do it temporarily, then use one of these methods to create a reliable backup, and then destroy the temporary paper backup. This article explains why these steps are necessary to preserve your investment.
The weakest link in crypto.
Storing your valuable backup key or seed phrase on a piece of paper carries unique risks for the crypto owner. Paper is delicate, and its threats include:
- Gradual deterioration of legibility over time
- Catastrophic destruction due to natural disasters like floods or fire
- Accidental destruction by insects, animals, or people
Additional threats that are common to nearly all forms of backup include:
- Loss or misplacement
- Theft
- Lack of awareness of backup location to family or heirs
The list of threats can go on and on. While designed with good intentions to protect crypto owners' assets from loss, paper backups actually have become the leading cause of lost crypto assets. Having a paper backup creates a false sense of security, because when an unplanned event causes a loss of the user's main wallet, they realize they do not remember or cannot access the paper backup they thought they had. As the number of cryptocurrency owners grows, this problem, with its devastating losses and resulting customer dissatisfaction with securing cryptocurrency assets, is also growing — with users often directing blame at wallet vendors.
The lesson of how fragile paper backups are was recently learned by the many residents of Los Angeles, California, as they had to evacuate their homes quickly to escape rapidly-spreading fires. How many left their paper crypto seed phrase passwords behind?
Risks of using Paper backups.
| Paper backups and wallets are often kept in the same location and are therefore subject to the same risks as the owner's main wallet: fire, natural disasters, burglary, etc. | |
Casual owners are likely to forget the "secret storage location" of their piece of paper after few years. | |
In the case of an owner's accidental death, there is no way for their inheritors to recover the assets, which in the case of cryptocurrency keys makes those assets permanently inaccessible. | |
By nature, paper is not a long-term storage medium, and can easily become unreadable after years through natural wear and tear. | |
Casual users are confused about the role and function of paper backups and often blame the wallet vendor for any incidents regarding wallet backup and recovery. That creates a significant load of unresolvable cases for customer service and increases customer dissatisfaction with the wallet brand. | |
Further, in financially-unstable countries where cryptocurrency ownership is crucial, access to bank safe deposit boxes (a common storage location for paper backups) is often restricted during any bank crisis, exactly when users might need immediate access to their crypto-assets. | |
Inheritance.
Beyond restoring cryptocurrency access that may have been lost in a damaged wallet, one of the times when a seed phrase backup is most desperately needed is in the event of inherited crypto assets. Sadly, there have been many instances when the inheritor has been unable to access assets after the owner has passed away, because no one knows about any paper backup copy.
What can be done to reduce risk to Paper Backups?
If a cryptocurrency owner chooses to store their backup seed phrase on paper, they should at a minimum take care to:
- Ensure that when they wrote the seed phrase down, their writing was not captured on camera, and any underlying pages in a pad were not imprinted from writing pressure.
- Carefully destroy (for example, by burning) any temporary or interim copies that they may have created while producing a permanent paper copy.
- Carefully ensure that no electronic copies remain on computers or printers that were used in generating the seed phrase, key, or QR code representation on paper. (This may require expert assistance.)
- Understand the expected durability of the pen, pencil, or printer ink chosen. (Pencil is often recommended.)
- Laminate the paper copy with waterproof, fade-proof, high-quality plastic.
- Ensure physical safety of the backup paper in a vault. Consider keeping a second copy in a separate, equally-secure vault.
- Let at least one other trusted person know about its existence.
Even if the protections above are followed, paper backups have limited reliability.
A better way.
Some crypto owners will not understand why they can't simply rely on the convenience of recoverable passwords like those used in traditional banking services. In the near future, as more types of transactions occur on blockchain networks, the security levels that we expect for today's cryptocurrency storage will also apply to fully-digital house keys, car keys, real estate titles, and a variety of personal property and documents that are currently secured by cryptographic keys. A better solution is needed to bring security and backup options to consumers at the forefront of this digital economy.
How to securely destroy your paper seed phrase backup.
You should remove all traces of temporary seed phrase backups.
TL;DR (concentrated takeaways)
You should not keep any temporary paper copies of your crypto wallet seed phrase.
The Vault12 Digital Vault is perfect for permanently and safely storing your seed phrase backup.
Disposing of your temporary paper seed phrase is easy, but the details are very important.
You could dispose of it by burning it in your kitchen, and then flushing the ashes.
You could dispose of it by erasing, shredding, and then flushing the pieces.
Remember that your wallet seed phrase allows access to your crypto
By now, you know that your crypto wallet seed phrase is the most important thing to protect in order to guard your crypto assets. You have read about the need to use randomness to generate your seed phrase, and then how important it is to back it up to ensure that it is not lost or stolen. In this article, we will assume that you have already decided on which wallet to use, how to generate your seed phrase, and how to back it up. With your wallet set up and your seed phrase safely and permanently backed up, now you find yourself with a piece of paper that holds a "spare copy" of your seed phrase scrawled on it. How should you dispose of that precious piece of paper?
Why would you have a paper copy of your seed phrase?
You probably ended up with that piece of paper containing your seed phrase as a result of your seed phrase generation and/or wallet setup steps. Until you are sure that your wallet configuration is complete, and your permanent seed phrase backup is complete, you likely wrote down your seed phrase on paper along the way.
If you generated your seed words incrementally with dice, you likely calculated them one by one, capturing each one on paper after it was chosen.
Similarly, if you let a crypto wallet choose your seed phrase for you, you likely wrote it down in order to confirm the words back to the wallet during the configuration process. In any case, you probably did not transcribe each word directly into permanent storage the instant that it was generated - you wrote it down offline, on paper, in order to have a copy to use to help you complete the steps of saving it to its permanent storage medium. Then you saved your seed phrase to a permanent medium such as your Vault12 Digital Vault, a steel card, or a limited-access, backed-up encrypted file. You might even have chosen to use two of those forms of secure, permanent backup.
Congratulations! But now you also have this extra piece of paper that you don't need - and it would be silly to leave it lying around waiting to be stolen, or to just throw it into your trash can.
Planning to destroy your temporary seed phrase copy
You need a foolproof way to destroy the now-unnecessary, temporary paper copy of your wallet seed phase, such that it can never be reconstructed. Here are some things to keep in mind as you plan to destroy it:
- Don't put the task off. If you do not keep the temporary copy in a high-security safe until it is destroyed, every moment that it remains readable holds some risk that you could misplace it, or that it could be otherwise accessed. Properly disposing of it is not hard to do, and it does not take long - finish the task.
- Meanwhile, be aware of cameras that could record the seed phase from the paper. Your smartphone, laptop, tablet, or security camera could all capture an image of your seed phrase without your realizing it. We have all become so accustomed to cameras around us all of the time, especially when they are part of our home security system, that we lose our awareness of what is being recorded. Don't take the chance of accidental image capture.
- If you wrote down the seed phrase on a pad of paper, ensure that the page below the one that you wrote on does not have impressions that could be used to detect and reconstruct the words. Tap into your spy novel knowledge to imagine that possibility! If necessary, destroy the page underneath as well to remove all traces.
- Be absolutely sure that you did not make any errors in backing up your seed phrase to permanent storage.
Now you are ready.

Option #1: Destroy your seed phrase copy with fire and water
For all activities related to fire, you should of course carefully take appropriate safety precautions.
It is possible to burn your seed phrase outdoors, but we recommend doing it indoors, since indoor space is more controllable. (Outdoors, you may be more conspicuous, the paper could blow away partially-burned, or worst of all, you could accidentally start a larger fire.)
Indoors, you have a ready-made seed phrase burning area: your kitchen stove. When you are ready:
- Just in case, know where your fire extinguisher is located!
- Survey the area around the stove to ensure that there is nothing flammable.
- Turn on the ventilation fan near your stove to prevent setting off the smoke detector.
- Have a lighter handy.
- Put a metal pan that you will use to contain the burning paper onto the stove.
- Fold your seed phrase paper in half so that it makes a V-shaped "tent."
- Place the folded paper into the pan, pointy side up (as an upside-down "V") - this will allow oxygen to circulate underneath it for a complete burn.
- Carefully light the paper on fire, and wait for the flame to completely consume it.
- Wait for the paper to cool. Crumble the ashes.
- Flush the ashes down the toilet to avoid any chance of reassembly.
Option #2: Destroy your seed phrase copy by shredding and flushing
To destroy your paper seed phrase without fire:
- First, if the words are written with pencil, completely erase them.
- Shred the paper into extremely small pieces, such that even if any letters could still be read, no more than one letter would be shown on any piece. (This could be done using your hands, scissors, or a shredding machine.)
- Flush the shredded pieces down the toilet to avoid any chance of their reassembly.
Your Vault12 Digital Vault is secure and convenient for your seed phrase backup
It is a good feeling to know that your seed phrase is safe and secure without having to keep paper copies lying around. Your Vault12 Digital Vault is the perfect place to store your sensitive digital assets including your seed phrase. Congratulations on being an informed, responsible holder of your own crypto assets.
How to back up a Seed Phrase
There are many ways to back up a seed phrase. This article summarizes for you the advantages and disadvantages of each method.
A seed phrase, or recovery phrase, is a sequence of words that a cryptocurrency wallet uses to access your cryptocurrency holdings. Securely backing up your seed phrase is a very important step, because knowledge of the seed phrase effectively serves as ownership of funds.
Cryptocurrency wallet documentation often offers limited advice about best practices to securely back up your seed phrase. A common recommendation made by wallet providers is to write down your seed phrase on paper and then store it in a safe place — but in itself, this is not sufficient protection.
For example, the official documentation on managing a Coinbase Wallet highlights the importance of securing your seed phrase but lacks detailed guidance, particularly on security options. We offer comprehensive guides on how to protect a Coinbase seed phrase, a Trust Wallet seed phrase, and other crypto seed phrases to keep your digital assets secure.
TL;DR (concentrated takeaways)
Securely backing up your seed phrase is the most important thing you can do to keep your crypto safe.
You must consider 3 things: physical security, data security, and time-driven deterioration.
Backup options include:
- Digital Vault
- Cryptosteel
- Local computer drives
- Cloud storage
- Multi-signature solutions
- "Brain wallets"
- Paper
What criteria make a seed phrase backup secure?
To be secure, a seed phrase backup should strongly satisfy the following 3 criteria:
Physical security
Where will your seed phrase backup be kept? The location where the seed phrase is stored is very important, and a seed phrase written on a physical medium like paper is very hard to secure. When picking a location, consider who has access to it. Your seed phrase backup should be stored in a secure location, accessible by only you. Physical security also implies that you will not lose or forget its location - don't hide it so well that you forget how to find it again. And even if you won't forget where your home vault is located, it might not be as findable as you expect if your house is subject to a rapid natural disaster like a wildfire, tornado, or tsunami. It is hard to contemplate, but your home could be destroyed quickly and unpredictably, with your safe lost in the chaos. Unfortunately, residents of Los Angeles were faced with wildfires, rapid evacuation, and delayed returns to their charred homes in early 2025. There is no definitive count, but certainly some lost their crypto wallet backups in the devastation.
Data security
Data security is usually accomplished via a locked safe or encryption. This serves the purpose of protecting your seed phrase even if bad actors find out where it is. As long as a bad actor does not gain access to the key to your safe or your encryption keys, your seed phrase and your crypto will remain secure.
Passes the "test of time"
The test of time introduces two potential threats: gradual natural decay, and the cumulative risk of eventual destruction via various types of disaster or unexpected changes. Consider the risks that arise over time when formulating a backup plan that will protect your seed phrase. Electronic media degrades over time, writing can fade, and paper can mildew. A paper backup that is not secured in a fireproof, waterproof safe is vulnerable to both natural decay from the elements and destruction via disasters.
1. Back up to Digital Vault
Vault12 is a decentralized Digital Vault that offers a very high level of security in a user-friendly mobile app. To back up your seed phrase in your Digital Vault, simply open your vault, select "Add Asset," and enter your seed phrase. In addition to your seed phrase, you can store any digital asset.
Using Vault12, your seed phrase will be encrypted, then split up into encrypted shards, and distributed to your chosen network of Guardians. Your network of Guardians can be made up of multiple devices under your control, or a network of people that you trust. This forms a mesh network of encrypted storage.
The advantages of backing up your seed phrase with Vault12 are portability, complete privacy, the ability to self-manage your backup, and redundancy - if you lose your device, you do not lose access to your seed phrase.
This solution meets all three criteria for secure backup, learn more.
2. Crypto Steel
A highly secure way to back up your seed phrase is by permanently affixing the words to indestructible stainless steel or titanium metal plates. (Steel is more commonly used.) This approach passes the test of time, and if your house burns to the ground, your seed phrase will survive.
A few companies offer ready-made steel plates, where all you have to do is input your seed phrase onto the steel card by engraving or stamping the card with provided tools, or by sliding tiles into locking slots. If you are handy, you could even make a steel plate backup yourself.
Backing up to a steel plate is great, and avoids many of the risks of backing up to paper - but like any other physical medium, you must prevent unauthorized people from accessing the plate. Keep it in a safe place and consider encrypting the seed phrase before committing to steel.
This method is primarily subject to the risk of physical security.
3. Encrypted local drive / USB
Storing your seed phrase on a locally-stored encrypted drive offers a high level of data security since it ensures that only you have access to your seed phrase, but does not offer a very high level of protection against other risks.
Encrypting data is the digital equivalent of storing data in a physical safe. When you encrypt a local drive that holds your seed phrase, a key or password will be needed to regain access to it (depending on what tool you choose to perform the encryption). Do not store the encrypted drive and the encryption key together, and do not lose the key/password!
This option offers flexibility in the choices available for the physical drive, and the method used to encrypt its contents. Not all encryption is created equal - always make sure that you choose a standards-based and strong encryption protocol.
For example, you could password-protect your encrypted local drive that holds your seed phrase, and back up the drive's encryption password somewhere like Vault12. However, with this kind of backup strategy, when the encrypted drive physical media fails, your safely-secured password that would decrypt that failed drive would not reunite you with your cryptocurrency seed phrase. Be careful with complex backup solutions.
This method holds some risk of each of the three criteria of secure backup. Learn more.
4. Cloud storage
If you choose to store your seed phrase on physical media, it could be secure, but if you don't carry it with you everywhere (which would come with its own risks), you will be out of luck if you need it while away from home. Cloud storage gives you a much more accessible option. However, putting your unencrypted seed phrase on a Cloud drive is absolutely not secure. You must encrypt the seed phrase first - that way, even if someone is able to access the file on the drive, it cannot be used.
The most significant risks related to cloud storage of an encrypted seed phrase are related to the loss or unintended disclosure of the encryption password (data security). Learn more.
5. Multi-Signature solutions
There are various multi-signature, or "multisig" key backup solutions available. Multisig solutions are a challenge because they are both complex and varied in form, operating differently on different blockchains. They can add significant security if carefully implemented, but they introduce risk tradeoffs related to having more moving parts, being more difficult to understand, and delegating trust to other parties. The term "multisig" is applied to many different implementations of solutions that involve multiple keys, and in practice, there are many subvariants of multisig solutions, each with strengths and weaknesses. Thus, multisig is not inherently a "good" or "bad" solution, but a complex and evolving basket of them.
6. Brain Wallet
This is by far the riskiest form of backing up your seed phrase. If you forget your seed phrase, you have to rely on your memory to retrieve it. When relying on human memory, there is a high likelihood over time that even you will be locked out from accessing your seed phrase. The benefit is that the process is completely offline (at least until Elon Musk is able to hack the human brain). Proceed with extreme caution.
If you plan to go down this route, it is a good idea to use a mnenomic of some sort, like a poem or a song where each word in your seed phrase represents the first line of the poem or song. This can help with memorization.
If you have a photographic memory, and you have never forgotten anything in your entire life, you could think of using your brain to backup your seed phrase. To do this, simply memorize your seed phrase. Of course, there is still a risk that you will someday suffer a brain injury, mental illness, or form of dementia that would cause you to lose your memory of your seed phrase.
This method has such a high level of risk from the "test of time" criterion that it must be stated twice - proceed with extreme caution. Learn more.
7. Paper
The most common method of backing up your seed phrase is using paper. The guidance provided with many wallets counsel you to write your seed phrase on a piece of paper, however paper alone is not a secure method. If you really want to use paper, it is necessary to take extra safety precautions. The paper your seed phrase is written on must be stored in a locked safe, at the very least.
This method holds some risk of each of the three criteria of secure backup. Learn more.
How to back up your seed phrase on Cryptosteel.
A highly secure way to backup your seed phrase is by recording it onto indestructible metal plates. This type of backup strategy is one of the most likely to pass the "test of time."
TL;DR (concentrated takeaways)
Backing up your seed phrase to steel plates offers a robust solution that is subject to only a few threats.
Don't give a steel plate vendor your seed phrase to stamp or engrave for you! This is a "DIY" task.
Once created, protect it well from discovery and theft.
Some options are Cryptosteel, Ledger CryptoSteel Capsule, Crypto Key Stack and Hodlinox (engraveable options), ColdTi (titanium), and Billfodl.
When it comes to a decision about how to back up your seed phrase, you have to consider your personal circumstances, and weigh the pros and cons of the many options that exist.
For offline, long-term, cold storage backups, utilizing steel is one of the most secure options. Steel requires no software, is nearly indestructible, and the backup process is completely manual and offline. Furthermore, the steel devices that are on the market today don't look like a seed phrase backup to those not already familiar with crypto seed phrases - this offers a degree of "security through obscurity" that could deter a common thief. (However, you should not rely on that protection! Always keep your backup in a safe or lockbox.)
Steel backups exist in a variety of formats. If you are handy with metalworking, you could even create a steel backup yourself. This review showcases Cryptosteel, which is produced from the original blueprints of the open-source Cryptosteel steel backup solution that was the first metal backup solution on the market. Cryptosteel sells its original model as the Cassette and has since added a Capsule version. Since the blueprint is open-source, the "cassette-type" steel wallet backup solution may be available from a variety of providers. If you consider several different steel backup solutions, consider the quality of each before making a purchase, since the place of manufacture, the grade of steel, and other characteristics may vary.
How is the seed phrase recorded onto the card?
A few companies offer ready-made steel plates, and all you have to do is input your seed phrase onto the steel. Different companies offer different ways of doing this, from sliding metal tiles into locking slots, to engraving, or using a metal punch. If you are handy and have the tools, you can even make a steel plate backup yourself.
There are 2 rules that you must follow if you are considering using metal plates as a backup:
1. Simplicity is the win-win! Some solutions are way too complicated. Fewer pieces = less chance for failure.
2. You should never ever provide the card manufacturer with your private key or seed phrase for "engraving" or whatever process they use. Unfortunately, some reckless manufacturers expose their customers to this severe risk ... pease keep your seed phrase safe by avoiding them.
What risks are steel cards still subject to?
Backing up to a steel plate is great - but don't forget about the importance of keeping that plate in a safe location. There is no "data security" layer present on a steel plate, so it becomes critical to implement steps to prevent unauthorized people from accessing the seed phrase or steel plate.
- Consider encrypting your seed phrase before committing it to steel - that way if the plate is exposed, you still have a layer of protection.
- Keep it in a safe place! If the plate is exposed, then your seed phrase is exposed, and you become at risk of your funds being drained.
Why protect Your Seed Phrase?
In the world of cryptocurrency, you are your own bank, and with great power comes great responsibility. Public blockchain cryptocurrencies are run on open, permissionless systems, where transactions are irreversible. There is no credit card company or bank to call and dispute the charges.
Your seed phrase provides full access to your wallet, and because of this, protecting your seed phrase is critically important. You can think of your seed phrase as equivalent in legacy finance to someone having all of your online banking information. Anyone with your seed phrase can access your wallet, just as anyone with your online banking information can log in to your banking account.
Protecting/backing up your seed phrase serves two purposes: First, it backs up your Wallet, allowing you to reconstruct your wallets in cases of device failure, new devices, etc. Second, it secures your Wallet by preventing bad actors from gaining access to your seed phrase, which would allow them to steal funds.
What is the Cryptosteel
Cryptosteel was the first steel seed phrase backup solution on the market. The concept was developed in 2013, and the blueprints were later released as open-source software. The rectangle block resembles a cassette deck, as suggested by its model name "The Cassette." The frame is a little bigger than a credit card and will fit easily into your pocket (although the pocket is a poor choice of locations for safekeeping).
The purpose of steel backup solutions like Cryptosteel is to safeguard your seed phrase from extreme scenarios. The Cryptosteel Capsule will survive fire up to 1400C/2500F degrees, and the Cryptosteel Cassette up to 1200C/2100F. (For reference, a house fire is around 600C/1100F degrees.) It will survive physical damage from flooding, electric shock, corrosion, magnetic shockwaves, and extreme pressure.
The form of the device does not appear to the untrained eye as a seed phrase backup solution - it appears simply as a block of metal. However, someone who is familiar with the devices will recognize what it is. After you have backed up your seed phrase, choose a proper location for storage, such as a safe or a lockbox.
The device is made from 100% AISI 304 grade stainless steel - the Capsule form also incorporates AISI 303 grade steel - and the company says that it can go undetected by many scanners and metal detectors. Since tech is always advancing, this is not a safe long-term reliance if your objective is stealth and your threat profile involves entities searching your house with metal detectors. If this is the case, embed the device onto a stainless steel object, preferably inside a wall, and your Cryptosteel will become masked and invisible to metal detectors.
How to use the Cryptosteel
When you first open the Cryptosteel, you will notice that the instructions are printed on the inside top of the cardboard box, along with pictures for each step. The device and the engraved steel tiles are neatly embedded into cushions.
0. Cryptosteel Unboxing

Cryptosteel unboxing
Remove the Cryptosteel device from the box, and the plastic container holding the engraved steel tiles. Printed on the box, underneath the plastic container, is an outline that maps out where each letter can be found in the plastic container. Each box shows 2 letters because the engraved steel tiles have one letter on each side.
Do you notice the elongated box in the middle, with numbers and symbols? BIP39 seed phrases do not contain numbers and symbols, but BIP39 does support adding a passphrase to the end of your seed phrase: this is sometimes referred to as the 13th or 25th word. However, the steel wallet only has 24-word options to fill, so if you have a 25th word, it won't fit. If you have a 12-word seed phrase, it will fit.
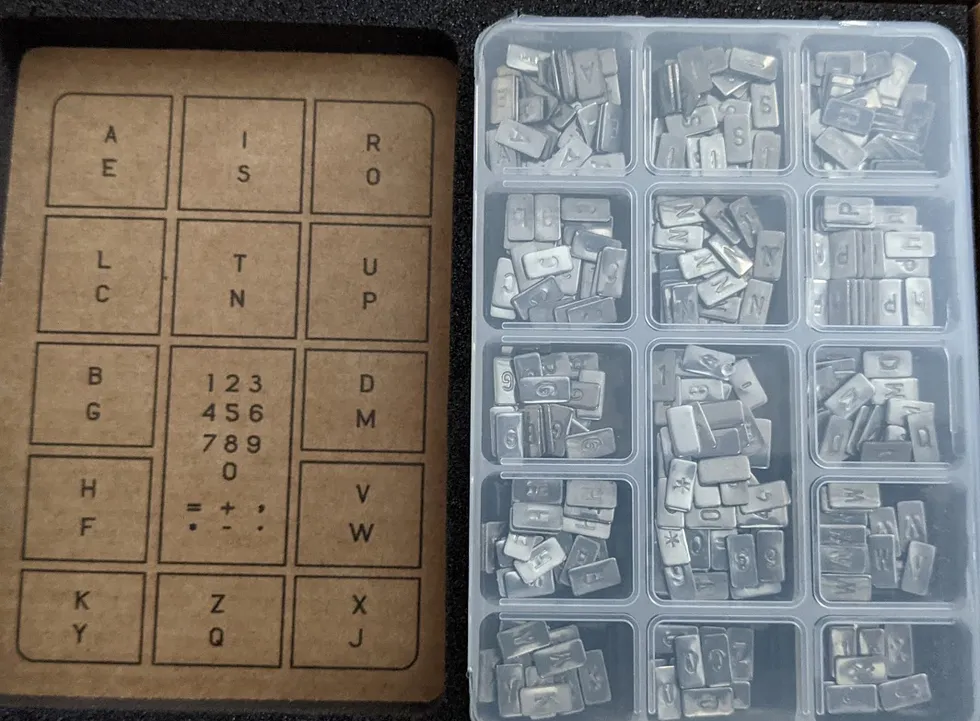
Cryptosteel outline and steel tiles

Cryptosteel device
1. Setup Cryptosteel
Now that you are familiar with the device and have had a chance to look everything over, let's back up your seed phrase.
Step #1 - "Open the case by sliding upper and lower containers like a fan."
When you first hold your Cryptosteel, the device frame is closed and locked, and it appears as a rectangular block of steel. To back up your seed phrase, first, you need to open the device.
To open the device easily, place your fingers near the top of the device, and slide each side in opposite directions.
Identify the top of the Cryptosteel by looking for the side that has a thin rectangular opening, which separates the two blocks of metal. In contrast, the bottom of the device will be completely closed and solid.
You shouldn't have to push too hard to open the Cryptosteel. If you are pushing hard, you are likely pushing near the bottom of the device.

Opening Cryptosteel
2. Unlock the frame by turning the screw counter-clockwise
Now that the Cryptosteel is opened, notice that the device frame is actually 2 plates of steel, with each steel plate holding 12 words, so that you can store your seed phrase.
The way that you store your seed phrase is by sliding engraved steel tiles into the Cryptosteel and then locking it. By default, the device comes locked. To unlock it, you will need to use a flathead screwdriver, or something similar, to turn a screw counter-clockwise. In our testing, we were also able to use a credit card and a fingernail to turn the screw.
It is easy to identify the screw, because it is the only screw on the device that has an opening to be turned. If you lay the Cryptosteel horizontal, the screw is on the top right.

Unlocking the Cryptosteel
3. Release the safety lever by pressing inside the long slot with a small tool.
Before you can open the frame, you need to release the safety lever. The safety lever prevents you from accidentally opening the frame and having your steel tiles fall out.
To identify the safety lever, look for the thin rectangular opening with a small half-oval inside of it. On the 1-12 word side, it is underneath word 12. On the 13-24 word side, it is underneath word 24.
To release the safety lever, you need to push out the metal piece inside the long slot. It's possible to push it out using your finger, but it's much easier to use something like a screwdriver or similar object.
Releasin safety lever
4. Open the frame while safety lever is released
Once the safety lever is released, you can easily open the frame by sliding it open. When the frame is shut, it protects the steel tiles from falling out by keeping them locked in place. After you have opened the frame, you are ready to start placing your seed phrase in the Cryptosteel.

Opening the frame on the Cryptosteel
5. Insert the slots with the first 4 letters of each word
With the frame open, you will be able to slide the engraved steel tiles into the Cryptosteel. Notice the numbers engraved on the device. It is extremely important to follow the correct order! The Cryptosteel has 3 rows, each with 4 words.
Due to the way BIP39 works, you will only need the first 4 letters of each word. This is because each word of the 2,048 word list has unique first 4 letters. If you have a word that only has 3 letters, feel free to use a steel tile from the numbers and symbols box to represent the "extra" space.
Now, it is time to open the plastic case containing your letters, and put them into the Cryptosteel:
- Identify word 1 of your seed phrase, and identify the position of word 1 on the Cryptosteel.
- Gather the engraved steel tiles of the first 4 letters of your word.
- Insert the 1st letter first, position it in the slot, and slide it to the bottom.
- Insert the remaining engraved steel tiles to complete your 4 letters.
- Repeat the process for the rest of your 12 words.
*If you have a seed phrase that has more than 12 words, keep following this guide till the end, and then repeat the same steps for the second steel block that contains words 13-24.*

Sliding the engraved steel tile into the Cryptosteel

First 4 letters of the first word in the Cryptosteel

When you are finished sliding in the steel tiles, this is what it will look like
6. Close the frame and bend the safety lever back inside the slot
Now that all the slots are filled, the next step is to close the frame and close the safety lever. When doing this step, be very careful to keep the Cryptosteel flat and horizontal. If you tilt it too much, it is possible for the steel tiles to slide out!
Before you can close the safety lever, you have to close the frame. Closing the frame is super-simple: just push it back down into place, and it should naturally fall into place without much resistance.
To close the safety lever, you need to push it back inside the slot. This requires a little more resistance than closing the frame. If the safety lever doesn't want to bend back into the slot, just give it a good push.
7. Lock back the frame by turning the screw clockwise
Recall Step 2, when you had to unlock the frame by turning the screw counter-clockwise? This step is the opposite of that: you are going to lock the frame by turning the screw clockwise.

This is what your Cryptosteel will look like once you have locked the frame
8. If you have a seed phrase more than 12 words, repeat these steps for the other side
The Cryptosteel is made up of 2 steel plates, with each steel plate containing 12 words. You have just completed setting up the Cryptosteel for a 12-word backup ... congratulations!
But what if you have an 18, or 24-word seed phrase? If so, repeat these same steps for the 2nd steel plate to back up the remaining words of your seed phrase.
When you are done, slide the 2 steel plates together so they form 1 steel plate. When finished, it will look like this:

The Cryptosteel, closed and locked
The advantages of using Cryptosteel
Using this method to backup your seed phrase provides protection from destruction via disaster. In today's world, you do not need to look far to see natural disasters happening around the world. From Texas freezing over, to fires in California, Cryptosteel ensures that your seed phrase is protected, and comes out completely intact on the other side.
The ideal solution
Cryptosteel is near-perfect as a long-term backup and storage solution. Since the steel wallet is a physical device, storing it in a safe place that is under your control is crucial. The best place to store the Cryptosteel would be in a safe, lockbox, or cleverly hidden - for example, embedded in a steel object.
The Cryptosteel is not without downsides. For starters, recovering your seed phrase requires physically retrieving the device, which could be tricky, depending on your chosen hiding place.
Today, next-generation digital backup solutions are available that utilize military-grade encryption, providing the same level of security as the Cryptosteel, and incorporating high levels of fault-tolerance and ease of access to your backups. You could choose to have the best of all worlds by using the Cryptosteel to provide protection against disaster and destruction, combined with next-generation tools like Vault 12 for your day-to-day use - with the same level of security.
Crypto Inheritance Recap: January 2026
Vault12’s monthly update on regs, the industry, and crypto inheritance management
- Regs Update.
- Vault12 Guard Product Updates.
- New to Crypto Inheritance? Start here.
Vault12 Open Source WebAuthn/Passkey Support for Electron on macOS: Enabling Touch ID and iCloud Keychain in Hybrid Desktop Apps
Miami - January 13, 2026 - Vault12 announced today the open-source release of electron-webauthn-mac, a native WebAuthn/Passkey implementation for Electron apps on macOS only that ports Apple's platform authenticators (Touch ID and iCloud Keychain) and cross-device passkey flows directly inside Electron-based desktop applications.
Why this is important: WebAuthn functionality in Electron apps on macOS is still blocked from real-world adoption.
On macOS, Electron does not provide native prompts for selecting a passkey or security key, and developers must use an Electron native module that invokes the Apple authorization APIs natively, and then manage the flow through IPC between the renderer and main processes.
“WebAuthn and Passkeys are extremely powerful security tools — but only if developers have a reliable platform for app deployment. We created electron-webauthn-mac to make that authentication pathway reproducible, auditable, and open-source — so other teams can ship applications protected by passkeys with Touch ID and iCloud Keychain without re-inventing the wheel.”
- Max Sky, co-founder and CEO of Vault12.
This highlights why many teams still don’t ship Apple-native passkeys in desktop web apps: the path is platform-specific, native-code heavy, and easy to get wrong. Meanwhile, Electron’s macOS WebAuthn behavior has been a long-running pain point for developers, with reports of the standard navigator.credentials flows being broken or unresponsive on macOS in Electron contexts.
Vault12’s solution: a native polyfill that connects Electron to Apple AuthenticationServices
electron-webauthn-mac is a native implementation and polyfill for macOS that enables Electron apps to use Apple’s AuthenticationServices framework directly — while retaining the ability to access the regular WebAuthn APIs on other platforms. This capability is already included in Vault12 apps.
Key capabilities include:
- Platform & security key authenticators: Touch ID, iCloud Keychain, cross-device QR pairing, and external FIDO2 keys
- PRF extension support to derive symmetric keys from passkeys for client-side encryption (platform authenticators)
- LargeBlob extension support to store/retrieve arbitrary data on the authenticator (platform authenticators)
- System integration to open the macOS Passwords/Password Manager directly from an Electron app
- TypeScript-ready developer experience, with included type definitions and an example Electron app showing best-practice main/renderer bridging
One big reason WebAuthn on macOS in a desktop app is fiddly has to do with the fact that macOS insists on security measures indicating that this app comes from the relying party domain (rpId). Vault12’s project documents and operationalizes the necessary steps, including hosting an apple-app-site-association file and embedding Associated Domains entitlements during code signing – with guidance on provisioning profiles and verification.
Availability
The electron-webauthn-mac is open sourced today (MIT licensed). See the repository documentation for installation and quick start: https://github.com/vault12/electron-webauthn-mac
About Vault12
Vault12 is the pioneer of crypto inheritance and develops security technologies that enable people and companies to protect important secrets — like cryptographic keys and 2FA seeds — using secure, customizable and privacy-focused tooling, including open-source components designed to work offline.
It is a venture-funded company that has raised funding from Winklevoss Capital, Naval Ravikant, Data Collective, and True Ventures.
Vault12 Guard can be found in the Apple App Store and Google Play Store.
For media inquiries, please contact: Wasim Ahmad media@vault12.com
How-Tos
Articles on crypto security how to's e.g how to secure, back up, and inherit all your cryptoassets such as Bitcoin, Ethereum, crypto, private keys, seed phrases, NFTs, digital art, DAOs, and DeFi tokens.
View all articlesHow to generate a Seed Phrase.
Here are five ways to generate a seed phrase, with an in-depth discussion on the importance of randomness in ensuring security.
Your seed phrase is the very foundation of a modern digital wallet, and it is no exaggeration to say that seed phrases are at the heart of the cryptocurrency universe generally. But what is it? A seed phrase is a mnemonic code consisting of 12-24 words used to create or recover your crypto wallet. You may have heard it referred to as a backup phrase, recovery phrase, or mnemonic sentence.
Where do they come from? This article explains some common ways to generate seed phrases.
Key Points on How To Generate A Seed Phrase
When you have your own crypto wallet, you have a few choices for how to generate your seed phrase:
- The Vault12 Guard app can generate a secure seed phrase for you.
- You could let your digital wallet generate a seed phrase for you.
- Or for very high security, you could "roll your own" seed phrase with dice or a calculator as offline methods.
It is extremely important that your seed phrase be randomly generated, so that it cannot be guessed or reverse-engineered.
1. How to generate a seed phrase with Vault12
Vault12 can help you to easily create an encrypted and distributed digital vault. The Vault12 Guard app secures all sorts of digital assets including cryptocurrency seed phrases, and can also generate your seed phrase for you. You can be absolutely sure that your seed phrase is generated safely and automatically backed up in a secure manner. To learn more about it, please read our guide.
2. How to generate a seed phrase with a calculator
Generating a seed phrase by using a calculator is done offline, which requires a bit of extra effort but eliminates the risk of some classes of potential online attacks. This introduces a small number of new risks, however: instead of using one device to generate your seed phrase, you'll need to use two devices: the calculator and an air-gapped computer. To create a seed phrase this way, you'll need a calculator that has a RANDOM function (for generating entropy). Learn more about generating a seed phrase using an offline calculator here.
3. How to generate a seed phrase with dice
A humble pair of dice can be used for a non-digital and completely offline method of seed phrase generation. To do this, you'll need dice, a pen and paper, and the BIP39 word list. This method is not for the faint-hearted - be prepared to do some math! You can use a single die if you want, but it is recommended to use multiple dice. You'll be creating entropy by generating a large set of random numbers by using the dice. Learn how to generate a seed phrase with dice here.
4. How to generate a seed phrase with software crypto wallets
With very few exceptions, most modern wallets will create your seed phrase for you when you create your wallet. This process is usually automatic, with limited options for setting the parameters of your seed phrase. For most users this one-time approach is sufficient, and it won't be thought of again.
Please take a look at the article, "Using crypto wallets to generate seed phrases" to get an overview of how seed generation is done inside wallets during the set up phase.
Optionally refer to our Crypto Wallet Guides for step-by-step instructions on how specific wallets accomplish this.
Please keep in mind, that in any potentially high net-worth use case, generating seed phrases manually on your own - especially offline - is an excellent choice since it offers much higher security and greater control over the process.
5. How to generate a seed phrase with hardware wallets
Hardware wallets provide an extra level of security compared to software wallets, and provide methods to generate a seed phrase locally (within the wallet itself). Hardware wallets strike an excellent compromise between usability and high security. Feel free to check out Vault12's "How-to" wallet guides to bring you through the steps needed to securely generate and back up seed phrases using hardware wallets.
Here are some hardware wallets that we recommend:
- Ledger Nano X
- Ledger Nano S
- Trezor One
- Trezor Model T
- KeepKey
- ColdCard MK3
- BitBox 01/02
What goes on behind the scenes of generating a seed phrase?
In a nutshell, the process of generating a seed phrase starts with generating random data, called entropy. The entropy is then run through a hashing function - specifically SHA256 - to generate a checksum. Part of the checksum is then added to the random data. The resulting output is then split into chunks of 11 bits, where each 11-bit chunk maps to a single word on the BIP39 word list.
Confused about anything in the above paragraph? Don't worry, each step will be explained in an easy to understand format below. You can also get a higher-level understanding of seed phrase construction by checking out the article "What is BIP39?".
How much entropy should your seed phrase have?
Generating a seed phrase HAS to begin with a RANDOM SOURCE OF DATA, otherwise an attacker could possibly steal funds by guessing or regenerating your seed phrase. Entropy is a measure of how random a set of data is.
Which offers more randomness: rolling 1 die, or rolling 2 dice? Since 2 dice have more possible outcomes, the randomness is higher. It is the same for your seed phrase. The more words that are in your seed phrase, the higher the entropy.
To successfully generate a seed phrase, the entropy generated has to fit certain parameters. The random data must be between 128 bits and 256 bits of entropy, and divisible by 32.
128 bits of entropy maps to a 12 word seed phrase
160 bits of entropy maps to a 15 word seed phrase
192 bits of entropy maps to an 18 word seed phrase
224 bits of entropy maps to a 21 word seed phrase
256 bits of entropy maps to a 24 word seed phrase
How are SHA256 and BIP39 word lists used to generate a seed phrase?
A hash function is a computer program that takes an input of data and returns a verifiable result, called a checksum. The input can be any source of data. Running the same hash function again on the same input data will always return the same checksum as the result.
For example, running your randomized source data of 128 bits of entropy through a hash function will always return the same result, so it can be used as a checksum. If the source data changes, you will get a different result from the hash function.
In this step, the random source data is run through the SHA256 hash function. The first X digits of the checksum are then added to the random source data/entropy, where X is equal to: (amount of bits of entropy / 32).
256 bits of entropy (256/32 = 8) - add the first 8 bits of the checksum to the random data
224 bits of entropy (224/32 = 7) - add the first 7 bits of the checksum to the random data
192 bits of entropy (192/32 = 6) - add the first 6 bits of the checksum to the random data
160 bits of entropy (160/32 = 5) - add the first 5 bits of the checksum to the random data
128 bits of entropy 128/32 = 4) - add the first 4 bits of the checksum to the random data
It's important to note that BIP39 generates the seed phrase from binary code, which is made up of 0's and 1's. However, the SHA256 hash function returns the checksum as a sequence of numbers and letters, called a hexadecimal. So in order to get the seed phrase, you have to convert the checksum from hexadecimal format to binary format.
Here's the next step: We slice the result into 11-bit chunks of data. Each 11-bit chunk of data will map to a word from the BIP39 word list
You have seen the word "bit" used a few times in this article. A bit represents 0's and 1's. It is the smallest representation of data we have, and it is expressed in a language our computers understand.
Your original source of random data (or entropy) plus the SHA256 checksum is divisible by 11. The BIP39 word list contains 2048 words, and each word on the list maps to 11 bits of data. In this next step, you break your entropy+checksum combo into sequential chunks of 11 bits.
It is important that you slice the 11-bit chunks in sequential order. This means going from left to right, every 11 bits is grouped together. Every 11 bits represents a word in your seed phrase, and the order of the words has to be correct.
The next step is to convert your 11-bit sequence into decimal format. This will give you a number that maps to the BIP39 word list. Now, in the correct order, map each 11-bit sequence to the matching word in the BIP39 word list. Finally, this is your seed phrase!
It's important to highlight that some word lists for BIP39 might start with 1. In code, the first number is always 0. This means that 2048 words are listed as 0-2047, not 1-2048. If your BIP39 word list starts with 1 instead of 0, you will need to subtract 1 from the word list numbers to get the correct word.
What are some different ways to perform Random Number Generation (RNG)?
Going back to generating your initial source of randomness: Once you generate the needed entropy, the remaining process of getting the seed phrase is simply math and cryptography. In practice, this means that when generating a seed phrase, the initial source of entropy is both the most important step, and also the step in which you have the most control over the result.
There are many ways to generate entropy: flipping a coin, rolling dice, dealing a deck of cards, recording ambient sound, and many more. The goal here is to get as close to true randomness as possible. If you are using a process that is not sufficiently random, an attacker could possibly recreate your seed phrase.
In the following sections of this article, we will cover different approaches for how to generate entropy, and thus generate your seed phrase.
What are the security considerations of generating your own seed phrase?
Taking control over the generation of your seed phrase provides an opportunity to increase the entropy of your seed phrase, thus increasing the security of your entire wallet. This does not come without risks - a single mistake can result in a less secure wallet, or even lost funds.
When generating your own seed phrase, security must be top-of-mind throughout the whole process. The most crucial part of generating your seed phrase rests with the generation of entropy, which is the first step of generating your seed phrase.
Your seed phrase can have 12, 15, 18, 21, or 24 words. Remember that the more words in your seed phrase, the higher the entropy, which results in higher security. A correctly generated 24-word seed phrase will ALWAYS produce a wallet that is more secure than a 12-word seed phrase. Many wallets today only produce 12-word seed phrases in their built-in wallet creation workflow - and given today's technology, 12-word seed phrases are still very secure. But a key concept here is 'correctly generated.' The only parameter that can be changed is the source of entropy. This is very important because if the source of entropy is corrupted, an attacker could potentially regenerate your wallet and steal your funds.
Generating entropy can be done manually or with a computer. Both methods have pros and cons, but when generating entropy, care must be taken to ensure that the process is done correctly and is free from outside manipulation or observation.
One example of manually generating entropy would be flipping a coin. But if an attacker gives you a coin that is weighted slightly in favor of heads, your initial source of entropy will have been corrupted.
When using a computer to generate entropy, the attack vectors (or corruption attempts) could be both over the internet and physically in-person. The computer being used should not be connected to the internet, as that could offer an opportunity for attackers to compromise the process. However, even if the device was ever connected to the internet, it could allow the possibility for this process to be compromised.
Part of being in a security mindset means limiting opportunities available for bad actors. A device not connected to the internet is considered to be air-gapped, and an attacker generally would have to be physically present at the device to be successful at manipulating its entropy generation capabilities.
Lastly, if you don't have a spare device that you can airgap, don't worry - you could use a "live" Linux environment. Many Linux operating systems are able to be run off of a portable USB stick or flash drive. These are called `live` distributions and they're released with verification signatures, so you can easily verify that the operating system has not been tampered with. We recommend Tails OS - a portable OS that protects against surveillance and censorship. To run the operating system, just plug in the flash drive and boot it up. When you're done, simply remove the flash drive and return to your normal operating system. This very temporary lifecycle of a "live" Linux distribution reduces the window of opportunity for even the cleverest bad actor to access and compromise it.
How to access your Seed Phrase or asset stored in Vault12.
If you need to access your Seed Phrase or other assets from your Vault, this article shows how you can ask your Guardians to unlock them to grant you access.
There are many ways to generate and back up seed phrases, and a superb choice is to use Vault12 Guard.
If you used Vault12 Guard to back up your seed phrase, this guide describes how you can access that seed phrase by unlocking your asset.
To access a seed phrase that you have stored in your Vault, you will follow these steps:
- Confirm that your seed phrase is backed up in your Vault, and that your Guardians are active.
- In the Vault12 Guard app, request that the asset be Unlocked.
- Wait for Guardians to confirm your request.
- View the asset.
1. How to confirm your Digital Vault setup?
In order to access your seed phrase or backup code that has been stored in your Vault, first check that you have a working Vault in your Vault12 Guard app, and that your Guardians are available. In general, it is a recommended practice to do a Vault "health check" regularly.
If you don't have a Vault because you changed phones, then you can recover your entire Vault - see instructions for Vault recovery. After recovery, your Vault and its stored assets will again exist on your phone, and you can proceed with these instructions to unlock the stored seed phrase or other asset.
If you have not created a Digital Vault and assigned Guardians to protect it, please follow these instructions (since you did not have a Digital Vault, the new Vault created will be empty).
Are your Guardians active?
Once you have confirmed that your assets are stored in the Vault installed on your phone, ensure that your Vault Guardians are available. You can do this by switching to the "My Guardian" tab from the bottom navigation pane. If all of your Guardians are shown as active, you can proceed to request an Unlock.
If not enough of your Guardians are shown as active, you may want to call your inactive Guardians in advance and ask them to open the Vault12 Guard app on their phone, to refresh the encrypted connection between your apps.
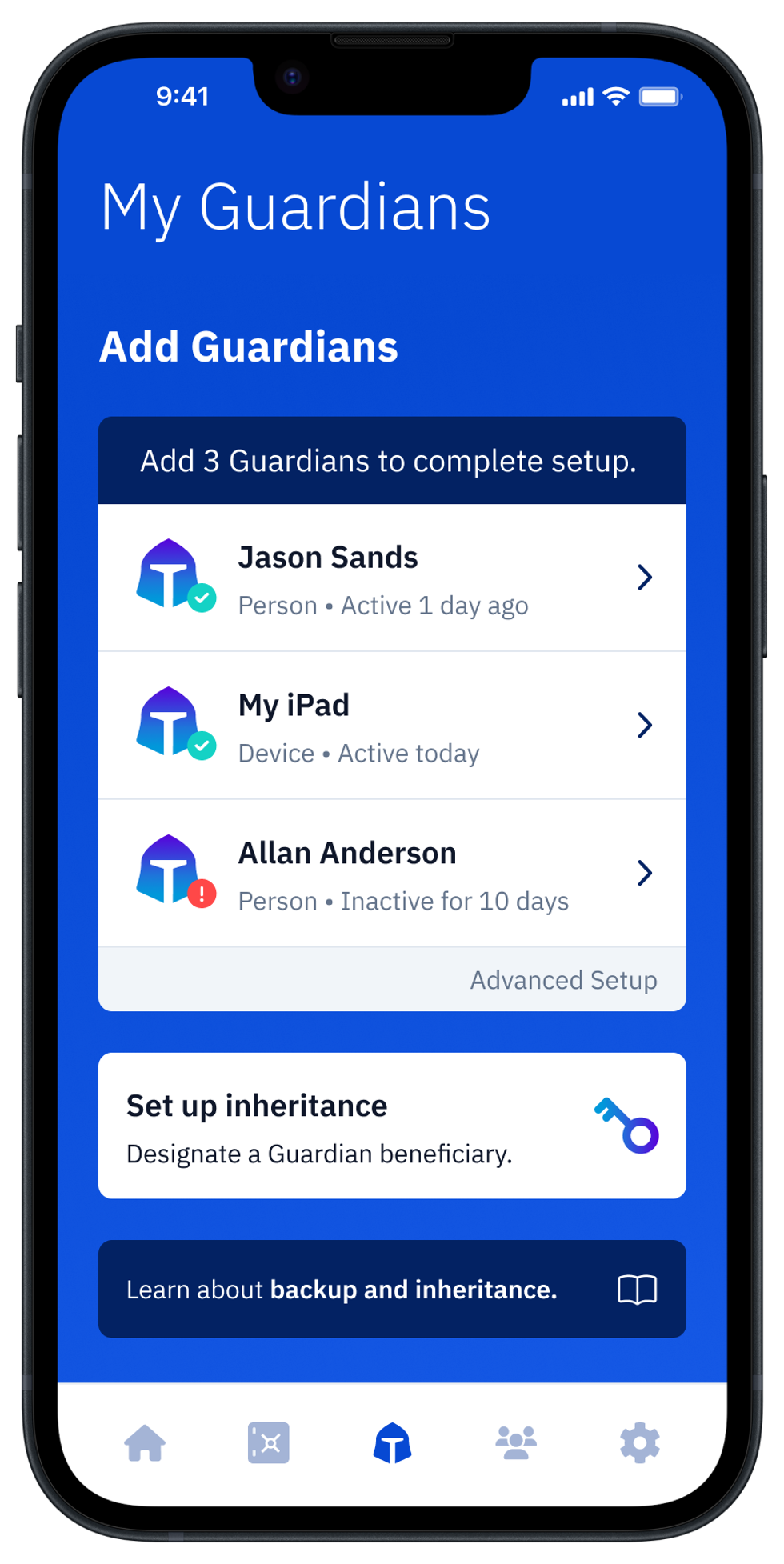
2. How to use Guard to request that your asset be Unlocked?
First, jump to the Vault section of your Guard app by using the bottom navigation pane.
On the "My Vault" screen, you will see your asset inventory, with the current state of each asset shown below its name. As you can see, there may be a variety of different states for the same asset:
- Blue icon - asset has a local copy on the device
- Grey icon - asset only saved with Guardians
- Recovering badge - the asset is requested for Unlock, and Guardians' responses are pending.
- Recovered badge - the asset was unlocked by Guardians, and a local copy is temporarily available.
- Sent to Guardians badge - the newly-created asset is in the process of backup and distribution to Guardians.
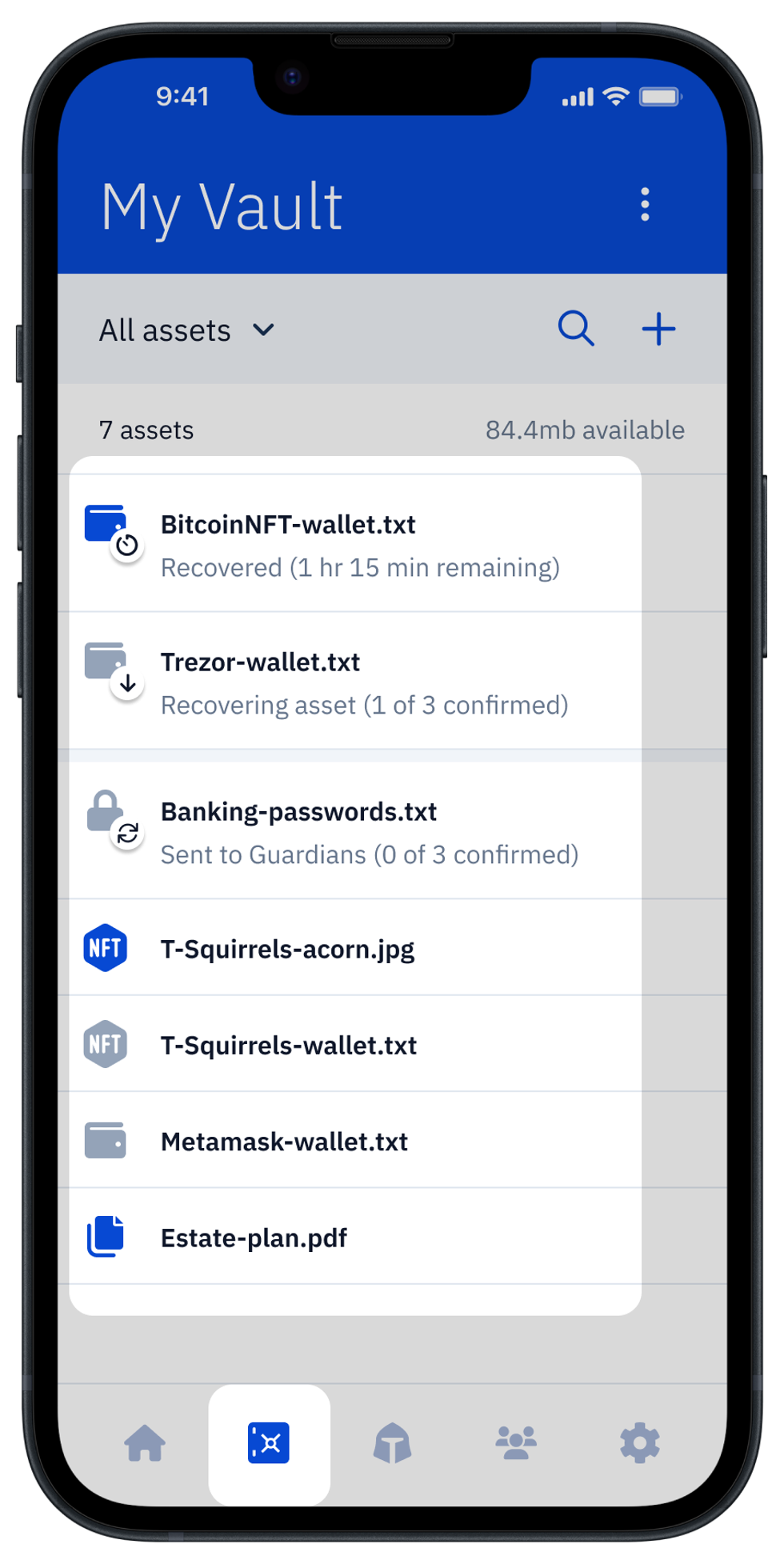
To Unlock an asset, choose the asset that you wish to unlock from the inventory list, and tap to open the Asset Details screen.
Then click on the "Recover from Guardians" button.
In the image above, there are two assets in a locked state (with grey icons). Let's unlock one of them (Metamask-wallet.txt) for illustrative purposes.
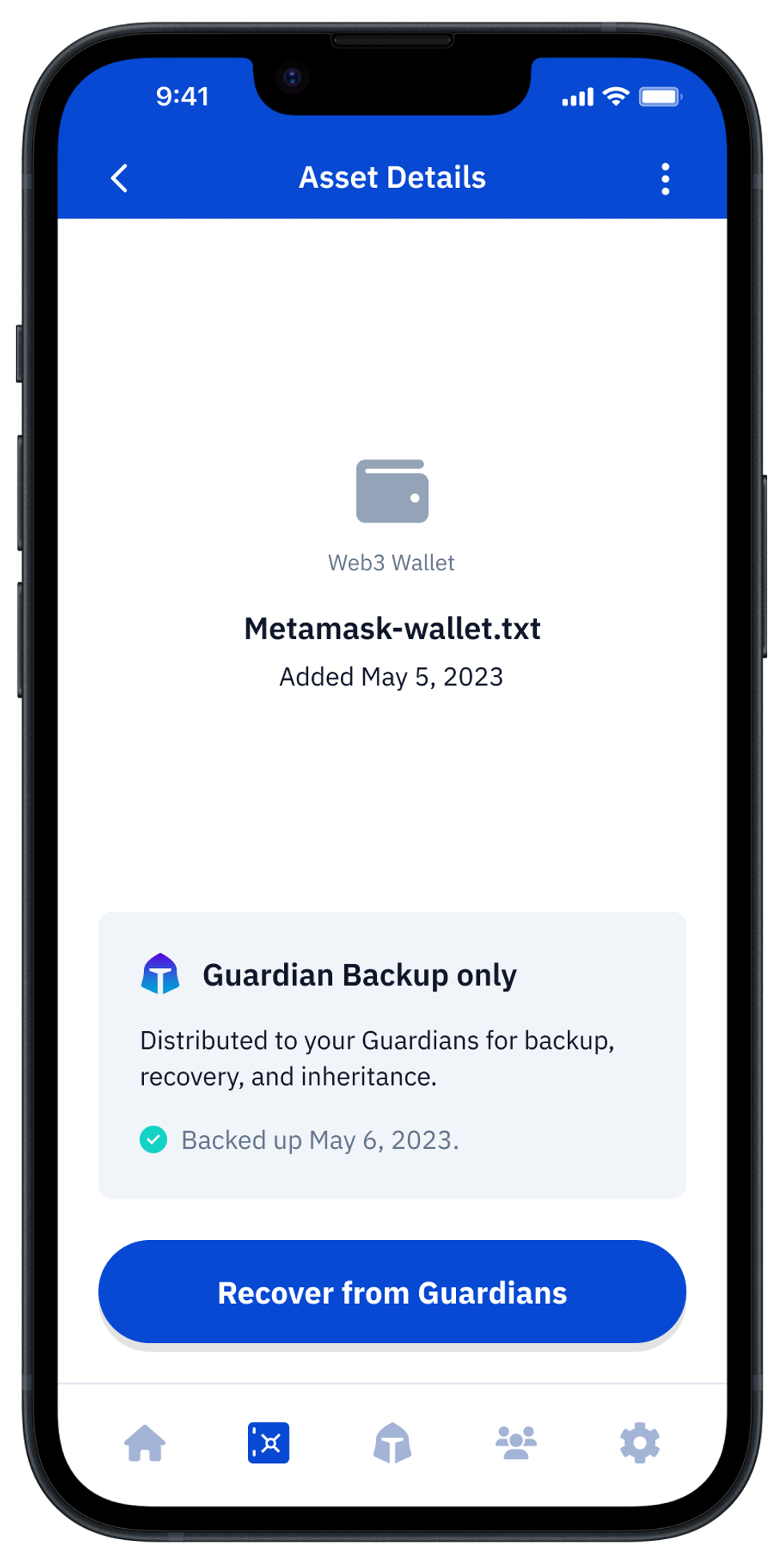
How do Guardians confirm recovery requests?
When the "Recover from Guardians" button is pressed, all of your Guardians will be notified with your Vault unlock request.
You have significant privacy even from your Guardians, since none of your Guardians can see which assets you are accessing. Your Guardians only see that you requested them to identify you, and they are asked to confirm that you made such a request.
Guardian's in-app notification of your request
As the Vault owner, to see the progress of Guardians' responses, and of your overall recovery request, tap "View Status" in your Vault app.
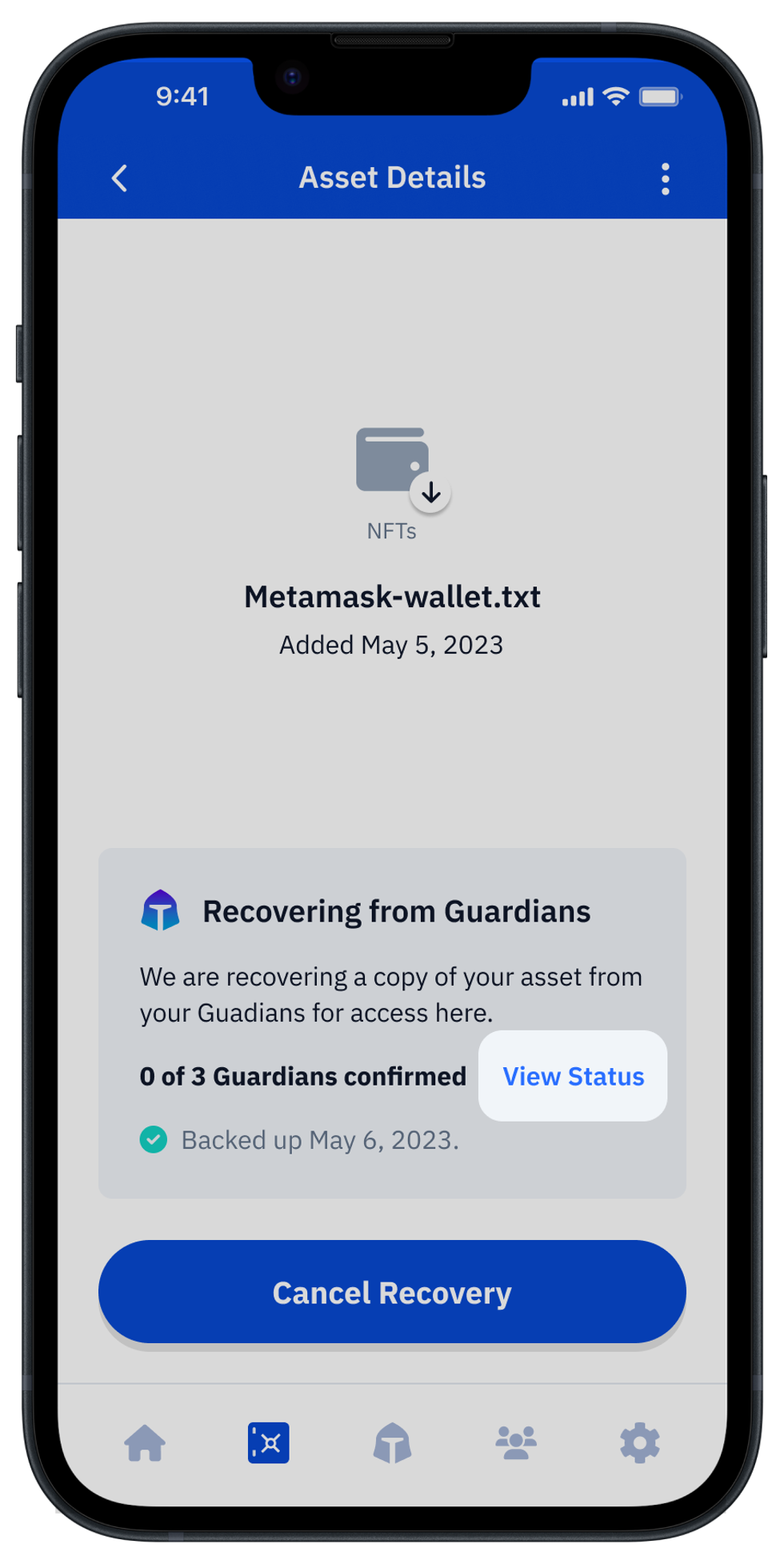
How do Guardians approve your recovery of the asset?
Here you can see all the details of the Guardians' confirmations progress and the recovery:
- The total number of Guardians requested (by default 3)
- Number of confirmations you need to receive from Guardians to recover (by default 2)
- Guardians' names, and status of their responses.
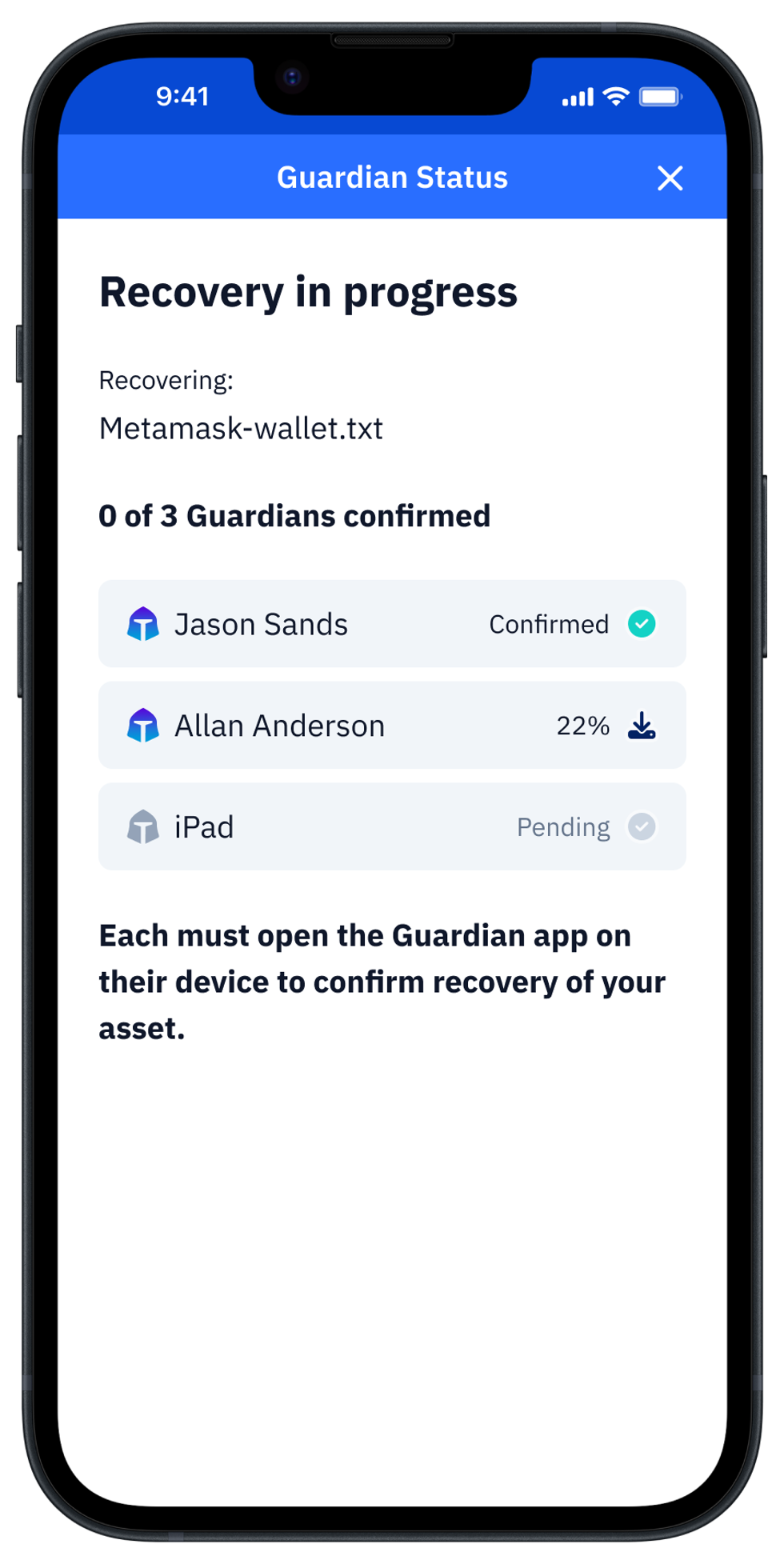
How to view the recovered seed phrase?
As soon as you have been positively identified by the required number of Guardians, and they confirmed your restore request, your asset will be recovered and available for you to view. You can then tap on "View Recovered Asset" to interact with it. Be careful not to expose your asset unintentionally to observers or cameras!
Do not hesitate to learn more about how to maintain your crypto safely and easily at SecureMyCrypto.org.
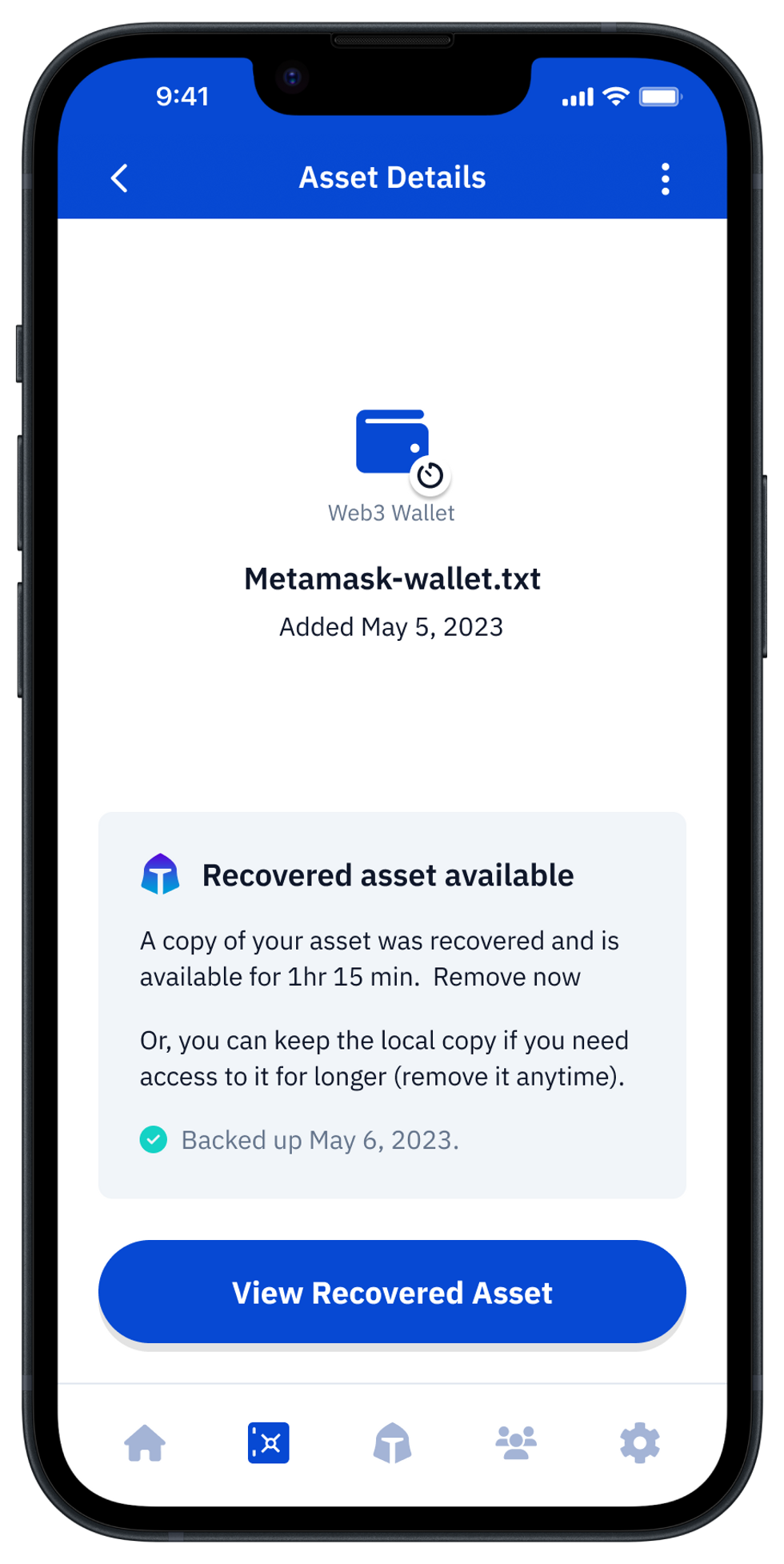
.
11 Things you need for a safer crypto environment.
These security-related best practices will make you and your crypto assets much less vulnerable.
Let's face it… wherever you find money, you will find people who want to steal it, especially online. So it makes sense to set up a secure environment around your crypto - one that is separate from your regular computer and internet activities. Consider implementing the 11 Things below before you buy your first digital assets.
TL;DR (concentrated takeaways)
Make sure that any computer that you use for crypto interactions is and remains free of malware.
Consider having unique or dedicated resources just for your crypto: computer, smartphone, email address, and of course, strong passwords.
Be extremely careful with your seed phrase backup strategy, and have a plan for how inheritance will incorporate wallet access or seed phrase access.
Use a cold-storage wallet (or several).
Enable 2-factor authentication where possible. Do not miss backing up 2FA recovery tokens too.
Don't "crypto-brag" about your holdings.
1. Create a new secure trading station.
If you are regularly going to be trading crypto versus accumulating or holding long-term, consider buying a new, inexpensive computer you will only use for crypto trading. Uninstall unnecessary pre-loaded software. Only load the software you need to run crypto-related functions, like wallets, a browser, and possibly a VPN. This is not absolutely necessary, but if you can afford it, it will definitely beef up your security. Also, unplug your LAN or disconnect from your Wi-Fi when not in use.
2. Make sure your computer is free of malware.
There are many commercial choices available on all platforms for anti-malware protection. If you have not purchased commercial antivirus software, you can use a free software program called Malware Bytes (https://www.malwarebytes.com/mwb-download) to scan for malware. Another good free resource for your Mac safety could be ObjectiveSee (https://objective-see.org/tools.html).
Note: When installing wallet software, you may need to disable anti-malware software - just be sure to re-enable it once the installation is complete.
3. If you keep your seed phrase on paper, consider using a Stonebook pad.
Assume that whatever you write and store in a file on your computer is accessible to hackers. As you configure your wallet, you may need to write down your passwords, private keys, seed phrases, etc., in temporary form as they are created. Any temporary paper store must be completely destroyed (for example, burned) after use. For long-term storage, you will need to back up your passwords and seed phrases correctly. If you must use paper, you can buy a water-resistant, tear-resistant notebook made just for cryptocurrency investors called a Stonebook for about $45. (However, there are limits to the protections that a Stonebook offers, and you would want to store it in a water and fireproof bag inside a locked safe or safety deposit box.)
4. Back up your seed phrases.
This is the most important step of all. The promise of crypto is that you can become your own bank. Sounds great, but it means you are 100% responsible for whatever happens to your crypto and therefore you must secure your seed phrase. If you lose your password or seed phrase but failed to back it up, there is no one to call to fix that. Safely backing up and storing your seed phrases and passwords is vital. To learn about many options for backing up your seed phrases, check out our article on "How to Back up a Seed Phrase," and be prepared before you buy your first crypto.
5. Create long, truly random passwords.
Every account, application, email, and wallet needs to have a completely different password. You should also have a strong password to turn on your computer. Never store your passwords in your browser. If you use online password managers, be sure the password to log in to the manager is at least 20 characters long and complex. Write them down, then back them up and store them safely!
6. Create a brand-new email address.
Create a brand-new email address that does not clearly identify your identity (for example, it should not contain your name). Use this only for crypto. Do not use it for anything else - not even for crypto newsletters! ProtonMail is an excellent choice for secure email. Make sure your recovery email account has a strong password, too.
7. Buy an inexpensive smartphone.
If you use your smartphone to interact with your cryptocurrency, consider buying an inexpensive smartphone that you use only for cryptocurrency trading. Password-protect that phone. (If you plan to use your current phone, remove your number from all online sites.)
To reduce the risk of a "SIM-swap attack," make sure that your cell phone provider will allow you to require a passcode before they will activate a new SIM card - some providers do not have this option and scammers have been known to go into their store and claim that they lost their phone and need a new one. They usually have just enough information to "prove" that they are you, and they get a new phone with all your information on it! Require a passcode and back it up.
8. Download two-factor authentication apps.
Two-factor authentication (2FA) applications make authenticating your identify more secure by forcing the confirmation of not just one factor, like a password that you know, but also a second factor, like whether you can prove access to a known device like your smartphone. Common 2FA apps for your smartphone include "Google Authenticator" and "Authy."
You will not usually be allowed to pick your favorite 2FA app to use ... the site or device that you are using (for example, a crypto exchange) will suggest one that they interoperate with as part of their authentication process. But many different sites will give you the choice of whether to enable 2FA - always choose yes! Be aware that some sites support 2FA but may not enable it for you by default - if user setup steps at a crypto-related site did not walk you through enabling 2FA when you set up your account, look at your user account settings to see whether it is offered as an option. In order to enable 2FA at several different sites, you will likely accumulate more than one 2FA app on your phone or laptop.
WARNING: Don't forget to backup your 2FA recovery codes! Losing your 2nd-factor authenticators could easily lead to unrecoverable accounts lockout. This is a VERY common oversight.
9. Buy a cold storage wallet.
Buy a cold storage wallet to store your cryptocurrencies. These will cost you between $60 and $200. There are a few reasons to never leave your cryptos on exchanges. One: hackers could attack the exchange and take your coins. Two: the exchange could go down or go out of business. And three: regulators could shut down exchanges that do not meet their regulations. Not all wallets hold all cryptos. You will need to find and buy a wallet that will accept the cryptocurrency you want to buy. Check out our overview of crypto wallets with detailed instructions about how to set up and use them here.
10. Distribute your crypto among several wallets.
You may want to divide up your cryptos and store them on different devices. That way, if one gets compromised, you haven't lost everything. This becomes more important if you are holding large values of cryptocurrency.
11. Record detailed instructions about your crypto investments for your heirs or beneficiaries.
Keep it simple, but detailed. You will need to store this in a safe place and implement a way that your heirs can find it or be notified. One of the simplest ways to do this is via the Vault12 Digital Inheritance solution. And, if you haven't already, create a will - it's a responsible and thoughtful thing to do.
Bonus tip: One more thing…
Don't brag about your crypto purchases in public places, online or offline. Unfortunately, there are stories of hackers and criminals targeting people with newly found crypto wealth. Keep your investment to yourself.
Back up your Seed Phrase or add an asset using Vault12.
If you already have a Guard Digital Vault and a Seed Phrase, these steps show how to store your Seed Phrase as an Asset.
There are many ways to back up a seed phrase, and here we will show you how you can use the Vault12 Guard app to back up a seed phrase from your preferred wallet.
To back up a seed phrase using the Vault12 Guard app, you will need to complete the following steps:
- Using the Guard app, create and set up a Digital Vault.
- Add an Asset to your Vault, e.g., "Add Web3 Wallet."
- Using the Web3 Wallet, generate your Seed Phrase.
- Using the Guard app, save the Seed Phrase or backup code into your Vault.
Confirm your Digital Vault setup
In order to back up a seed phrase, you must have a working Digital Vault. If you have not created a Digital Vault and assigned Guardians to protect it, you can easily do that by following these instructions first.
After you have created a Vault, from the Guard app's Home screen, add an asset to your vault by tapping on "Add a Web3 Wallet."
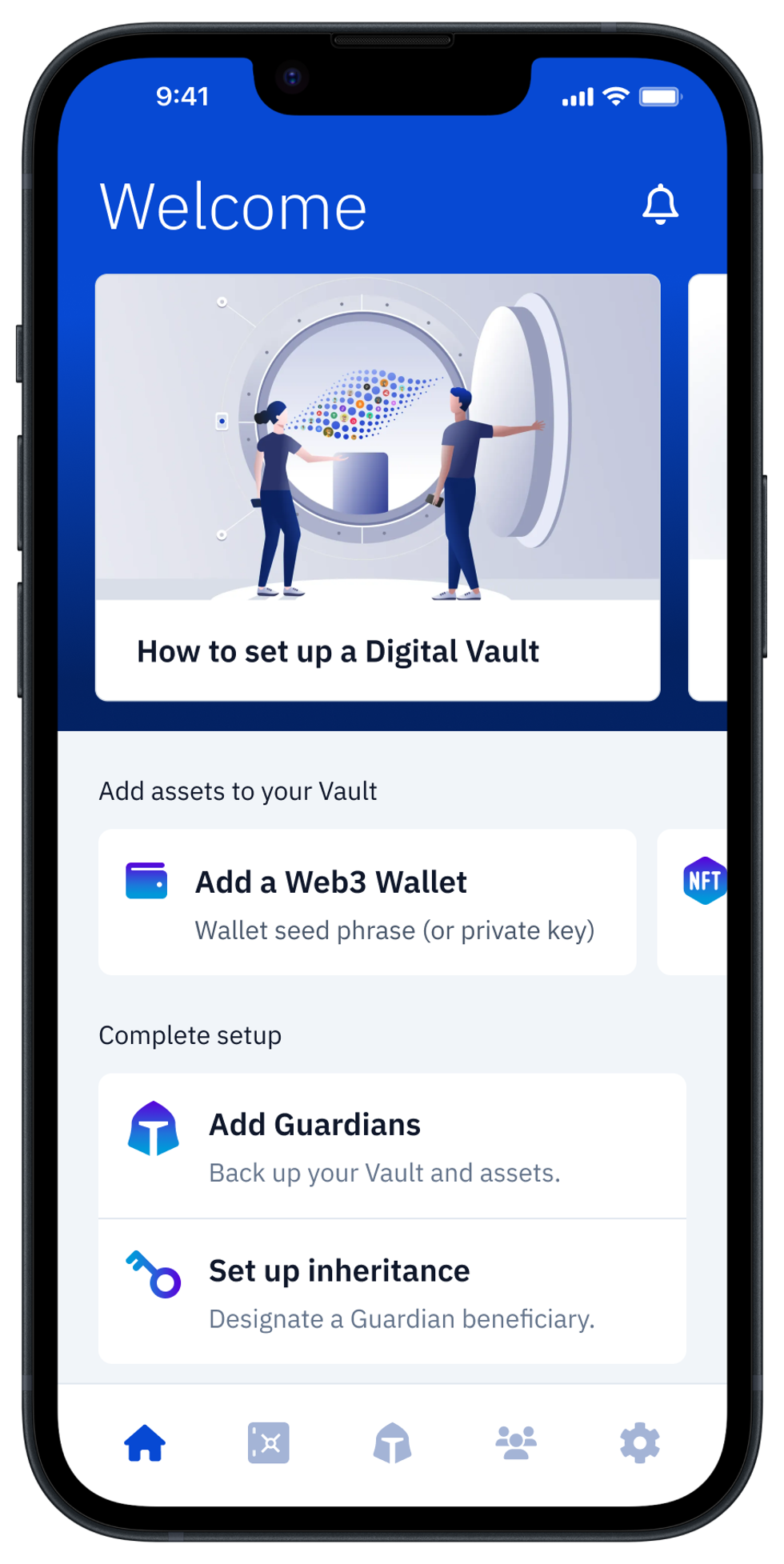
Add an Asset to your Digital Vault
Alternatively, you could start from the app's "My Vault" screen, by tapping the Add an Asset button, or the [ + ] button in the upper right corner, and then choosing Web3 Wallet.
Choose your Wallet type
On the next screen, you will be able to choose the wallet vendor you are backing up from (or which you plan to use). By identifying the wallet vendor, it is easy for you to distinguish multiple seed phrases and private keys that you may accumulate in your Vault in the future.
When you select a wallet type, you can choose from all major vendors of software and hardware wallets.
Choose a display format for your Seed Phrase backup
Now, you need to select the format in which you want to store your seed phrase - word-by-word or free-text format. The 'Enter each word" option presents the words in your seed phrase as a formatted list. The "Free-form text" option allows you to enter your seed words in whatever way you choose.
There are also Advanced options in case you want to securely generate a new seed with the Vault12 Guard app, or import your seed backup as a file or as a photo of your paper backup.
Prepare to add a Seed Phrase to your Vault
Create or open your Web3 wallet, and display your seed phrase. Often, right after you set up your wallet, it will ask you to back up your Seed Phrase - this is the best time to add it to your Vault. Confirm how many words your seed phrase contains (for example, 12), and select that option in the Vault12 app.
Carefully enter your Seed Phrase into your Vault
Carefully enter your Seed Phrase into your Vault, word by word, in order, until all words have been entered. You can copy/paste the whole seed phrase if your wallet provides such an option. Be sure to double-check your entry against what you see in your wallet. (You may even want to triple-check! )"Enter each word" option
 "Enter each word" option
"Enter each word" option"Free-form text" option
 "Free-form text" option
"Free-form text" optionName your Asset, and store it in your Vault
Once you have entered all of the words and clicked the "Done" and "Continue" buttons, you have the option to give your Wallet's Asset a unique name (otherwise it will be stored with the name of the Wallet vendor chosen before).
Also, if you already set up the Guardians for your Vault, there will be a choice between creating an Asset Backup using your Guardians only, or "Guardian Backup + local copy" of the Asset too. Having a local copy might be convenient in case you need regular and prompt access to this seed phrase, however choosing "Guardian Backup only" is more appropriate for cold storage and higher security needs.
Finally, press the "Add to Vault" button, to store the Asset.
Your Vault distributes a Backup of your Asset to your Guardians
After you tap "Add to Vault," the app will bring you to the main "My Vault" screen, showing you the newly added Asset. You can check the status of the backup by tapping on the Asset.
After the seed phrase is stored in your Vault, it will be encrypted, split, and distributed to your Guardians (if you already set up the Guardians for your Vault). In case you choose not to store a local copy, the asset will be locked after distribution to Guardians is complete.
"My Vault" with added Asset
 "My Vault" with added Asset
"My Vault" with added AssetAsset Details: Backup status
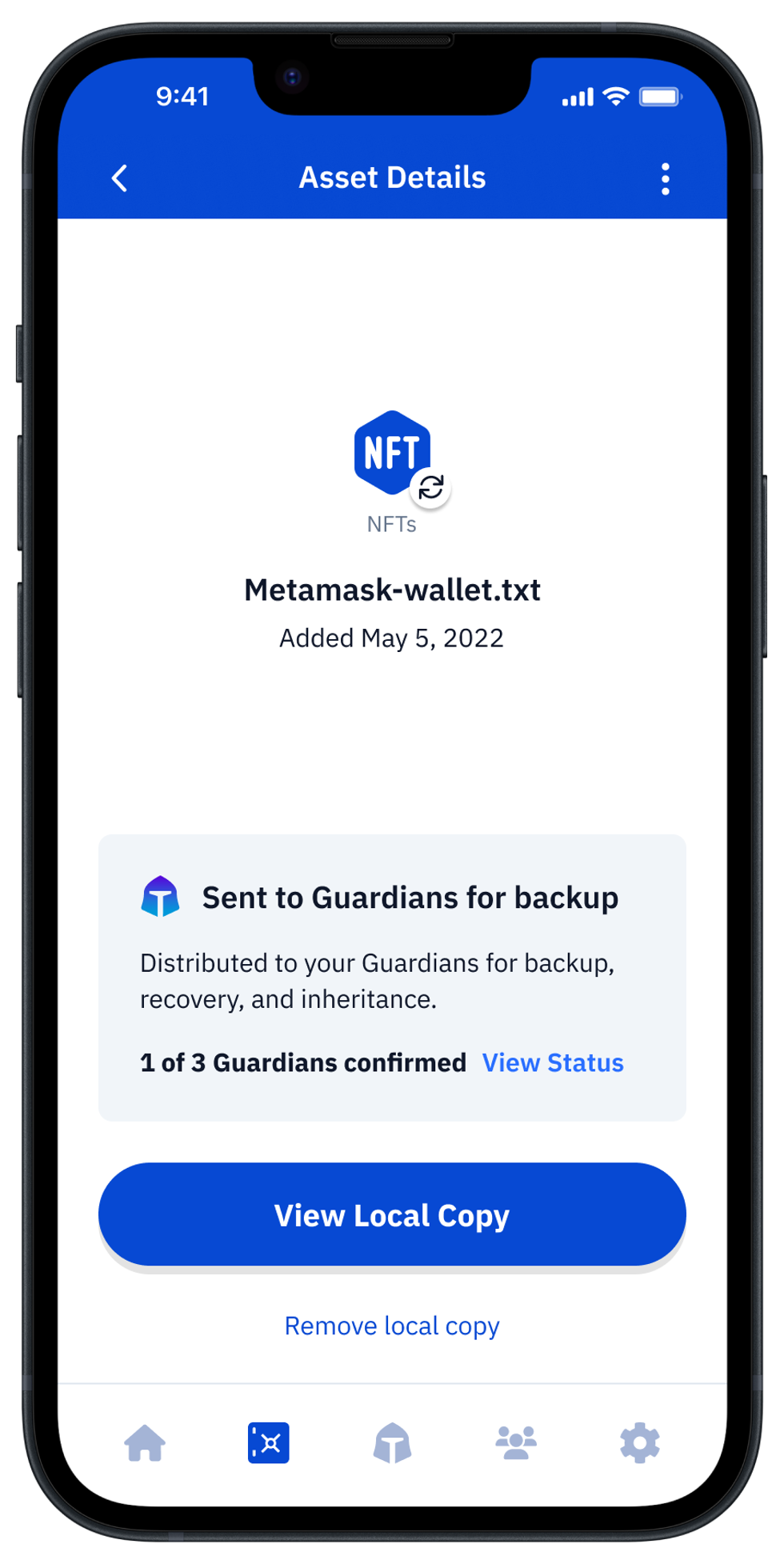 "Asset Details" and backup distribution status
"Asset Details" and backup distribution statusAccess and unlock Seed Phrase Asset
By default, your Asset will remain locked. To unlock and access your Seed Phrase, check out this article.
Once unlocked, your Asset's Seed Phrase will be temporarily displayed so that you can enter it into a new wallet.
Note: The asset will automatically lock after 2 hours.
How to Protect Yourself From Impersonators on Telegram
As members of our Telegram community, you may encounter scammers impersonating admins and others — please read this article to understand how to avoid entanglements.
If you do not want to be taken advantage of by scammers, please remember:
- None of the Vault12 team members will ever ask you for money or cryptocurrencies. You should NEVER transfer any to them. We will never ask for you to send your contributions to a wallet address that we provide on Telegram. All crypto transfers related to Vault12 are found in your Vault12 app.
- If it seems too good to be true, it probably is.
- Never give out your personal details, even email addresses on the Telegram chat. If an admin gets in touch with you via a private message, make sure their username (listed below) is correct before engaging in any discussion.
- See this in-depth investigation by the New York Times into Telegram security.
1. Check Your Telegram Privacy Settings
Telegram gives users a number of privacy settings to control information being accessed, e.g. your telephone number. Make sure you've reviewed the settings to hide information that doesn't belong in public.
Telegram Privacy and Security Settings
2. Identify admins
Check if they have "admin" titles beside their names on the Telegram channel member list.
To see the member list, just click on "members" or "info".
Look for the admin or owner tag
3. Check member @usernames to determine if you are talking to the right person
You may get messages from scammers pretending to be team members with their exact same photo/avatar and a very similar username. Please report those accounts to TG so that they get banned.
Just click on the photo/avatar of the person you are talking to, to check their username and compare this with our list of admin usernames:
Official Vault12 team members:
@wasima
@max_vault12
@commagere
@pavlo1
@anastasiapopova
4. SIM Swapping - Another potential attack risk

The other common attack is via a SIM swap, this is where your phone number is ported to another device, followed by account password resets — the recovery codes now being under the control of the criminal. To guard against this you need to implement 2FA with an app such as Authy, and to have your carrier explicitly forbidden to do number ports to new devices without verifying identity. Please see this article for more details: https://www.wired.com/story/sim-swap-attack-defend-phone/
5. Remember these two things
* Do not transfer your funds to addresses received in private messages
* Block and report any suspicious behavior and spam messages — this will help Telegram remove these impersonators.
Join Us on official channels for current updates
Team: https://vault12.com/team
Blog: https://vault12.com/blog
Twitter: https://twitter.com/_Vault12_
Website: https://vault12.com
White Paper: https://bit.ly/vault12-whitepaper
Announcement Channel: https://t.me/Vault12official
Support Channel: https://t.me/Vault12
Wallet Guides
Articles on crypto security how to's e.g how to secure, back up, and inherit all your cryptoassets such as Bitcoin, Ethereum, crypto, private keys, seed phrases, NFTs, digital art, DAOs, and DeFi tokens. Start here to learn the basics about security risks in Web3, and where to learn more about keeping your cryptoassets secure.
View all articlesLedger vs Trezor: Which Hardware Wallet is Best in 2025?
Looking for a comparison of Trezor and Ledger hardware wallets? Let's review all of the popular models.
Ledger Nano X
- Bluetooth connectivity — works with or without a cable (at least with smartphones).
- Wider interoperability with wallets, coins, and apps.
- Compact. User input is via buttons, not touchscreen.
- Has Secure Element.
- Price Point: Reasonable.
Trezor Model T
- No Bluetooth connectivity. iOS app is view-only.
- Smaller set of wallets, coins, and apps.
- The touchscreen and input are very well-thought-out experiences.
- Missing Secure Element.
- Price Point: About the same.

Ledger Nano X vs Trezor Model T
Ledger Nano X
- Bluetooth connectivity — works with or without a cable (at least with smartphones).
- Wider interoperability with wallets, coins, and apps.
- Compact. User input is via buttons, not touchscreen.
- Has Secure Element.
- Price Point: Reasonable.
Trezor Safe 5
- No Bluetooth connectivity. iOS app is view-only.
- Smaller set of wallets, coins, and apps.
- The touchscreen and input are very well-thought-out experiences.
- Has Secure Element.
- Price Point: About the same.

Ledger Nano X vs Trezor Safe 5
Comparison of Ledger Stax and Trezor Safe 5
Ledger Stax
- Bluetooth connectivity — works with or without a cable (at least with smartphones).
- Wider interoperability with wallets, coins, and apps.
- Posh design with according price level.
- Has Secure Element.
- Large but potentially irritating display.
Trezor Safe 5
- No Bluetooth connectivity. iOS app is view-only.
- Smaller set of wallets, coins, and apps.
- The touchscreen and input are very well-thought-out experiences.
- Has Secure Element.
- Price Point: About half of Ledger Stax.

Ledger Stax vs Trezor Safe 5
Comparison of Ledger Stax and Trezor Model T
Ledger Stax
- Bluetooth connectivity — works with or without a cable (at least with smartphones).
- Wider interoperability with wallets, coins, and apps.
- Posh design with according price level.
- Has Secure Element.
- Large but potentially irritating display.
Trezor Model T
- No Bluetooth connectivity. iOS app is view-only.
- Smaller set of wallets, coins, and apps.
- The touchscreen and input are very well-thought-out experiences.
- Missing Secure Element.
- Price Point: About half of Ledger Stax.

Ledger Stax vs Trezor Model T
More comparisons coming soon...
Missing comparison for any model not mentioned?
Which is a better wallet: Ledger Nano X or Exodus?
Consider both your short-term needs and the long-term protection of your assets
When choosing crypto wallets, many users base their decisions on day-to-day asset management needs and perceived wallet or device security. However, savvy crypto users first consider a wallet's ability to handle long-term security scenarios.
Long-term security includes expected essentials like backup and recovery tools, and often-overlooked features related to secure and fault-proof third-party recovery. Wait, what's third-party recovery? You can think of third-party recovery as your ability to allow crypto assets to be inherited by successors. All crypto investors should have a comprehensive security strategy for the full life cycle of their crypto assets.
Let's begin by helping you understand the pros and cons of the Ledger Nano X hardware wallet and the Exodus software wallet for day-to-day activities, as well as considering their ability to safeguard the long-term security of your assets.
Overview
The Ledger Nano X and Exodus wallets both provide a wide variety of features and support a broad spectrum of cryptocurrencies, making them suitable for diverse crypto portfolios.
At a high level, several differences are clear:
Ledger Nano X
- Form: A hardware wallet, with mobile-centric usability via Bluetooth.
- General Usability: User-friendly (with necessary trade-offs due to its more-robust security features).
- Design: Compact and durable. The de facto standard for securing transactions on desktops.
- Price Point: It's not free, like software wallets are.
Exodus
- Form: A software wallet, available in both mobile and desktop versions.
- General Usability: Easy to use, and has particularly well-reviewed customer support.
- Design: Built-in exchange features and a moderate number of integrations.
- Price Point: The wallet software is free; the company makes money on exchange services provided through the wallet.
The decision between the two will likely hinge on individual preferences for target security requirements, preferred platforms (mobile or desktop), and should take into account the planned frequency of use.
Approach to comparison
Now, let's have a closer look.
When choosing the best hardware wallet for cryptocurrency security, you may wonder not only which is better, the Ledger Nano X or the Exodus, but also:
- What happens if your wallet is lost or stolen? (How well can these wallets recover from user errors?)
- How do these wallets handle more advanced scenarios like inheritance of crypto assets?
- How easy to use are these wallets?
- How do their security features compare?
This article compares important characteristics for these two popular wallets. We’ll break down the strengths and weaknesses of each, focusing on security, ease of use, and backup and recovery methods. By the end of this comparison, you’ll clearly understand which wallet is right for you, as well as how to recover your crypto assets in case of accidents.
What happens if your wallet is lost or stolen?
Wise wallet owners recognize the critical importance of crypto recovery before they find themselves in an unexpected bind! That's why it's important to understand the fundamental topic of crypto asset longevity, including features such as backup, recovery, and inheritance for crypto assets. These considerations are central to long-term planning.
Technical security is essential, but in the world of crypto, the degree to which backup and recovery solutions are foolproof for users is at least equally important. Here are the backup and recovery options for these two wallets:
Ledger Nano X | Exodus | |
Backup & Recovery methods | Recommends Recovery Seed Phrase be written on paper, or engraved onto metallic plates. | Recommends Recovery Seed Phrase be written on paper, or using iCloud or Google Account saving it along with your everyday passwords. |
Optional paid subscription | Ledger Recover, a centralized 3rd-party cloud service, highly criticized by the crypto community. Clouds are not safe — especially when operated by multiple 3rd parties. | No. |
How do these wallets handle Crypto Inheritance?
Crypto Inheritance Features
Currently, most crypto wallets, including the Ledger Nano X and Exodus, lack any features for establishing and managing crypto inheritance. This gap presents a challenge for users who want to be sure that their crypto assets can be transferred to their heirs.
Ledger Nano X | Exodus | |
Backup |
- Written only | - Written only |
Inheritance | No | No |
Decentralized backup with Vault12 | Yes | Yes |
Inheritance Management with Vault12 | Yes | Yes |
Backup and recovery differentiators
Ledger Nano X Recover service Disadvantages:
- The optional Ledger Recover backup service is a paid service provided by three corporations that each hold parts of the user’s seed phrase in a cloud. This introduces risks, as the seed phrase could potentially be accessed via subpoena; or business partners could terminate agreements or become involved in lawsuits that result in locked data or resources (like, for example, Gemini and Genesis). These scenarios contain multiple potential points of failure.
- Very important detail: The terms of the optional Ledger Recover service do not mention support for inheritance, meaning any unfortunate accident related to the user could make crypto assets unrecoverable for his or her successors. Ledger itself suggests using 3rd-party crypto inheritance services for those purposes.
Ledger Nano X Recover service Advantages:
- People have different preferences. If a user is comfortable trusting a bank with their assets, they might also feel confident using Ledger Recover for securing their seed phrase backup (even though Ledger is not providing the entire cloud backup solution).
Exodus backup Disadvantages:
- Exodus has a cloud backup feature that comes with similar security assumptions and risks as all other passwords stored in your cloud provider. It is not recommended to rely on cloud backups for significant crypto balances.
Exodus backup Advantages:
- Exodus does offer a one-click solution for backup for insignificant balances of crypto.
How easy are these crypto wallets to use?
Let's compare the key aspects of both wallets side by side, and then summarize what really stands out for user convenience:
Ledger Nano X | Exodus | |
Display |
1” Monochrome OLED, | Full smartphone screen |
Input interface | 2 click buttons | Full smartphone screen |
Cable | USB-C | n/a |
Wireless | Bluetooth | As smartphone |
Platforms | macOS, Windows, Linux, Android, iOS, Browser Extension (3rd party) |
iOS, Android, Browser Extension |
3rd party wallets and dapps support | MetaMask, Exodus + 28 more | Ledger, Trezor |
Password manager & 2FA | FIDO2 2FA & Passkeys, Password Manager | n/a |
Product size & weight | 72 x 19 x 12 mm / 34g | - |
Convenience features | Battery (Up to 5 hours in use) | Exchange support |
Number of supported coins | 5,500+ | 200+ |
Price | $149 | $0 |
Crypto wallet user experience (UX) differences

Ledger Nano X with Smartphone UX
Ledger Nano X Disadvantages:
- The display is literally the size of a coin: very uncomfortable to use.
- Requires two-handed operation, making it difficult to use with a phone simultaneously — contrary to some misleading ads.
- The buttons are stiff, making operations cumbersome.
Ledger Nano X Advantages:
- Offers Bluetooth connectivity — works with or without a cable, at least with smartphones.
- Wide support for third-party wallets and dapps, allowing the Ledger Nano X to sign transactions directly in MetaMask, Uniswap, and other platforms without relying on Ledger Live software. This is a huge advantage for DeFi users.
Exodus UX Disadvantages:
- As a product that prioritizes ease of use, Exodus does not offer a full suite of advanced features such as fiat currency on/off ramps or advanced Web3 / DeFi integrations.
- The desktop version of Exodus offers more features than the mobile version (e.g., portfolio management tools, Trezor hardware integration, and a broader set of supported cryptocurrencies).
Exodus UX Advantages:
- Exodus is generally more user-friendly than the Ledger Nano X (and other hardware wallets).
How do these wallets' security features compare?
Now, we dive deeper into the core specification of every hardware wallet: security features.
| Ledger Nano X | Exodus | |
| PIN-code | 4 - 8 digits | up to 6 digits |
| BIP39 Passphrase | Yes | No |
| Open-source | Partial | Partial |
| Secure Element | Yes | No |
| Multisignature | Yes | No |
Crypto wallet security feature differentiators
Ledger Nano X security Disadvantages:
- Some critical components are closed-source. This raises concerns, especially after the controversial introduction of the Ledger Recover backup service, which challenged the previous assumption that the Secure Element could never transmit the recovery seed phrase outside the hardware wallet.
Ledger Nano X security Advantages:
- Includes a Secure Element, giving Ledger devices a strong reputation for withstanding physical attacks. This is important for users who prefer not to complicate their security with BIP39 passphrases, prioritizing ease of use.
Exodus security Disadvantages:
- Portions of the Exodus wallet are closed-source, preventing full transparency of its code security.
- Exodus, like all software wallets, operates in an inherently less-secure operating environment than a hardware wallet.
- As a software wallet, Exodus lacks a Secure Element.
- Exodus lacks support for some common security extensions such as 2-factor authentication, creation of multisignature transactions, and entry of a wallet "extra word" passphrase.
Exodus security Advantages:
- Some of Exodus's security disadvantages could be mitigated by using Exodus together (integrated) with Ledger Nano X (they are compatible with each other).
Summary of Ledger Nano X and Exodus Comparison
The Ledger Nano X and Exodus both provide a respectable set of features, and support a broad spectrum of cryptocurrencies, making them suitable for diverse crypto portfolios.
The Ledger Nano X is a mobile-friendly, security-oriented solution, and offers a balance of security and convenience features. It provides a small display and uncomfortable input, but with the advantages of a Secure Element and wireless connectivity options like Bluetooth.
On the other hand, Exodus is free and simple, but provides fewer security capabilities. It's great for beginning users and suitable for relatively small amounts of crypto.
The decision between the two will likely hinge on individual preferences for the target use case and balance, and should take into account the planned frequency of use.
Given their convenient integration, the best of all worlds could be to use both wallets, holding larger amounts of crypto in your Ledger Nano X wallet while keeping a small, ready-to-transact "petty cash" stash in your Exodus wallet.
Whichever you choose, remember to add crypto inheritance to your choice of wallet to ensure the long-term safety of your digital assets.
Vault12 Guard: a decentralized solution for Crypto Inheritance
Vault12 is the pioneer in Crypto Inheritance Management, and delivers an easy-to-use and secure method for assigning a legacy contact to your crypto wallets. This enables you to pass on your wallet seed phrases and private keys for all types of digital assets to future generations. Vault12 Guard is designed for everyday people, yet strong enough for Crypto OGs.
Vault12 Guard has a uniquely-secure design. Utilizing advanced encryption and decentralized storage, it ensures that crypto assets are not only safe but also transferable under predefined conditions, filling a critical need unmet by most traditional hardware wallets. Vault12 Guard applies a hybrid approach of software fused with the hardware-based Secure Element of phone devices (The Secure Enclave for iOS devices, and Strongbox for Google devices). Vault12 Guard's decentralized design reduces possible points of failure. Nothing is stored on cloud servers or Vault12 servers, and no assets are stored on local devices, making them less of a target.
From a user perspective, the Vault12 Guard app asks users to appoint one or more people (or mobile devices) as Guardians. The designated Guardians are entrusted to protect the user's comprehensive collection of wallet seed phrases and private keys, which are safely stored within a decentralized digital Vault. Its simple, user-friendly workflow removes the necessity for regularly revising wallet inventories or modifying instructions for your lawyers — a process that otherwise could lead to privacy breaches.
Both the Ledger Nano X and Exodus are compatible with Vault12 Guard Inheritance. This addresses the seed phrase backup dilemma for any hardware wallet. It also makes less-secure backup methods, such as paper or steel plates, unnecessary.
Comparison of Ledger Nano X and Trezor Safe 5
Your choice will likely depend on your preferences for UI, portability, and integrations.
When choosing the best hardware wallet for cryptocurrency security, you may wonder:
- Which is better, the Ledger Nano X or the Trezor Safe 5?
- How easy to use are these wallets?
- How do their security features compare?
- Do these wallets have vulnerabilities, and have they been hacked?
- What happens if your wallet is lost or stolen?
- How do these wallets handle Crypto Inheritance Management?
This article compares important characteristics for these two popular wallets. We’ll break down the strengths and weaknesses of each, focusing on security, ease of use, and backup methods.
Additionally, we’ll explore the fundamental topic of inheritance and backup for crypto assets — a crucial aspect of long-term planning. By the end of this comparison, you’ll clearly understand which wallet is right for you, and how to address the often-overlooked safety issue of recovering your crypto assets in case of loss.
How easy are these crypto wallets to use?
Let's compare the key aspects of both wallets side by side, and then summarize what really stands out for user convenience:
Ledger Nano X | Trezor Safe 5 | |
Display | 1” Monochrome OLED, |
1.54" Color LCD, |
Input interface |
2 click buttons |
Touchscreen, Haptic feedback |
Cable | USB-C | USB, MicroSD card slot |
Wireless | Bluetooth 5.2 | No |
Companion Apps | macOS, Windows, Linux, Android, iOS |
macOS, Windows, Linux, Android |
3rd party wallets and dapps support | 50+ | 9+ |
Password manager & 2FA | FIDO2 2FA & Passkeys, | FIDO2 2FA |
Product size & weight | 72 x 19 x 12 mm / 34g | 66 x 40 x 8 mm / 23g |
Convenience features | Battery (Up to 5 hours in use) | Magnetic dock |
Number of supported coins | 5,500+ | 1,600+ |
Price | $149 | $165 |
Crypto wallet user experience (UX) differences
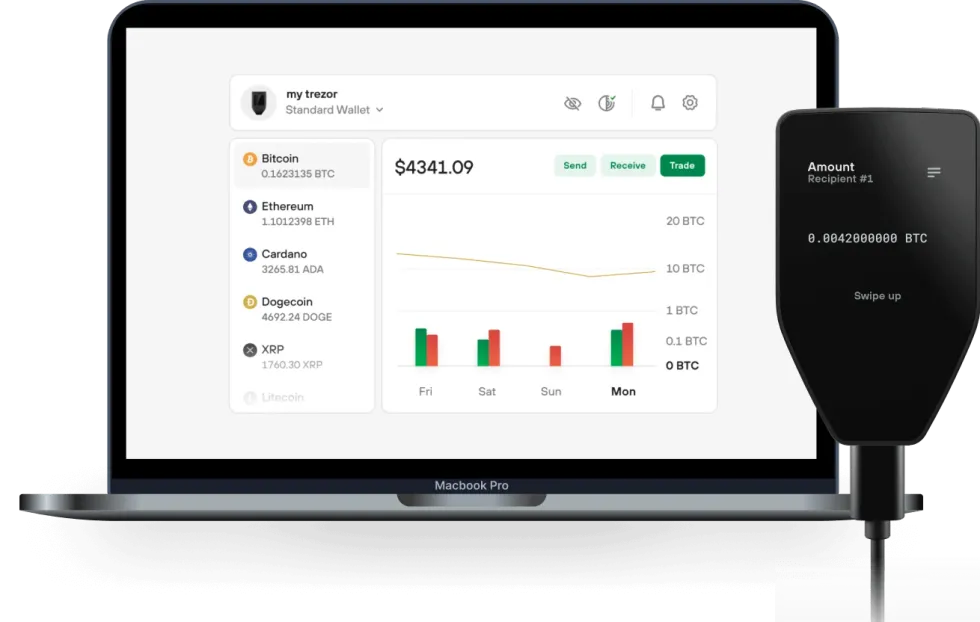 Trezor Safe 5 wallet and desktop software
Trezor Safe 5 wallet and desktop softwareLedger Nano X Disadvantages:
- The display is literally the size of a coin: very uncomfortable to use.
- Requires two-handed operation, making it difficult to use with a phone simultaneously — contrary to some misleading ads.
- The buttons are stiff, making operations cumbersome.
Ledger Nano X Advantages:
- Offers Bluetooth connectivity — works with or without a cable, at least with smartphones.
- Wide support for third-party wallets and dapps, allowing the Ledger Nano X to sign transactions directly in MetaMask, Uniswap, and other platforms without relying on Ledger Live software. This is a huge advantage for DeFi users.
Trezor Safe 5 Disadvantages:
- No wireless connectivity: you always have to use a cable.
- iOS integration is a view-only, you can only watch balance and can't send transactions from iOS app.
Trezor Safe 5 Advantages:
- The display is convenient to work with on a regular basis, and easy to read.
- The touchscreen and input are very well-thought-out experiences on Trezor Safe 5 — you can use it without any discomfort.
 Ledger Nano X with Smartphone UX
Ledger Nano X with Smartphone UXHow do these wallets' security features compare?
Now, we dive deeper into the core specification of every hardware wallet: security features.
| Ledger Nano X | Trezor Safe 5 | |
| PIN-code | 4 - 8 digits | up to 50 digits |
| BIP39 Passphrase | Yes | Yes |
| Open-source | Partial | Full |
| Secure Element | Yes | Yes, and it's NDA-free |
| Multisignature | Yes | Yes |
Crypto wallet security feature differentiators
Ledger Nano X Disadvantages:
- Critical components like the Secure Element and its operating system are closed-source. This has raised concerns, especially after the controversial introduction of the Ledger Recover backup service, which challenged the assumption that the Secure Element could never transmit the recovery seed phrase outside the hardware wallet.
Ledger Nano X Advantages:
- Includes a Secure Element, giving Ledger devices a strong reputation for withstanding physical attacks. This is important for users who prefer not to complicate their security with BIP39 passphrases (prioritizing ease of use).
Trezor Safe 5 Disadvantages:
- The hardware and software are not not fully open-source, but Trezor mitigates this limitation architecturally, so that the seed phrase is not touched by closed source software. The Secure Element chip is responsible for secure boot only, and it is NDA-free: Trezor is not bound by Non-Disclosure Agreements (NDAs) that would restrict them from publicly disclosing any security flaws.
Trezor Safe 5 Advantages:
- With its new flagship product, Trezor raises the security bar by incorporating Secure Elements into their products. Further, its Secure Element chips are NDA-free.
- Allows for longer PIN codes, which might appeal to particularly cautious users.
Have there been vulnerabilities or hacks of these wallets?
There have been vulnerabilities and hacks associated with both the Ledger and Trezor products. Let's review the history of hacks for the manufacturers, which is more representative than for individual models.
Far from delivering uncompromised security, these wallets are routinely subject to malware, supply chain, and firmware vulnerabilities. Here are some recent notable incidents:
Ledger Vulnerabilities:
- The Connect Kit Attack (2023): The Connect Kit breach was discovered by the security teams of Ledger.
- Ledger User Data Breach (2020): A major data breach exposed the personal information of thousands of customers, leading to phishing attacks.
- Another User Data Breach (2021): Ledger announced on Twitter that it has been targeted by rogue Shopify team members who exported over 200 merchants’ customer databases.
- Ledger Live (2020): Users were exposed to basic double spending attacks, amplified double spending attacks, and DoS attacks without user consent.
- Potential Supply Chain Attack Vulnerability (2020): Kraken Security Labs Identifies Supply Chain Attacks Against Ledger Wallets.
Trezor Vulnerabilities:
- Ability to Physically Hack Trezor T Wallet (2023): Crypto Security Firm Unciphered Claims Ability to Physically Hack Trezor T Wallet
- Five Reported Vulnerabilities in Two Models of Trezor Hardware Wallets (2019): Ledger’s Attack Lab has found five vulnerabilities in hardware wallets of its direct competitor Trezor.
- Kraken Identifies Critical Flaw in Trezor Hardware Wallets (2020): Kraken Security Labs has devised a way to extract seeds from both cryptocurrency hardware wallets offered from industry leader Trezor, the Trezor One and Trezor Model T.
What happens if your wallet is lost or stolen?
Security is essential, but in the world of crypto, the degree to which backup and recovery solutions are foolproof for users is equally important. Here are the backup and recovery options for these two wallets:
Ledger Nano X | Trezor Safe 5 | |
Backup & Recovery methods | Recommend Recovery Seed Phrase be written on paper, or engraved onto metallic plates. | Recommend Recovery Seed Phrase be written on paper, or engraved onto metallic plates. |
Optional paid subscription | Ledger Recover, a centralized 3rd-party cloud service, highly criticized by the crypto community. Clouds are not safe — especially when operated by multiple 3rd parties. | No. |
Backup and recovery differentiators
Ledger Nano X Recover service Disadvantages:
- The optional Ledger Recover backup service is a paid service provided by three corporations that each hold parts of the user’s seed phrase in a Cloud. This introduces risks, as the seed phrase could potentially be accessed via subpoena; business partners could terminate agreements or become involved in lawsuits that result in locked data or resources (like, for example, Gemini and Genesis); and there are multiple potential points of failure.
Ledger Nano X Recover service Advantages:
- People have different preferences. If a user is comfortable trusting a bank with their assets, they might also feel confident using Ledger Recover for securing their seed phrase backup (even though Ledger is not providing the complete cloud backup solution).
Trezor Safe 5 backup Disadvantages:
- Trezor has a Multishare backup service, but it is fully manual, and challenging to maintain. The user is responsible for generating, distributing, and keeping track of the encrypted shards.
Trezor Safe 5 backup Advantages:
- Trezor does offer a Multishare backup option for those who are able and willing to set it up.
How do these wallets handle Crypto Inheritance Management?
Crypto Inheritance Features
Currently, most hardware wallets, including the Ledger Nano X and Trezor Safe 5, lack any features for establishing and managing crypto inheritance. This gap presents a challenge for users who want to be sure that their crypto assets can be transferred to their heirs.
Ledger Nano X | Trezor Safe 5 | |
Backup |
- Written only | - Written only - Manual sharing of shards |
Inheritance | No | No |
Decentralized backup with Vault12 | Yes | Yes |
Inheritance Management with Vault12 | Yes | Yes |
Summary of Ledger Nano X and Trezor Safe 5 Comparison
The Ledger Nano X and Trezor Safe 5 both provide a variety of security measures, and support a broad spectrum of cryptocurrencies, making them suitable for diverse crypto portfolios.
The Ledger Nano X is more mobile-friendly, and offers a balance of security and convenience features. It offers a small display and uncomfortable input, but with the advantages of a Secure Element and wireless connectivity options like Bluetooth.
On the other hand, the Trezor Safe 5, at the same price, boasts more open-sourced and NDA-free framework, reasonably sized display with colors, and touchscreen interface for enhanced user interaction, but with reduced convenience features working only with USB connections and missing iOS integration.
The decision between the two will likely hinge on individual preferences for the target platform (mobile or desktop), and should take into account the planned frequency of use.
Whichever you choose, remember to add crypto inheritance to your choice of wallet to ensure the long-term safety of your digital assets.
Vault12 Guard: a decentralized solution for Crypto Inheritance
Vault12 is the pioneer in Crypto Inheritance Management, and delivers an easy-to-use and secure method for assigning a legacy contact to your crypto wallets. This enables you to pass on your wallet seed phrases and private keys for all types of digital assets to future generations. Vault12 Guard is designed for everyday people, yet strong enough for Crypto OGs.
Vault12 Guard has a uniquely-secure design. Utilizing advanced encryption and decentralized storage, it ensures that crypto assets are not only safe but also transferable under predefined conditions, filling a critical need unmet by most traditional hardware wallets. Vault12 Guard applies a hybrid approach of software fused with the hardware-based Secure Element of phone devices (The Secure Enclave for iOS devices, and Strongbox for Google devices). Vault12 Guard's decentralized design reduces possible points of failure. Nothing is stored on cloud servers or Vault12 servers, and no assets are stored on local devices, making them less of a target.
From a user perspective, the Vault12 Guard app asks users to appoint one or more people (or mobile devices) as Guardians. The designated Guardians are entrusted to protect the user's comprehensive collection of wallet seed phrases and private keys, which are safely stored within a decentralized digital Vault. Its simple, user-friendly workflow removes the necessity for regularly revising wallet inventories or modifying instructions for your lawyers — a process that otherwise could lead to privacy breaches.
Both the Ledger Nano X and Trezor Safe 5 are compatible with Vault12 Guard Inheritance. This addresses the seed phrase backup dilemma for any hardware wallet. It also makes less-secure backup methods, such as paper or steel plates, unnecessary.
Ledger Stax and Ledger Nano X Wallets: Which is right for you?
The right wallet for you depends on your design preferences and price sensitivity
When choosing hardware wallets, many crypto users base their decisions on day-to-day asset management needs and perceived device security. However, savvy crypto users first consider a wallet's ability to handle long-term security scenarios. Long-term security includes expected essentials like backup and recovery tools, and also often-overlooked features related to secure and fault-proof third-party recovery. You can think of third-party recovery as your ability to allow crypto assets to be inherited by successors. Successful crypto users require a comprehensive security strategy for the full life cycle of crypto assets. This article will help you achieve that.
Let's jump into helping you understand the pros and cons of the Ledger Stax and Ledger Nano X hardware wallets for day-to-day activities, as well as their potential to safeguard the long-term security and longevity of your assets.
Overview
The Ledger Stax and Ledger Nano X both provide a wide variety of reliable security features and support a broad spectrum of cryptocurrencies, making them suitable for diverse crypto portfolios. However, several differences are clear:
Ledger Stax
- Mobile-Centric Usability: Designed with mobility in mind, the Ledger Stax features wireless connectivity options like Bluetooth and NFC, making it highly compatible with mobile platforms. Stax also has a longer battery life (up to 10 hours versus Nano X's 5).
- Premium Design: Its unconventionally large display enhances readability, though it comes with slightly slower responsiveness.
- Price Point: Positioned as a premium product, its cost reflects its advanced features and sleek design.
Ledger Nano X
- Mobile-Centric Usability: Offers Bluetooth connectivity — works with or without a cable, at least with smartphones.
- Design: A bit more compact than Stax. User input is via buttons, not touchscreen.
- Price Point: Not so overpriced.
In terms of crypto asset longevity features, such as backup, recovery, and crypto inheritance, both devices provide industry-standard and proprietary options with certain trade-offs, as well as compatibility with third-party solutions like Vault12 Guard for succession planning scenarios.
The decision between the two will likely hinge on individual preferences for the target platform (mobile or desktop), and should take into account the planned frequency of use.
Approach to comparison
When choosing the best hardware wallet for cryptocurrency security, you may wonder:
- Which is better, the Ledger Stax or the Ledger Nano X?
- How easy to use are these wallets?
- How do their security features compare?
- Do these wallets have vulnerabilities, and have they been hacked?
- What happens if your wallet is lost or stolen?
- How do these wallets accomodate user errors, and complex scenarios like inheritance of crypto assets?
This article compares important characteristics for these two popular wallets. We’ll break down the strengths and weaknesses of each, focusing on security, ease of use, and backup and recovery methods.
By the end of this comparison, you’ll clearly understand which wallet is right for you, as well as how to recover your crypto assets in case of accidents.
What happens if your wallet is lost or stolen?
Wise wallet owners recognize the critical importance of crypto recovery before they find themselves in an unexpected bind! That's why it's important to understand the fundamental topic of crypto asset longevity, including features such as backup, recovery, and inheritance for crypto assets. These considerations are central to long-term planning.
Technical security is paramount, but in the world of crypto, the degree to which backup and recovery solutions are foolproof for users is at least equally important. Here are the backup and recovery options for these two wallets:
Ledger Stax | Ledger Nano X | |
Backup & Recovery methods | Recommends Recovery Seed Phrase be written on paper, or engraved onto metallic plates. | Recommends Recovery Seed Phrase be written on paper, or engraved onto metallic plates. |
Optional paid subscription | Ledger Recover, a centralized 3rd-party cloud service, highly criticized by the crypto community. Clouds are not safe — especially when operated by multiple 3rd parties. | Ledger Recover, a centralized 3rd-party cloud service, highly criticized by the crypto community. Clouds are not safe — especially when operated by multiple 3rd parties. |
How do these wallets handle Crypto Inheritance?
Crypto Inheritance Features
Currently, most hardware wallets, including the Ledger Stax and Ledger Nano X, lack any features for establishing and managing crypto inheritance. This gap presents a challenge for users who want to be sure that their crypto assets can be transferred to their heirs.
Ledger Stax | Ledger Nano X | |
Backup |
- Written only | - Written only - Optional 3rd party KYC-based cloud |
Inheritance | No | No |
Decentralized backup with Vault12 | Yes | Yes |
Inheritance Management with Vault12 | Yes | Yes |
Backup and recovery differentiators
Ledger Stax and Ledger Nano X both have similar recovery service Disadvantages:
- The optional Ledger Recover backup service is a paid service provided by three corporations that each hold parts of the user’s seed phrase in a Cloud. This introduces risks, as the seed phrase could potentially be accessed via subpoena; or business partners could terminate agreements or become involved in lawsuits that result in locked data or resources (like, for example, Gemini and Genesis). These scenarios contain multiple potential points of failure, and should be taken into account.
- Very important detail: The terms of the optional Ledger Recover service do not mention support for inheritance, meaning any unfortunate accident related to the user will make crypto assets unrecoverable for his or her successors. Ledger itself suggests using 3rd-party crypto inheritance services for those purposes.
Ledger Stax and Ledger Nano X both have similar recovery service Advantages:
- People have different preferences. If a user is comfortable trusting a bank with their assets, they may also feel confident using Ledger Recover for securing their seed phrase backup (even though Ledger is not providing the entire cloud backup solution).
 User holding a mobile phone and using Ledger Stax as FIDO U2F security key
User holding a mobile phone and using Ledger Stax as FIDO U2F security keyHow easy are these crypto wallets to use?
Let's compare the key aspects of both wallets side by side, and then summarize what really stands out for user convenience:
Ledger Stax | Ledger Nano X | |
Display | 3,7” black and white E Ink, | 1” Monochrome OLED, |
Input interface | Touchscreen |
2 click buttons |
Cable | USB-C | USB-C |
Wireless |
Bluetooth, | Bluetooth |
Companion Apps | macOS, Windows, Linux, Android, iOS | macOS, Windows, Linux, Android, iOS |
3rd party wallets and dapps support | 50+ | 50+ |
Password manager & 2FA | FIDO2 2FA & Passkeys, | FIDO2 2FA & Passkeys,Password Manager |
Product size & weight | 85 x 54 x 6 mm / 45g | 72 x 19 x 12 mm / 34g |
Convenience features | Battery (Up to 10 hours in use) | Battery (Up to 5 hours in use) |
Number of supported coins | 5,500+ | 5,500+ |
Price | $399 | $149 |
Crypto wallet user experience differences
 Ledger Nano X with Smartphone UX
Ledger Nano X with Smartphone UXLedger Stax UX Disadvantages:
- The display has a noticeable response delay due to the "E Ink" touchscreen technology, and could be irritating.
- Not all apps are ported to Stax yet. Even the native Passwords app still has no release date identified as of this article's publish date, so check in advance whether your favorite network/coin is supported.
- Extremely expensive. The value in Stax is more about design, rather than practical aspects.
Ledger Stax UX Advantages:
- Huge informative display and "Clear Signing" allows you to review and confirm all transaction details directly on Ledger Stax and in a human-readable language before they are signed and sent. This enhances security and ensures that you see exactly what you are approving in a secure and tamper-proof manner.
- Offers Bluetooth connectivity as well as NFC — works with or without a cable, at least with smartphones.
- Wide support for third-party wallets and dapps, allowing the Ledger Stax to sign transactions directly in MetaMask, Uniswap, and other platforms without relying on Ledger Live software. This is a huge advantage for DeFi users.
Ledger Nano X Disadvantages:
- The display is literally the size of a coin: very uncomfortable to use.
- Requires two-handed operation, making it difficult to use with a phone simultaneously — contrary to some misleading ads.
- The buttons are stiff, making operations cumbersome.
- No NFC.
Ledger Nano X Advantages:
- A bit more compact than Stax while also offering Bluetooth connectivity — works with or without a cable, at least with smartphones.
- Wide support for third-party wallets and dapps, allowing the Ledger Nano X to sign transactions directly in MetaMask, Uniswap, and other platforms without relying on Ledger Live software. This is a huge advantage for DeFi users.
- Not so overpriced.
How do these wallets' security features compare?
Now, we dive deeper into the core specification of every hardware wallet: security features.
| Ledger Stax | Ledger Nano X | |
| PIN-code | 4 - 8 digits | 4 - 8 digits |
| BIP39 Passphrase | Yes | Yes |
| Open-source | Partial | Partial |
| Secure Element | Yes | Yes |
| Multisignature | Yes | Yes |
Crypto wallet security feature differentiators
Ledger Stax and Ledger Nano X both have similar security feature Disadvantages:
- Critical components like the Secure Element and its operating system are closed-source. This raises concerns, especially after the controversial introduction of the Ledger Recover backup service, which challenged the previous assumption that the Secure Element could never transmit the recovery seed phrase outside the hardware wallet.
Ledger Stax and Ledger Nano X both have similar security feature Advantages:
- Includes a Secure Element, giving Ledger devices a strong reputation for withstanding physical attacks. This is important for users who prefer not to complicate their security with BIP39 passphrases, prioritizing ease of use.
- Clear Signing is also a security feature.
Have there been vulnerabilities or hacks of these wallets?
There have been some vulnerabilities and hacks associated with Ledger products in the past — let's consider their "hack history." While relatively secure, most crypto wallets — even hardware wallets — can not provide perfect security, and are routinely subject to malware, supply chain, and firmware vulnerabilities. Here are some recent notable incidents:Ledger Vulnerabilities:
- The Connect Kit Attack (2023): The Connect Kit breach was discovered by the security teams of Ledger.
- Ledger User Data Breach (2020): A major data breach exposed the personal information of thousands of customers, leading to phishing attacks.
- Another User Data Breach (2021): Ledger announced on Twitter that it has been targeted by rogue Shopify team members who exported over 200 merchants’ customer databases.
- Ledger Live (2020): Users were exposed to basic double spending attacks, amplified double spending attacks, and DoS attacks without user consent.
- Potential Supply Chain Attack Vulnerability (2020): Kraken Security Labs Identifies Supply Chain Attacks Against Ledger Wallets.
No software is perfect, and no wallet is ideal. However, some designs have been compromised more than others.
Summary of Ledger Stax and Ledger Nano X Comparison
The Ledger Stax and Ledger Nano X both provide a respectable set of security measures, and support a broad spectrum of cryptocurrencies, making them suitable for diverse crypto portfolios.
The Ledger Stax is more mobile-friendly, and offers a balance of security and convenience features at a very premium price. It offers an unconventionally large display with delayed response, with the advantage of wireless connectivity options like Bluetooth.
On the other hand, the Ledger Nano X, at a lower price point, is still mobile-friendly and offers a balance of security and convenience features. It offers a small display and uncomfortable input, but still has the advantages of a Secure Element and wireless connectivity options like Bluetooth.
The decision between the two will likely hinge on individual preferences for the target user interface with screen, and should take into account the planned frequency of use.
Whichever you choose, remember to add crypto inheritance to your choice of wallet to ensure the long-term safety of your digital assets. Both the Ledger Stax and Ledger Nano X are compatible with Vault12 Guard Inheritance planning.Vault12 Guard: a decentralized solution for Crypto Inheritance
Vault12 is the pioneer in Crypto Inheritance Management, and delivers an easy-to-use and secure method for assigning a legacy contact to your crypto wallets. This enables you to pass on your wallet seed phrases and private keys for all types of digital assets to future generations. Vault12 Guard is designed for everyday people, yet strong enough for Crypto OGs.
Vault12 Guard has a uniquely-secure design. Utilizing advanced encryption and decentralized storage, it ensures that crypto assets are not only safe but also transferable under predefined conditions, filling a critical need unmet by most traditional hardware wallets. Vault12 Guard applies a hybrid approach of software fused with the hardware-based Secure Element of phone devices (The Secure Enclave for iOS devices, and Strongbox for Google devices). Vault12 Guard's decentralized design reduces possible points of failure. Nothing is stored on cloud servers or Vault12 servers, and no assets are stored on local devices, making them less of a target.
From a user perspective, the Vault12 Guard app asks users to appoint one or more people (or mobile devices) as Guardians. The designated Guardians are entrusted to protect the user's comprehensive collection of wallet seed phrases and private keys, which are safely stored within a decentralized digital Vault. Its simple, user-friendly workflow removes the necessity for regularly revising wallet inventories or modifying instructions for your lawyers — a process that otherwise could lead to privacy breaches.
Both the Ledger Stax and Ledger Nano X are compatible with Vault12 Guard Inheritance. This addresses the seed phrase backup dilemma for any hardware wallet. It also makes less-secure backup methods, such as paper or steel plates, unnecessary.
MetaMask browser extension
Browser extension, Version 1.0.10
Welcome to this guide on securely setting up a MetaMask wallet. This guide focuses on the security choices you can make when setting up your MetaMask wallet; if you are looking for the official setup guide, please click here.
MetaMask is your entry point to the world of Ethereum - a blockchain platform designed for running apps and smart contracts.
This guide is focused on the MetaMask browser extension. Read our iOS and Android guides.
Step 1. What is MetaMask?
MetaMask consists of two main parts: a wallet and a web browser. The wallet supports any token compatible with Ethereum, and the web browser is preconfigured for interacting with dapps and smart-contracts.
MetaMask was first released in 2016, as a browser-extension, by ConsenSys - the first company focused on building decentralized tools and infrastructure. Both MetaMask and ConsenSys have played monumental roles in bringing Ethereum to the mainstream.
It is hard to overstate the effect MetaMask has had on the Ethereum ecosystem. By making dapps and smart-contracts simple and intuitive to use, activity on the Ethereum blockchain has enjoyed consistent growth.
Metamask is an open-source wallet, active development happens on github. The wallet has tons of features, and is constantly being updated and improved.
MetaMask is available as a browser-extension for Chrome, Firefox, Brave, and Edge. In September of 2020, MetaMask released a mobile app for iOS and Android.
Step 2. How can you download MetaMask?
MetaMask is installed as a browser-extension. The process of installing MetaMask involves going to the extension/add-on store for your browser and downloading MetaMask.
- The first step is crucial. Navigate to the official MetaMask website. The only valid URL for metamask is https://metamask.io
- Verify the closed lock to the left of the URL. This signifies you are connected through SSL - an encrypted connection. SSL encrypts data in transit and prevents attacks like phishing, and man-in-the-middle attacks.
- If you do not see the closed lock, exit the page immediately.
How can you prevent phishing attacks when you download MetaMask?
- MetaMask is a target for phishing attacks. Phishing is a way of stealing your credentials, by tricking you into downloading a malicious version of the app you want to download. A common tactic for phishers is to purchase domain names of common misspellings - hoping you make a mistake typing the URL.
- Advanced phishers will install an SSL certificate on their phishing site. For extra verification, click on the closed lock, then click on `Certificate` to bring up the certificate details. Verify that the certificate was issued to https://metamask.io - the only valid URL for MetaMask.
How do you go from the MetaMask download page to your browser's extension store?
After you have verified you are on the correct URL - https://metamask.io - click on `Download` in the upper right corner, or `Download Now` in the main section.
- The MetaMask download page contains the official links to download MetaMask from your web browser's extension store. By following or verifying the links from the official MetaMask site, we can prevent phishing.
- On the MetaMask download page, click on your Web Browser's icon to go to the browsers extension store

Which browser extension or Add-On stores can you use to install MetaMask?
- Chrome Web Store - https://chrome.google.com/webstore/detail/metamask/nkbihfbeogaeaoehlefnkodbefgpgknn?hl=en
- Firefox Browser Add-Ons - https://addons.mozilla.org/en-US/firefox/addon/ether-metamask/
- Microsoft Edge Add-Ons - https://microsoftedge.microsoft.com/addons/detail/metamask/ejbalbakoplchlghecdalmeeeajnimhm?hl=en-US
- Brave Browser (Brave Browser is a Chromium-based browser, it sources add-ons from the Chrome Web Store.) - https://chrome.google.com/webstore/detail/metamask/nkbihfbeogaeaoehlefnkodbefgpgknn?hl=en
Follow the official link from MetaMask to your browser's web store, then click `Add to browser`.
Before installing, you will get a pop-up letting you know MetaMask can access and alter data on any website you visit. Let's go over the details
Why does MetaMask need access to your browser's data?
- Since MetaMask works by connecting your web-browser to an application running on the blockchain, MetaMask needs these permissions to form the connection and establish the flow of data between the blockchain and your web browser.
- To maximize security, consider running MetaMask in a browser profile that only consists of MetaMask. This creates a separation between regular browsing activities and MetaMask activities.
- Click on `Add Extension` and MetaMask will finish installing and open a new tab with a welcome screen. Congrats! You just installed MetaMask browser-extension

Good job on safely installing MetaMask. By verifying the authenticity of the MetaMask download, like this guide shows, a whole range of attacks can be prevented. When doing anything in the world of crypto, having a security mindset is so important. Having a security mindset is the best way to prevent loss of funds or a breach of personal information.
Trust, but verify - This means even if a source is trusted, such as an official website or a trusted community member, you should always take the additional steps to verify the information - no matter what.
You are now ready to move on to the next section. Click on `Get Started` on the welcome screen.
Step 3. How can you create and setup a MetaMask wallet?
MetaMask is a very easy wallet to get started with. No email address or personal identification is required. The process consists of two main steps - creating a password and backing up your seed phrase. You will be ready to explore the world of Ethereum in just a few minutes.
MetaMask supports any token built on the Ethereum blockchain. You might come across terms such as ERC-20 and ERC-721; these are just types of tokens.
ERC-20 tokens are fungible; meaning they are like money - each token represents the same value.
ERC-721 are NFT's, non-fungible tokens - where each token represents a unique digital asset - like a collectible.
On the Ethereum Blockchain, there are a couple hundred thousand tokens in existence. MetaMask includes most of the popular tokens by default.
To add a token, simply tap `Add Token` and search for the token. If your token is not listed, select `Add Custom Token` and input the contract address - MetaMask will then pull the info automatically.
Safely backing up your MetaMask wallet is essential. This guide covers in detail how to securely back up your seed phrase in Section 5. Securely back up your seed phrase.
MetaMask uses BIP39 to generate a seed phrase for your wallet. Your seed phrase will cover every token, address, and transaction generated by your wallet. Think of it as your backup master key. Backing up your seed phrase ensures you will always have access to your funds.
When creating a new MetaMask Wallet, the default method is to create your wallet within the app. The more advanced method is to generate your own seed phrase. We created detailed guides on generating your own seed phrase. By following the right directions, you can generate a seed phrase that is more secure than the default method used by wallets.
If you already have a recovery phrase, proceed to Section 6. Initialize or import seed phrase.
Create a New Wallet in MetaMask
In this section, you are going to create a new wallet in the MetaMask browser extension using the wallet's default method. Let's get started.
To create a new wallet with a new recovery phrase in MetaMask:
- Open the MetaMask extension and tap on `Get Started`. This will bring you to the `Wallet Setup` screen
- On the `Wallet Setup` screen you will be presented with 3 options:
- `Import using seed phrase`
- `Create a new wallet` ← This is the one you want to select
Help us improve MetaMask? Before setting up your wallet, MetaMask wants to know if you want to help contribute to MetaMask development by contributing anonymous data. This is a personal decision for you to make based on your own value system. The data MetaMask wants to collect is anonymous clicks and pageviews.
- The first step is to create your password
- Create a secure password! MetaMask does not have 2FA, so creating a secure password is very important
- Make your password unique, do not reuse an old password
- Consider using a passphrase instead, a sequence of 4 or more random words
- Consider using a password generator and manager, like Bitwarden
- Setup a time frame to rotate to a new password
- Learn how to make secure passwords
- Prepare your Seed Phrase for Backup - Backing up your seed phrase is the most important step in creating a wallet. In this step, you will find your seed phrase and prepare it to be backed up. Section 5. Securely back up seed phrase of this guide focuses on how to safely backup your seed phrase.
- MetaMask will first show you your secret backup phrase, called your `Seed Phrase`, grayed out. Click in the box to reveal your seed phrase.
- There are a few options for backing up your seed phrase mentioned here, only one suggested option is secure enough - backing the seed phrase up on an encrypted medium.
- Remind me later ← Never Select this option.
- MetaMask encrypts data on the client-side, this means your seed phrase is the only method of recovering funds.
- Temporarily write your seed phrase on paper ← Only acceptable with additional safety measures
- Please read Section 5. Securely back up seed phrase, multiple additional steps need to be taken to ensure the safety of funds.
- Store seed phrase in password manager ← Never select this option.
- Your seed phrase should be nowhere near the internet.
- Store seed phrase on encrypted medium← The only good option listed
- There are a few different ways you can safely back up your seed phrase. We have done the research and compiled all the ways to do so in Section B of this guide
- To move on to the next step, you will have to write down your 12-word seed phrase. Click in the gray box to reveal your 12-word seed phrase.
Step 4. How can you verify your recovery phrase?
At this point, you will have a fully functioning cryptocurrency wallet that is able to store, send, and receive cryptocurrency. Before you put funds in your wallet, you need to verify and create a backup of your recovery phrase. Your recovery phrase is the only way to restore access to your funds if you lose access to your wallet - backing up your recovery phrase is a very important step. Before moving on to Section B, you need to find out what your recovery phrase is, so you can back it up.
WARNING: When you follow the steps to find your recovery phrase, you will be writing the recovery phrase on a piece of paper. It is very important that you back up the recovery phrase on a more reliable medium, and then destroy that piece of paper. Paper is vulnerable to accidental loss, theft, and damage. It is not the safest method of backing up your recovery phrase.
- Now you need to confirm you accurately prepared your Seed Phrase for backup. MetaMask will display your 12 words in a random order. Starting with the first word, click on each word in the correct order.
- MetaMask encrypts data on the client-side. This means all data is encrypted locally in your web-browser before being transmitted over the internet. If you lose access to your account, MetaMask cannot help you recover your account
- Pay attention to the piece of paper you have written your seed phrase on. Do not leave this paper anywhere where someone else can find it. It is advisable to destroy the paper after you have backed up your seed phrase.
- Congratulations! Your wallet has been created and is ready to be used. You have also prepared your seed phrase for backup. Read over the advice given on the Congratulations screen and click `All Done` when you are ready.
- Get ready to explore the world of Ethereum. Your MetaMask wallet can store, send, and receive any token on the Ethereum blockchain. MetaMask is more than just a wallet - it's your portal to interact with apps and smart-contracts built on Ethereum.
- Before you put funds in your wallet, you need to create a safe backup of your seed phrase. Your seed phrase is the only way to restore access to your funds if you lose access to your wallet.
You are now ready to proceed to Section 5. Securely back up your seed phrase and securely back up your funds.
Recommended Action: After you securely back up your recovery phrase, it is important to destroy the paper you temporarily wrote your recovery phase on.
Step 5. How can you securely back up your seed phrase?
If you used Vault12 to generate your recovery phrase, your recovery phrase is already securely backed up in your digital vault.
Your recovery phrase is the master key to all of your cryptocurrency funds. BRD Wallet uses BIP39, which is the current industry best practice for generating recovery phrases. The majority of modern wallets today use BIP39. This means your MetaMask seed phrase can be used to access your funds across many different wallets.
Securely backing up your recovery phrase is the most important step in creating a new wallet. To emphasize how important this is, consider how someone with your recovery phrase could access your funds without you knowing.
Imagine a bad actor has your recovery phrase, and you have your BRD Wallet locked down with 2FA, IP address whitelisting, blocked tor access, and all the other security features. The attacker could simply open any wallet application, and import your recovery phrase. The attacker now has access to all of your funds.
We want you to have a secure backup, so this never happens to you.
Nine out of ten wallet providers only mention one way to back up your recovery phrase - by writing the recovery phrase on paper. Wallet providers only mention this paper backup method because it is easy for beginners to do. Paper backups are simply not that secure.
We did extensive research and compiled the best ways to back up your recovery phrase. We cover all the most well-known options, including next-generation options like how to back up your recovery phrase in Vault12.
Once you have safely backed up your seed phrase, you can initialize your wallet using any BIP39 compatible wallet. In the next section, you will learn how you can initialize a MetaMask wallet using your seed phrase.
Step 6. How can you Initialize or import your seed phrase?
If you are following this guide from the beginning, and you created your wallet using the default approach, using the app to `Create a Wallet`, then congratulations! You are ready to start using your wallet.
However, be careful about storing large amounts of funds secured only by a wallet-generated recovery phrase.
If you followed one of our guides for pre-generating a more secure seed phrase, for instance using Vault12, and you want to use that seed phrase with your wallet - this section is for you!
In this section, you will learn how to initialize your wallet using only your recovery phrase. There are 3 main reasons to generate your wallet using this method:
- You lost access to your wallet, and you need to regain access to your wallet and your funds.
- You want to access your wallet and funds using a different wallet app.
- You want the best security, and you generated a recovery phrase using an advanced method.
The Metamask Wallet makes the process super easy and user friendly. Let's get started.
In this section you are going to create a new wallet in the MetaMask browser extension by importing your seed phrase. Let's get started.
To create a new wallet with a new recovery phrase in MetaMask:
- Click on the MetaMask extension and tap on `Get Started`. This will launch the wallet setup process.
- On the `Wallet Setup` screen you will be presented with 2 options:
- `Import Wallet`← This is the one you want to select
- `Create a new wallet`
- Help us improve MetaMask? Before setting up your wallet, MetaMask wants to know if you want to help contribute to MetaMask development by contributing anonymous data. This is a personal decision for you to make based on your own value system. The data MetaMask wants to collect is anonymous clicks and pageviews.
- Enter your seed phrase and create a new password.
- Proceed to type in your 12 word recovery phrase. Any typos, misspellings, or typing the words in the incorrect order will invalidate the process and you will have to start over
- Create a secure password! MetaMask does not have 2FA, so creating a secure password is very important
- Make your password unique, do not reuse an old password
- Consider using a passphrase instead, a sequence of 4 or more random words
- Consider using a password generator and manager, like Bitwarden
- Setup a time frame to rotate to a new password
- Congratulations! Your wallet has been created and is ready to be used. Get ready to explore the world of Ethereum. MetaMask is more than just a wallet - it's your portal to interact with apps and smart-contracts built on Ethereum. Your MetaMask wallet can store, send, and receive any token on the Ethereum blockchain.
- Read over the advice given on the Congratulations screen and click `All Done` when you are ready to start using MetaMask.
Recommended Action: do you have a safe backup of your seed phrase? Your seed phrase is the only way to restore access to your funds if you lose access to your wallet. Review Section 5. Securely Backup Seed Phrase of this guide for compiled information on best practices for secure seed phrase backups.
Where can you read more about MetaMask?
In the world of cryptocurrency, knowledge is your best friend.
Crypto Wallet providers will almost always have their own user documentation, and sometimes they may even have a user community where you can ask questions.
Check out these resources about MetaMask Wallets:
Information about best practices on the topic of security can be scattered all over the internet. We work hard to distill the best practices into one place for you.
Check out these resources about securing digital wallets:
- Benefits of using an encrypted digital vault, like Vault12
- How to back up a seed phrase on paper
- All about RNG's - Random Number Generators and why they are important
Ethereum is home to a rapidly growing ecosystem of dApps, smart contracts, communities, and more.
Check out these resources about Ethereum:
Advanced
Managing digital assets like cryptocurrencies can be complex, especially when it comes to inheritance.
View all articlesMoveTheNeedleNews: Vault12 Releases Open-Source Capacitor Plugin for Quantum-Safe Data Storage
Move The Needle News
Shamir's Secret Sharing (SSS) for Quantum-Safe Data Storage
How does Shamir's Secret Sharing (SSS) provide you with Quantum-safe data protection?
Quantum Supremacy: Is it a real threat?
What is Quantum supremacy and should I be worried?
What Is a Self-Sovereign Identity?
Personal control over our online personas has given rise to the philosophy of self-sovereign identity (SSI). In essence, a person who has an SSI has sole ownership of their digital and analog identities and controls how their data is viewed or shared.